AMI-Enterprise
description
Transcript of AMI-Enterprise

AMI-Enterprise
Use Case Team Status
Kay Stefferud
Columbus OH, July 14 2009, Hosted by AEP

Overview
• Purpose: Develop Use Cases and Functional Requirements for AMI-ENT
• Group has been meeting regularly since late Oct 2008
• Face to face meetings in November, December 2008, and January, April, July 2009
Timeframe • October 2008 Use case development begins• February 2009 Use case development complete• March 2009 Functional requirements complete• April 2009 Present use cases and functional requirements• July 2009 Propose ratification of version 1.0• ? 2010 Complete AMI ENT use case unification

Use Case Examples
The DR solution shall manage demand resources. The DR solution shall communicate with organizations that manage the grid.The DR solution shall provide for participation of independent third party electric distributors.
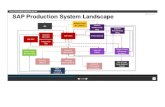
uc Primary Use Cases
Prov ision Demand Response Equipment
Manage DR Customer
Add DR Dev ice Remov e DR Dev iceRead DR Dev ice
InformationUpdate DR Dev ice
«include»
«include»
«include»
«include»
«include»

Breakout Session Topics
• Outage Management use cases– Business Process Models (BPM) – Existing use case status – Diagram using EA
• Incorporate recent comments– Arizona Public Service Company
• Scope AMI ENT use cases– Plans to incorporate existing use cases
• Stakeholders for EA model• Incorporation of security requirements• Barriers to use and incorporation

Security Requirements
• Defined by AMI-SEC group• Included by reference in AMI-ENT requirements• Concern: How to implement security
– Leverage industry group expertise (CERT, SANS, CISSP)
– Use Secure Coding best practices (threat model with mitigations, secure coding standards, secure design patterns, training/certification, etc.) Secure Coding UCA 2009.pptx
– Advanced: Critical Information Protection, Anti-Tamper