ETM Q3 2010 Issue
-
Upload
enterprisemanagement360 -
Category
Documents
-
view
241 -
download
0
Transcript of ETM Q3 2010 Issue
-
8/9/2019 ETM Q3 2010 Issue
1/44
-
8/9/2019 ETM Q3 2010 Issue
2/44
-
8/9/2019 ETM Q3 2010 Issue
3/44
TM CONTENTS PAGE
11Editor andcontributors page
13Industry snapshot
15Professional prole
122Events and features
16 GRCStep by step
In the last few years, GRC has emerged as the
meeting point of eorts to ensure not only
compliance with regulatory requirements, but
a responsible approach to the management of
the enterprise risk that underlies regulatory
demands. SCO CWFORD(ENTERPRISE MANAGEMENT
ASSOCIATES) talks with LUCIO DERISI (MEGA INTERNATIONAL)and LUC BNDTS (BWISE), twoexperts directly involved in helping organizations
shape their GRC strategy.
26 e back o ce means
businessNDY BSCHE (GENESYS)and ETMS ALI KLAVER explore how
companies are applying best practices from the
contact center to the back o ce to improve
e ciencies and meet service levels, all while
reducing cost.
28Pure logic
How can businesses beer operate by
identifying and capturing dened logic and
repeatable rules? DANA GARDNER(INTERBOR SOLUTIONS)discusses business rules management (BRM),
and explores the value of businesses being agile
in a safe way. He is joined byDON GRIEST(FICO), RIK CHOMKO (INRULE
TECHNOLOGY) and BRESTINEMAN (IBM).
38 e key to success
As cloud computing takes a stronger hold on
the IT industry, organizations must realize
that there is a another factor that will ensure
its success. MARTIN KUPPINGER(KUPPINGER COLE)writes about theimportance of serv ice management.
40 Smooth transition
Public versus private cloud computing is one of
the hoest topics in IT at the moment, but theres
still a lot of confusion around its adoption
which has been higher than anyone expected.
STEVE BSEN (ENTERPRISEMANAGEMENT ASSOCIATES)talks with DENIS MARTIN andBROOKS BORCHERDING(NAVISITE) about the scope and transitionof cloud computing.
46 Transforming business
ETMS ALI KLAVER interviews DEEPAK
JAIN (WIPRO) about enabling business growth
through IT infrastructure transformation.
50Actionable IntelligenceDR. ANTON A. CHUVAKIN talksabout the usability and integration of security
information and event management (SIEM)
and touches on log management with the added
benet of three industry experts; MICHAELLELAND (NITROSECURITY),
A.N. ANANTH (PRISMMICROSYSTEMS)and DEBBIEUMBACH (RSA, THE SECURITYDIVISION OF EMC).
62 Create your own app
factoryETMS ALI KLAVER chats toEDDY PAUWELS (SERENASOFTWARE) about business process-driven application lifecycle management and
how they link to each other, as well as how
businesses can benet from such a strategy.
Contents
-
8/9/2019 ETM Q3 2010 Issue
4/44
116One at a time
Enterprise search and subsequent workow ha
long been confused with compliance and polic
for archiving. Information governance strategie
reset thinking in this area by establishing clear
use cases for accessing information versus thos
that enable retention. SIMON TAYLOR(COMMVAULT) takes ETMS ALIKLAVER through the dierent faces of
enterprise search.
CONTENTS PAGE
Contents
68 e pros and cons of
cloudLAU DIDIO (ITIC) describes
what to watch for if youre considering making
the jump to cloud computing. She suggests its
denitely a benet, as long as youve done your
research and its done right.
72 A marriage of sorts
MIKE ATWOOD (HORSES FORSOURCES) moderates a panel discussionon IT outsourcing touching on transformation,
the cloud and some fantastic case studies with
the help ofCHUCK VERMILLION(ONENECK IT SERVICES) andRINE BRUNET (STERIA).
84 SIEM satisfaction
One of the most ignored benets of security
information and event management technology
is using SIEM technology to improve overall
IT operations.A. N. ANANTH andSTEVE LAFFERTY (PRISMMICROSYSTEMS) talk to ETMS ALIKLAVER about how improved operations is
seldom given much aention but might well
provide the most tangible cost justication.
88 A question of semantics
ETMS ALI KLAVER talks with DR. THY
DAHLGREN (COGNITIONTECHNOLOGIES)about an innovativeapproach to meaning-based text processing
technology. Among a discussion on market trends
and the boom line, its clear that Cognition is at the
forefront of searchnow and into the future.
92 Seven reasons
PAUL BURNS (NEOVISE) shareswith ETM why every CIO must embrace Service
Level Management as a way to transform the IT
organization.
94 Moving with the times
ETMS ALI KLAVER talks to
PSHANTH SHEY(METRICSTREAM) aboutmanaging enterprise GRC programs in global
organizations, and how to realize the benets that
can stem from successful implementation.
100Business and ITside by side
DANA GARDNER(INTERBOR SOLUTIONS)moderates a discussion on the productivity
benets and future of business process
management with the help ofMARKTABER (ACTIVE ENDPOINTS),DR. ANGEL DIAZ (IBM) andSAMIR GULATI (APPIANCORPOTION). is expert panelexamines BPM and explores what it delivers to
enterprises in terms of productivity and agility.
110Archiving on demand
MARTIN KUPPINGER(KUPPINGER COLE) talks to AstarosERIC BEGOC about mail archiving, how its
changing, and what to expect in the future.
112Open innovation
With the rise and embrace of social networking
and soware you could be forgiven for
thinking that were at the height of innovation.
MAHEW LEES (PATRICIASEYBOLD GROUP) tells us how socialtechnology can make innovation more than
just a word.
-
8/9/2019 ETM Q3 2010 Issue
5/44
EDITORS PAGE ETM CONTRIBU
C o n t r i b u t o r s
P a u l B u r n sP r e s i d e n t a n d F o u n d e r
Ne o v i se
L a u r a D i D i oP r i n c i p a l A n a l y s t
I n f o r m a t i o n T e c h n o l o g y I n t e l l i g e n c e C o r p ( I T I
M a r t i n K u p p i n g e r
Senior Partner and Founder Kuppinger Cole
M a t t h e w L e e sSenior Contributing Editor
Patricia Seybold Group
HeadquartersInformed Market Intelligence (IMI) Ltd
Farringdon House, 105-107 Farringdon Road
London, EC1R 3BU, United Kingdom
+44 207 148 4444
New York68 Jay Street, Suite #201, Brooklyn, NY 11201, USA
+1 718 710 4876
Head in the cloudsIt appears the IT world is slowly but surely opening up a realm of possibilities forbusinesses globally. While we in the IT sphere have known this for a while, its just
coming to the attention of businesses looking at their SIEM solutions, their business
process management, and especially ROI.
An IT department stuck in the bowels of the building is quickly becoming a thing
of the past as business decision-makers realize that creative collaboration is the way to
go. Now, IT and management are rubbing shouldersliterallyand working across the
gamut of business applications to find ways to grow, collaborate and innovate.
Our Q3 issue is a breath of fresh air and packed full of the answers to your questions.
Why not start with our business rules management and business process management
podcasts (pages 28 and 100 respectively), as one of our favourite moderators, Dana
Gardner, guides you through the essentials with the help of
industry leaders.
Matthew Lees from the Patricia Seybold Group tells us how social technology can
make innovation more than just a word (page 112), while I have an interesting chat
with Dr. Kathy Dahlgren from Cognition Technologies about semantic searchcertainly
one to get the brain working (see page 88).
There is plenty more to read in this issue of ETM, and hopefully in these pages youll
find the perfect solution to your IT problems. And dont forget, there are a wide range of
podcasts to enjoy onwww.globaletm.com
Thank you for reading, and if you would like to contribute to any future issues of
ETM, please feel free to contact me via email at [email protected]
Ali Klaver
Managing Editor
F o u n d e r / P u b l i s h e rA m i r N i k a e i n
M a n a g i n g E d i t o r A l i K lav e r
C r e a t i v e D i r e c t o rA r i e l L i u
I n t e r n D e s i g n e rJ e f f C e r i e l l o
We b D e v e l op e rV i n c e n z o G a m b i n o
P o d c a s t / S o u n d E d i t o rM a r k K e n d r i c k
A s s o c i a t e E d i t o r s M a r y W r i g h t
H e l e n a S t a w i c k iL e e L i a n L o n g
A c c o u n t E x e c u t i v e s J o e M i r a n da
S a n d i n o S u r e s hA i c h a G u l t e k i n
N o r t h A m e r i c a n A c c o u n t E x e c u t i v e sF a r r a h T u t t l e
Y e s s i t A r o c h o
M a r k e t i n g E x e c u t i v eA l e x a n d r o s T h e m i s t o s
Enterprise Technology Managementis published by Informed Market Intelligence
How to contact the editorWe welcome your letters, questions, comments, co mplaints and compliments.
Please send them toInformed Market Intelligence, marked to the Editor,Farringdon House, 105-107 Farringdon Road, Lo ndon, EC1R 3BU, United Kingdomor email [email protected]
PR submissionsAll submissions for editorial consideration should be emailed to [email protected]
ReprintsFor reprints of articles published in ETM magazine, contact [email protected] material copyright Informed Market Intelligence
This publication may not be reproduced or transmitted in any form in whole or part without the written express consent ofthe publisher.
-
8/9/2019 ETM Q3 2010 Issue
6/44
INDUSTRY NEWS
GROWTH IN
RUSSIA
Industry snapshot
Groteck Business Media reports that the
information security market in Russia wasable to develop during the economic crisis.
Almost all segments grew in 2008, kept growing
in 2009, and they anticipate growth in the
2010-2011 period. e main drivers were
requirements towards protecting personal data
and information in public authorities. In the
next two years they expect the implementation
of electronic document management and the
protection of mobile devices to be big growth
areas.
www.groteck.com
Kenya is registering all mobile phone numbers
in a bit to cut crime. Kidnappers oen useunregistered mobile numbers to text ransom
demands and its expected most people will
support the move to make life more di cult
for criminals. Users must supply ID and proof
of address before they get a number, and any
numbers still unregistered as of the end of July
will be disconnected. Tanzania is also involved in
a similar process.
CALLING KENYA
IBM PROBED
e European Commission has launched two
separate competition inquiries to discover
whether IBM has abused its position in the
mainframe market following complaints by two
soware makers. e inquiries will examine
whether IBM prevented competitors from
operating freely and will look at their relations
with maintenance suppliers. IBM says the
inquiries have no merit.
NEW LICENSING
OPTIONS
It looks like the Microso O ce license
per device concept has had a rethink. Withthe increasingly mobile workforce, and as
virtualization comes to the fore, Microso has
had to clarify its SA policies. Since July, users o
a PC with an O ce license have rights to O c
2010 Web Apps from PCs or external devices,
but companies will need to host the O ce
Web Apps on either SharePoint Server 2010 or
SharePoint Foundation Server 2010.
www.microso.com
Google has trumped Bing in a deal to providesearch results and related advertising to Yahoo
Japan. e deal will see Google provide search
capabilities to 90% of the PC market and roughly
half of the mobile web market. is is a further
boost for Googles Japanese operation. On
another note, the China/Google row continues...
JAPAN EMBRACESGOOGLE
PENTAGON HUNTSWIKILEAKS
e Pentagon is still on the hunt for the source
who leaked more than 90,000 classied US
military documents. Bradley Manning, the
22-year-old Army intelligence o cer currently
under arrest for leaking a variety of classied
documents, databases and videos to Wikileaks,
has not been ruled out as a suspect. Although
the leaks reveal past actions, the details are
considered nonetheless damaging.
VIRUS TARGETSINDUSTRY
Siemens is tackling a virus that specically targ
computers used to manage large-scale industria
control systems used by manufacturing and
utility companies. Although this could be one
the biggest malicious soware threats in recent
years in the form of industrial espionage, Sieme
is actively looking to counteract it. eyve
already discovered that its best to leave current
passwords unchanged and to refrain from using
USB keys.
-
8/9/2019 ETM Q3 2010 Issue
7/44
hp://www.GlobalETM.com
XECUTIVE PANEL GOVERNANCE, RISK AND COMPLIANCE
6
In the last few years, GRC has emerged as the meeting point of efforts to ensure not only
compliance with regulatory requirements, but a responsible approach to the management
of the enterprise risk that underlies regulatory demands. SCOTT CRAWFORD
(ENTERPRISEMANAGEMENT ASSOCIATES) talks with LUCIO DE RISI
(MEGA INTERNATIONAL) and LUC BRANDTS (BWISE), two expertsdirectly involved in helping organizations shape their GRC strategy.
GRCStep by step
-
8/9/2019 ETM Q3 2010 Issue
8/44
GOVERNANCE, RISK AND COMPLIANCE EXECUTIVE P
SC: THERE HAS BEEN A LOT OF TALK
ABOUT GRC OVER THE PAST FEW
YEARS, AND TO MANY IT SOUNDS
QUITE BROAD AND UNDERSTANDABLY
SO, CONSIDERING THE BREADTH OF
WHAT IS INCLUDED TYPICALLY IN A
GRC PROGM. LUC, HOW DO YOU
AND BWISE DEFINE GRC?
LB:We feel that there is a need tointegrate all the dierent levels of defence in
the organization. So with the rst level we want
to help businesses to responsibly implement
policies and procedures, report incidents,
implement controls and so on.
is is supported by a second level
of defence, whether its risk management
compliance or quality management
departments, and thats where a big
convergence eort is taking placetrying to
integrate all the dierent risk languages into
one. We see GRC as oen being mistaken for
just that second level of defence.
eres also more to it, a third level of
defence, where internal audit does their
independent review of that information, trying
to leverage the data thats out there as much as
possible.
Finally, theres a fourth level of defence, the
external auditor and regulators, who hopefully
also take that information into account.
What were trying to establish, and what
organizations are trying to get across, is that all
these dierent entities, departments and views
within an organization need to be speaking a
single risk language. eres a strong element
of risk and a very important component of
compliance that is being governed by the
processes that help these four levels of defence
to cooperate.
LD:Based on customer experience, Ithink that GRC doesnt mean the same thing for
everybodyjust the initiatives today cover a
large spectrum of requirements.
An analysts denition would call GRC a
set of policies, processes, methodologies andtools that a company implements to phase the
increasing pressure of internal and external
regulation, and to guarantee that all conditions
are met to achieve business goals.
In the beginning, GRC was formed to
basically put together siloed initiatives within
one global approach, then the acronym of GRC
was born. Today, that model of GRC is more
about implementing a holistic approach to
target rst business performance, and then x
the technical problems within each department.
SC: THAT LINES UP VERY WELL
WITH WHAT WEVE SEEN AT EMA.
THERES DEFINITELY A VERY LARGE
ELEMENT OF RISK, AND LUCIO, THE
ISSUE YOU BRING UP DOES REVOLVE
TO A CERTAIN EXTENT AROUND
GOVERNANCE.
ORGANIZATIONS THAT WE WOULD
QUALIFY AS HIGH PERFORMERS H AVEPLACED A GREAT DEAL OF EMPHASIS
ON SEING THE TONE AT THE TOP,
IF YOU WILL, AND THE SUPPORT OF
SENIOR MANAGEMENT IN TERMS OF
DEFINING PRIORITIES, STTEGY AND
A TRULY RESPONSIBLE APPROACH TO
ENTERPRISE GOVERNANCE.
ONE OF THE THINGS EVIDENT
FROM OUR RESEARCH HAS BEEN NOT
JUST SEING THE TONE AT THE TOP
BUT SENIOR MA NAGEMENT SUPPORT
FOR GRC EFFORTS. ITS CRITICAL, NOT
JUST FOR LEADING GOVERNANCE
INITIATIVES, BUT FOR IMPLEMENTING
RISK MANAGEMENT TACTICSAND
THAT INCLUDES MEASURES SUCH AS
ENFORCEMENT, FOR EXAMPLE.
LUCIO, WHAT ARE SOME OF THE
THINGS THAT YOU THINK HELPS
ORGANIZATIONS SUCCEED IN
DEFINING EFFECTIVE GOVERNANCE?
LD:First, Id like to enhance the kindof dichotomy in how to approach GRC in
initiatives, and then position the sponsorship
from top managers with respect to these two
dierent approaches. ese two approaches are
not opposed, but complementary.
One is what you would call approach based
on controls, and the second is based on business
improvement. e role of senior management is
dierent in these two dierent cases.
Let me clarify what I mean. In some cases,
the companies need to apply what I call the
control-based approach. For example, you
need to respect US law about not exporting to
some countries, or you have to guarantee that
you provide the appropriate data to the stockexchange. If youre in Europe you know that you
cannot provide any advertising, or you must be
sure that youre not referring to smoking, for
instance.
In all these cases, which are basically
maers of respecting the law and other strict
rules, I think that the control-based approach is
the one that companies must apply, even if its
not the only one.
e second one that I mentioned, which I
call the business improvement-based approach,
-
8/9/2019 ETM Q3 2010 Issue
9/44
RandyBrasche(Genesys)and ETMS ALI K LAVER explohow companies are applying be
practices from the contact centeto the back o ce to improvee ciencies and meet service levall while reducing cost.
Usually a piece of work goes into a queue,
just like a telephone call would go into a
queue, then the contact center, usually the
back office person, has to pull that piece
of work out of the queue and they have to
validate it in terms of actually doing the work.
Then they have to go one step further and
execute the work.
What weve found is that the process of
nding the piece of work and pulling it out of
the queue usually takes about three minutes or
so, and thats tremendously ine cient when
youre talking about thousands and thousands
of work items in the back o ce every year.
Imagine, for example in the same contact
center, if someone were to go ahead and call in,
and an agent looked at all the calls in the queue
and saw that a person wanted to change theiraccount information. ey could then pull it
out and take care of that customer very quickly
and easily.
Imagine how inefficient and frustrating
it would be for the c ustomer on the telephone
to wait for an extended period of time, or get
put through to the wrong department, when
all they wanted was the change their account
informationthese are the exact same
things that are happening in the back office
today.
AK: THATS A GREAT EXAMPLECAN
YOU PERHAPS TAKE US THROUGH A
FEW MORE?
RB:I have a few other great examples.
Typically, when you think of the back
o ce, there are usual ly some penalties or
costs associated with it. If you think about
provisioning a service like your telephone, or
doing a credit card dispute, theres usually a
service level associated with that.
Say that we took, for example, one of our
customers who is a large telecommunications
company. When they dont provision a
telephone serv ice from the back o ce, they
have to pay nes to the front o ce, the contact
center and to the customer.
Imagine if all this work is siing thereand they might have two pilesone might
be something as simple as just changing
account information, and the other pile is for
provisioning a new serviceobviously you
want to go in and prioritize the provisions on
your services to ensure that you dont have to
pay a ne.
Similarly, one of our customers tries to
move ahead quickly and set up new credit card
account that they receive from the web, but
they get stuck in the back o ce and they dont
get prioritized. ese prospects actually end
EAD TO HEAD BUSINESS PROCESS MANAGEMENT
The
Back Office
means Business
AK: NDY, WHY DOES THE BACK
OFFICE WANT TO EMULATE THE
CONTACT CENTER OR FRONT OFFICE?
RB:Well, if you think of the contact
centre, they ve had years to become e cient. e
calls that go into a contact centre get prioritized,
routed, sent to the right agent, and so on.
When you look at the back o ce, they
sometimes have six times the amount of
workers, three to ve times the costs, and a lot
of the time theyre very ine cient.
Perhaps you had to submit an insurance
claim and normally you might be very happy
with your experience of the contact center
submiing that request, but when it came to
actually being processed it gets delayed.
And in terms of cost, especially since itsthree to ve times the cost in the back o ce,
thats a lot of money companies are spending
mostly on individuals in the back o ce, cherry
picking work, not taking the right items, or the
work not being aligned to the right person.
AK: WHAT ARE YOU FINDING IS THE
SOURCE OF THESE INEFFICIENCIES?
RB: ere are usually a couple of stepsthat are taken in the back o ce when a work
item is processed.
6
-
8/9/2019 ETM Q3 2010 Issue
10/44
up geing credit cards from other companies
because they werent processed appropriately
or quickly enough in the back o ce. So thats a
case of lost revenue.
Both cases are from a service level
agreement perspective, and at times you may
have to pay nes for not meeting them. From
the other credit card example, this is lost
revenue and lost customers that you could have
had because you were very ine cient in theback o ce.
AK: WHAT ARE SOME OF THE EXISTING
TECHNOLOGIES IN THE BACK OFFICE
THAT COULD BENEFIT FROM THESE
NEW EFFICIENCIES?
RB: ere are a lot of new technologiesthat, if you think about it, any process or work
based item can use to their advantage.
e simplest might be a fax server, and
Ill give you an example in a second. Another
one might be a service request system, such as
a Remedy, trouble ticketing system, a Siebel
system or SAP system, and all the way up to
the more complex systems such as a business
process management system.
e simplest example I could give is that
most people can relate to a fax service. I was
using an airline several years ago and they
missed crediting me for 5000 miles .ey said to
fax my request in and that it would be rectied.
So I did that and nothing happened, even when
I faxed it again. I ended up geing so frustrated
that I switched airlines.
Had they actually known my status as a gold
customer, looked at the fax, and aached a high
priority tag to it and sent it to the right agent,
along with an SLA associated with it saying that
I needed to be responded to within 24 hours,
then I might not have ended up leaving and
going to another airline.
Im now a happy customer at the airline
I switched to, so thats a great example of a
technology that could actually benet from this
type of a process.
AK: THE BOOM LINE IS STILL SUCHAN IMPORTANT ASPECT OF DAILY
BUSINESS LIFE NDY, SO CAN YOU
TELL ME WHAT THE TYPICAL ROI AND
SAVINGS ARE?
RB: Its prey dramatic, when you thinkabout it, if you prioritize the work items based
upon value and send them to the right person
in the back o ce just like you would with a
telephone call in the front o ce and the contact
center. Weve seen a dramatic improvement of
about 15-25% e ciencies in the back o ce.
Ill use another real-time
example. We did a pilot with
a customer in Australia and
they typically had a problem
with their nine to ve work
day and the fact that, at
ve oclock when work was
done, they still had a lot of
unnished work and items
that werent processed thatwere high priority.
Once we worked with them, implementing
this process, their nine to ve work day went
from nine oclock until two oclock, so they had
three extra hours to re-provision these workers
to do other items that could actually benet
from the next days worth of work.
AK: THATS ANOTHER FANTASTIC
EXAMPLE NDY. WHAT TYPES OF
COMPANIES WOULD BENEFIT?
RB: e logical ones are obviously themost paper process-intensive companies suchas insurance companies that have to deal with
claims, nancial services and so forth. But there
are a lot of other companies that you might not
even think about.
ese are companies that have to process
leads that they get from their websites, or other
companies that have some sort of government
regulation and service levels associated with
themto use the credit card example, when
you have to go ahead and issue your credit card
disputethen that has to be fullled within a
certain period of time.
So if you think about any company across
the board and any vertical industry, theres
always some sort of business process associated
in the back o ce, so any company could really
benet from this.
AK: YOURE TALKING ABOUT
CATERING ACROSS A WIDE NGE OF
INDUSTRIES HERE, AND ESPECIALLY
IN THIS ECONOMIC CLIMATE ITS
ESSENTIAL TO REALLY JUMP ON THES
BACK OFFICE BUSINESS PROCESSES T
ENSURE THAT YOURE GEING THE
BEST POSSIBLE RESULT YOU CAN.
NOW FOR OUR LAST QUESTION, WHA
CAN THOSE COMPANIES LISTENING
TODAY DO TO GET STARTED?
RB: It really requires self assessment asome internal thinking in terms of: What are m
processes? How are they being done? How are
my workers being utilized? What are their ski
sets? How do I determine which items are the
higher business priority? e list can be endle
A lot of companies are doing this back
o ce transformation today and I think it
really becomes an issue of self assessment. You
need to take a close look at what you do in the
back o ce and re-prioritize your resources,
your processes, and also implement new
technologies to ensure that youre becoming
more e cient.
At the end of the day, when youre talking
about six t imes the amount of back o ce
workers at three to ve times the cost, that
translates into a lot of money.
Also, these back o ce processes are being
relied on by the front o ce and the contact
centre, and youre also talking about customer
satisfaction which can result in customer
defection. But if you can keep those customer
happy, then these happy customers are going t
spend more money.
So it really requires self assessment and
looking internally to see where you can
improve.
BUSINESS PROCESS MANAGEMENTHEAD TO
Randy is responsible for driving adoption of Genesys market-
leading customer service and sales solutions. Prior to Genesys, he
was a founding member and director of product marketing at Active
Reasoning, and held marketing and product strategy positions at Cable
and Wireless, Exodus, Oracle, Informix and Liberate Technologies.
Randy is the author of the popularIT Compliance for Dummies
andDynamic Contact Center for Dummiesbooks.
Randy Brasche DIRECTOR OF PRODUCT MARKETING
GENESYS
... these backofficeprocesses are being relieon by the front officeand the contact centre...
-
8/9/2019 ETM Q3 2010 Issue
11/44
-
8/9/2019 ETM Q3 2010 Issue
12/44
BUSINESS RULES MANAGEMENT EXECUTIVE P
DGARDNER: DON, TELL ME A LILE
BIT ABOUT YOUR HISTORY. HOW IS IT
THAT BUSINESS RULES MANAGEMENT
PLAYS AN IMPORTANT ROLE AT YOUR
COMPANY?
DGriest:FICO is probably best
known for FICO score which is used in credit
decisions, when you get a credit card or apply
for a loan for a house. Its been around 50 years
now and started with a couple of statisticians,
Bill Fair and Earl Isaac.
ey came up with a way of using data
analytics to improve decisions. ey quickly
found out that giving people a good credit score
wasnt enough and that they needed to apply
those decisions in making oers on products
and making decisions about the credit risk.
So they started building applications for
banking and then eventually insurance, retail,
healthcare and other industries to help them
make decisions informed both by the best
practices that were in the policies, but and by
analytics including predictive analytics, predictive
modelling, simulation and optimization.
Today, we sell both applications and then
tools underneath that help us build those
applicationsbusiness roles management being
a critical one of those.
DGARDNER: WHATS CHANGING?
WHAT MAKES BUSINESS RULES
MANAGEMENT SO IMPORTANT TODAY?DO YOU AGREE THAT COMPLEXITY IS
SPINNING OUT OF CONTROL?
DGriest:I agree that therehave been a number of changes in the market.
Obviously, the recent economy changes have
put a lot of pressure on e ciency and doing
more with less. is means you need to make
faster, cheaper decisions, and you need to be
able to make changes to those decisions faster.
At the same time, weve got more regulatory
pressures coming in not just in banking but also
in healthcare as well. at is increasing the need
for decision-making with great transparency
and also being able to minimize the impact to
the overall return on the company.
If you look at retail, its exploding in
terms of what the web has done and in terms
of consumer expectations about how many
combinations of dierent products are available
and greater competitive pressure to get the
right price point and the right oer to the right
customerand actually still make money
doing it.
DGARDNER: IM G OING TO GUESS
THAT AT FICO YOU OFFER SERVICES
THAT AMOUNT TO BUSINESS RULES
MANAGEMENT, BUT I BET YOU
ALSO EMPLOY IT WITHIN YOUR
ORGANIZATION. SO YOURE A
BUSINESS RULES CONSUMER AS WELL
AS USER?
DGriest:Denitely. FICOis known for its scores, so that uses rules
management to implement those scores. ey
create formulas that take information at the
credit bureaus and apply scoring techniques to
create a score. We then have applications that
our customers use in origination.
So when you ll out the loan it actually
helps to walk that through the process
a culmination of normal business process ow
but also business rules being at the centre ofthat. So, yes, its used throughout the company.
DGARDNER: RIK AT INRULE
TECHNOLOGY, TELL US A LILE
BIT ABOUT WHAT YOU DO, WHAT
YOU PROVIDE, AND HOW YOU SEE
THE LANDSCAPE FOR BUSINESS
RULES MANAGEMENT SHIFTING OR
ADVANCING?
RC:InRule was started about eightyears ago and we decided, at the time the .NET
framework was almost brand new, to focus on
rule technology for that particular framework
and platform.
Weve been doing that ever since and
really pushing harder to be a solution for the
.NET platform that provides the authoring,
management, storage and execution of the rul
applied on that platform.
I think what Ive seen over the last few
years has been changing a lile bit more than
what was there before. ere are always the to
three industries that you would apply busines
rules toinsurance, nancial services and
healthcareand while those are still going
strong today there seems to be an uptake in a l
of other industry sectors that might be lookin
to use rules, outside those top three.
For example, take the entertainment
industry. One of our clients is actually using
rules to manage their project plans to enforce
consistency and promote realistic planning fo
large scale video production.
So its kind of interesting where were seei
this use of rules grow out from perhaps what
people would traditionally apply rules to, and
trying to branch into other industries.
DGARDNER: BRE STINEMAN AT IBM
HOW DO YOU SEE YOUR BRM MARKET
SHIFTING OR PERHAPS GROWING IN
THE NEXT FEW YEARS?
BS: Im sure most people have a fairlygood idea of who IBM is in terms of the variosoware, hardware and services that we provi
In terms of business rules management, our
oering came from an acquisition of a compan
called ILOG that occurred in 2009.
ILOG has a long history, going back
20 years, in a variety of dierent types of
decision technologiesboth from a business
rules standpoint as well as optimization
and visualization technologies, all of which
were used to help organizations make beer
decisions for various parts of their businesses.
How can business better operate by identifying and capturing defined logic and
repeatable rules? DANA GARDNER (INTERARBOR SOLUTIONS)
discusses business rules management (BRM) and explores the value of businesses
being agile in a safe way. He is joined byDON GRIEST (FICO), RIK
CHOMKO (INRULE TECHNOLOGY) and BRETT STINEMAN(IBM).
-
8/9/2019 ETM Q3 2010 Issue
13/44
ITS NOT ABOUT IAM FOR THE CLOUD
Given that, we have to redene our IAM
strategies. We have to think about how to
manage everything consistently. at excludes
approaches that run externally and only manage
the external services. IAM in the cloud only
for the cloud is contradictory to the target of
managing everything consistently. us, we need
to expand what we have (or should have) in IAM,
and access governance to support our future IT
infrastructure.
Approaches that arent focused on supporting
a hybrid cloud environment can only be tactical
approaches, if at all. On the other hand, internally
focused tools have to expand their reach to
external services.
ONE ITONE MANAGEMENT
It obviously doesnt make any sense to deal with
external services that dier with internal services.
at will make management inconsistent,
redundant and error-prone, plus, it will inhibit
the exible change from internal to external
services and back.
Consuming external services is one element
of the overall IT service provisioning. And it is, by
the way, an element which is in place in virtually
any organization. ink about web hosting,
web conferencing and many other applications
which are frequently provided by external service
providers.
e quintessence of cloud computing is that
it standardizes the service management across
NALYST FEATURE SERVICE MANAGEMENT IN THE CLOUD
As cloud computing takes a stronger hold on the IT industry, organizationsmust realize that there is a another factor that will ensure its success.MARTIN KUPPINGER (KUPPINGER COLE)writes about the importance of service management.
Thekeytosuccess
Cloud computing is the hype topic in IT. And without a doubt, cloud computing is about a fundamental paradigm shi in IT.
However, it is not so much about procuring external services. It is about the way IT services are produced, procured and managed
internally as well as externally. at is where service management comes into play.
Service management, from the Kuppinger Cole perspective, is the key success factor for cloud computing. When talking about cloud
computing, it s something dierent than the cloud.
First of all, there are several clouds, in the sense of environments which deliver IT services. ese might be internal or external; they might be private or
public; but all of them provide IT services at dierent levels of granularity. ese levels range from granular web services to coarse-grain services like complete
application environments and many SaaS (Soware as a Service) approaches.
Cloud computing, on the other hand, is about selecting, purchasing/requesting, orchestrating and managing these services. e management spans the
entire range from technical aspects to auditing and accounting.
While the services might be delivered by many clouds, there has to be one consistent management approach. is approach has to cover internal and
external IT services. It is about one view on the IT, regardless of the service provider (or cloud, to use that term).
8
-
8/9/2019 ETM Q3 2010 Issue
14/44
all types of services and thus allows you the
exibility to choose services from dierent
providers. Another eect is that internal
IT services have to become standardized
and (from a cost perspective) produced
e cientlyinternal IT ser vice production
should signicantly benet from that approach
by becoming more industrialized and
automated.
FOCUS BEYOND SERVICE
FUNCTIONALITY
To fulll the security and governance
requirements, service management has to
focus not only on the functional aspects (and,
like frequently seen today when looking at the
cloud, costs).
For each service there has to be
governance requirements, including aspects
like encryption of data, requirements for
privileged access management, allowed
locations for processing and storing the data,
and many more.
When describing services and dening
the service requirements, there has to be a
standardized set of such requirements to ensure
that these aspects are considered when selecting
the (internal or external) service provider.
e most appropriate provider isnt the one
with the most advanced functionality or the
lowest costas long as he doesnt meet the
governance requirements.
BUSINESS SERVICE MANAGEMENT
When talking about service management in thecontext of cloud computing, it becomes obvious
that there are multiple layers of services. Within
IT services there is a range from single web
services at the application level to complex SaaS
applications. However, that can be managed
with a consistent approach because the
fundamental principles of service management
apply to any level of service.
Beyond the IT perspective, there has to be
business service management as well. Business
service management is, in contrast to todays
vendor marketing, about having descriptions
from the business perspective of their
requirements to IT.
It is not about availability management
for business processes or something similar, it
is about mapping the required IT services to a
business requirementfor example, mapping
storage and archiving services, information
rights management and other services to therequirement, that contracts are handled in a
dened way.
One element within such a business
service management is providing the input for
the governance requirements of IT services.
ese requirements typically are derived from
business requirements, including regulatory
compliance.
ERP FOR IT
An interesting opportunity within this approach
of consequently using service management
paradigms at all levels is that the ability for
accounting will signicantly increase. Once
everything is understood as a well-dened
service, it is relatively easy to have a price tag on
these services.
at, in consequence, will allow you to
do much beer resource planning and to
predict costs of new business services (eg. new
requirements to the IT) much more reliably
than before.
In other words: service management
is the foundation for an ERP for IT, the
ERP application which is still missing today.
However, todays service management
applications arent an ERP for IT, even while
some vendors tend to start telling this to their
customers.
FOCUS ON SERVICE MANAGEMEN TAND SUCCEED WITH CLOUD
COMPUTING
Looking at cloud computing and service
management, it is obvious that these two thin
cant be separated. Service management is the
foundation for successful cloud computing.
And cloud computing will drive the service
management initiatives in organizations and
will require the internal IT to standardize
their services.
e most important reason for this is that
otherwise the internal IT cant prove that they
are providing the most appropriate servicesbecause they cant directly compare with
cloud services. Only with complete service
requirements, including the governance aspec
can internal IT can validate that their service
procurement suits the needs of the business
beer than the (sometimes) cheaper external
service.
It will absolutely change the way the
internal IT is workingbut it is the only
opportunity the internal IT has: standardize
services, optimize the service production,
and be beer in meeting all the service
requirements.
From an overall IT perspective, service
management is key to success in cloud
computing as well because it is the prerequisit
for being able to exibly switch between
internal and external service providers and
back.
SERVICE MANAGEMENT IN THE CLOUDANALYST FEA
Martin established Kuppinger Cole, an independent analyst company, in
2004. As founder and senior partner he provides thought leadership on
topics such as identity and access management, cloud computing and IT
service management.
Martin is the author of more than 50 IT-related books, as well as
being a widely-read columnist and author of technical articles and reviews
in some of the most prestigious IT magazines in Germany, Austria and
Switzerland. He is also a well-known speaker and moderator at seminars
and congresses.
Martin Kuppinger |FOUNDER AND SENIOR PARTNER
KUPPINGER COLE
While the services might bedelivered by many clouds,there has to be one consistentmanagement approach.
-
8/9/2019 ETM Q3 2010 Issue
15/44
EAD TO HEAD CLOUD COMPUTING
0
Public versus private cloud computing
is one of the hottest topics in IT at the
moment, but theres still a lot of confu-
sion around its adoptionwhich has
been higher than anyone expected.
STEVE BRASEN(ENTERPRISE MANAGE-MENT ASSOCIATES) talks
with DENIS MARTIN and
BROOKS BORCHERDING(NAVISITE) about the scope ofcloud computing and its transition.
Smoothtransition
hp://www.GlobalETM.com
-
8/9/2019 ETM Q3 2010 Issue
16/44
CLOUD COMPUTING HEAD TO
SB: TODAY WELL BE TALKING ABOUT PUBLIC VERSUS
PRIVATE CLOUD COMPUTING, CERTAINLY A HOT TOPIC
AND ONE AROUND WHICH THERE IS A LOT OF CONFUSION.
I DONT SEEM TO BE ABLE TO PICK UP A TDE MAGAZINE
THESE DAYS WITHOUT SEEING RE PEATED REFERENCES TO
CLOUD.
ACCORDING TO EMA PRIMARY RESEARCH, IN FACT, 11%
OF ALL BUSINESSES HAVE ALREADY ADOPTED SOME FORM
OF CLOUD SERVICES IN ORDER TO ACHIEVE THEIR BUSINESSOBJECTIVES. THIS IS VERY FAST ADOPTION WERE SEEING,
FOR WHAT IS REASONABLY CONSIDERED A FAIRLY NEW
TECHNOLOGY. WEVE PROJECTED THIS TO BE SOMEWHERE
BETWEEN A $4050 BILLION DOLLAR INDUSTRY BY THE END
OF 2011, AND GROWING ROUGHLY TO $160 BILLION BY 2015.
YET WITH ALL THIS PROMISE AND HYPE, ITS SURPRISING
THAT THERE DOESNT SEEM TO BE MUCH CONSENSUS
ON EXACTLY WHAT CLOUD IS AND WHERE THE SCOPE IS,
WHICH LEADS ME TO MY FIRST QUESTIONHOW WOULD
YOU DEFINE THE SCOPE OF CLOUD COMPUTING, AND HOW
DO YOU DIFFERENTIATE PUBLIC AND PRIVATE CLOUD
COMPUTING?
DM:Youre right Steve, there is a lot of confusion in themarket today around cloud. Today well talk about it primarily from an
infrastructure perspective, but even then theres a lot of confusion about
what a public cloud is compared to a private cloud.
In that spectrum from private to public, the consensus dening factor
thats emerging is how many customers are on the cloud. If there is more
than one, its typically dened or put in the bucket of being a public cloud.
If its only one, then its eligible to be qualied as a private cloud.
Even then there are a number of options or gradients along that
spectrum where its not so black and white. For example, NaviSite
offers private hardware where we can put one customer on a piece
of hardware, yet theyre sharing other components of the underlying
infrastructure.
Is that private, or is that public? We think of it as quasi-private and
we think we provide all the benets of a private cloud without any of
the downsides. Its not so cut and dry that there is a single dierentiator
between public and private.
BB:Id like to add to what Denis said and to your initial points,Steve, around rapid adoption.
If you take a step back and consider why cloud has become so
interesting and gathered so much hype, its because it is a true revolution
and a true transformation of the way that companies are consuming IT
resources.
So be it public, private or a hybrid of anywhere in between, I thinkat least in our generation, that weve very rarely seen something of this
magnitude that is changing the fundamental consumption paradigm of IT.
We certainly have experienced that where were based here, in
the enterprise space, but you can see this very rapid consideration of
alternatives to the way that companies are consuming IT resources from
consumers across the enterprise spectrum.
SB: WHAT ARE THE PRIMARY BENEFITS AND CHALLENGES OF
PUBLIC AND PRIVATE CLOUD IMPLEMENTATIONS?
DM:From the public cloud perspective, the biggest benet is theease of access and the ease of on-boarding.
Typically you can get on a public cloud, whether its for compute
and storage or a combination of them, usually within minutes by simply
providing a credit card number and commitment to pay and then your
access is immediately available. So its a very simple on-boarding process.
e challenge on the public cloud, because it is geared for larger grou
of users and for a general usage case and not for specic usage cases, is tha
its geared typically for non-production services with very low service leve
agreement guarantees, and in some cases almost to the point of best eor
type performance.You really dont rely on them for services other than things like
development or some sloppy bursting that you might need, but for today
at least, theyre not geared for the rigors required for producing and
supporting production applications.
Private clouds, on the other hand, inherently have all of the features
required for not only doing high level SLAs, but also providing the
complete infrastructure lifecycle management.
So in the case of public cloud, you might only have the ability to
manage your CPU and the amount of memory, but you dont have contro
over rewalls and load balancers and the other components that are
required to provide the use of the machine that you created, the rewall
rules that you apply to it, the load balancing and so on.
On the private side, since it is fully controlled, you do have the ability
to create and work on the machines, apply rewall rules to them, apply
load balancing as needed, and then expose them from either the back end
network or expose them on the public network space automatically.
Its a much more robust environment for providing a range of services
whether its simply for development and testing, and all the way to the leve
of providing production services with four nines or ve nines availability.
BB:I think a couple of the general benets, be it public or private,the fact that cloud services do have a promise of mitigating the complexity
of IT. So, from a consumer perspective, it is easer to look at this as an
alternative to acquire these resources, be they compute resources, or bethey application on demand or SaaS-type capabilities.
So from both, there is this promise that we can make it much simpler
to consume IT. And on both, I think theres also a promise, be it public or
private, consumer or enterprise, that there will be a reduction in capital
expenditure and an increase in operational e ciency across the spectrum
Where the dierentiation comes between public and private, as Deni
mentioned, is that theyre built to deliver enterprise-type class services
at least, thats the approach that weve taken at NaviSite.
So its taking everything from the quality of the underlying
infrastructure and technology through to everything else that would be
required such as the security standards, the wraparound services that you
would expect, and then the ongoing support.
... a quasi-private
cloud, as an extensionof yourIT environment, is really awin-win onboth sides.
-
8/9/2019 ETM Q3 2010 Issue
17/44
SK THE EXPERT IT INFRASTRUCTURE TRANSFORMATION
AK: CAN YOU GIVE US A BRIEF SUMMARY OF WIPROS
INFSTRUCTURE SERVICES BACKGROUND AND HOW YOU
HELP BUSINESSES SUCCEED?
DJ: Wipro has been oering IT Infrastructure services to its customersfor over 25 years. Our customers are spread across North America, Europe,
Asia Pacic and Middle East geographies. Wipros IT infrastructure business
is US$926 million and contributes 21% of our IT services revenues globally.
Were seeing robust growth in this business and have been ahead of
company growth at 40% CAGR for the last three years. We have seven
datacenters and 17 global command centers including 14 security operations
centers globally. Over 16,000 associates work for this division.
Our growth strategy is to keep on expanding our portfolio and, today,
in our infrastructure services business, we oer end-to-end IT outsourcing
solutions from design and implementation services, managed services, DCoutsourcing including technology transformation, and audits to continually
improve the performance of IT systems.
We also have comprehensive oerings to cater to complete IT security
management services (consult deploy manageaudit). We also have a
strong oering on the Core Telecom networks.
AK: HOW DO YOU HELP BUSINESSES SUCCEED IN THE
CURRENT MARKET?
DJ: Our approach is to partner with our customers and look at longterm relationships. Our domain knowledge helps us understand the clients
business better, and then propose solutions more aligned to business.
Unlike many Indian IT companies focused on remote infrastructure
management and cost arbitrage, we also focus on improving the business
KPIs, for example, how IT can help in faster inventory turns or reduce
cycle time for order to cash, or how we can reduce cost to serve for our
clients end customers.
AK: LETS TACKLE THE SUBJECT OF TODAYIT
INFSTRUCTURE TNSFORMATION. HOW DO YOU DO IT?
HOW DOES IT TNSLATE INTO COST SAVINGS?
DJ: IT Infrastructure optimization and transformation has to belooked at through four broad areas:
CONSOLIDATION: Our experience of working with customers across
industries proves that consolidation is a big lever for cost savings. As IT
assets increase so does IT infrastructure complexity, creating signicantmanagement problems. In addition, data center energy consumption
is skyrocketing, not to mention the energy prices rise. erefore, the
consolidation approach should focus on:
Consolidation of IT operations, such as a central monitoring and
command centre, IT service desk and knowledge database
Consolidation of IT Infrastructure, such as a reduced number of
datacenters and computer rooms
Consolidation of IT procurement. We believe that procurement for
global organizations gives them the scale to negotiate and manage
hardware and soware spend beer
Consolidation of services through shared model for service desks, and
factory model for application packaging.
6
ETMS ALI KLAVER interviews
DEEPAK JAIN (WIPRO)about enabling your business growth
through IT infrastructure transformation.
Transforming
businesshp://www.GlobalETM.com
-
8/9/2019 ETM Q3 2010 Issue
18/44
IT INFRASTRUCTURE TRANSFORMATIONASK THE EX
STANDARDIZATION: Simplication is again an important lever for
controlling costs. Over time, many customers have added complexity into
their IT environments which could be in the form of disparate applications,
operating systems, technologies, processes and tools being used.
We recommend our customers make one-time investments to
standardize the IT estate and look at ROI over ve to seven years.
TIONALIZATION:Application and infrastructure rationalization is
another key driver for cost reduction.
VIRTUALIZATION: Both on the data center side and on the end user side.e data center side is where one consolidates the servers and storage across
the enterprise. is leads to lower support costs and easier administration
without sacricing compute power and storage capacity.
On the desktop sidevirtualization of desktop or VDIthis leads to
beer control over the desktops, lower costs and increased ease of desktop
management and refresh.
AK: WHY IS IT IMPORTANT FOR A BUSINESS TO DO THIS NOW,
PARTICULARLY IN THE CURRENT ECONOMIC CLIMATE? WHAT
ARE THE MAIN BENEFITS?
DJ:e CIO/CTO organizations have realized that aer a phase of
over abundance there is a need to get to a state of equilibrium.Also, the future trends and technologies, including the disruptive
trends like cloud computing, will require organizations to seriously look at
consolidation, standardization and rationalization. erefore, its important
that organizations are ready to make the best advantage and avoid high
transition/migration costs as these trends mature.
e cost take-out initiative that companies started in 2008-09 also
continues because it was a multi-year program. First tranche of savings
came in from discounts from vendors. However, to get a sustainable cost
advantage, transformation is essential. Without this further cost take-out will
be extremely di cult.
We also believe that organizations will consolidate their business
portfolios and that the center of economic activity will shi to newer
geographiestime to market will be the key parameter to gain market share.
erefore, end users will not be bothered about the technology used
but will be more focused on the functionality it delivers. e economic
environment will move customers from being buyers of technology and
building on capacity, to looking at capacity on demand and utility models.
Companies that achieve the above will be quick in making the best use
of on-demand computing and manage exibility of infrastructure costs based
on business cycles.
AK: WHAT IS YOUR FAVORITE CASE STUDY THAT REALLY
HIGHLIGHTS WHAT WIPRO CAN DO IN THIS SPHERE?
DJ: We have multiple case studies to talk about, and there are threeimportant ones in particular.We are currently engaged with a customer in the energy and utility space
to transform their retail business, and one of the key KPIs is to bring down
their cost to serve by 10% per subscriber.
Secondly, were working with a client in the retail space to help manage
their IT cost as a function per square foot of retail space.
And thirdly, we manage IT cost as a function on the number of
subscribers for a client in the telecom space.
All of the above are large deals, not in the context of technology
transformation alone, but more importantly in terms of business
transformation. We believe that IT costs as a function of customer revenues
is important, but linking it to business parameters like the ones above ensures
that IT operations, technology adoption and spend on IT transformation i
optimal at all times and can be a function of the business growth.
AK: WHAT ARE TH E LEVERS FOR SUSTAINABLE COMPETITIVE
ADVANTAGE THROUGH INFTNSFORMATION?
DJ: IT transformation positions organizations to:BEER MANAGE COST AND RISK: Our hindsight experience of
delivering these services for close to three decades helps us to do the job wthe least possible risk, and at the most optimized cost through our Global
Delivery Model.
SUPPORT BUSINESS INNOVATION: Our domain understanding and
its trends helps us to understand our customers current and future needs.
We drive innovation in our solution to bring about business innovation for
our customers.
SCALE MORE EFFECTIVELY: We are not into product reselling on a
stand-alone basis, and were not incentivized to dump more products. We
analyze the customers current needs and the impact of their ever changing
business environment. at helps us to provide the most optimized solutio
for todays challenges while keeping scalability in mind for future growth.
REDUCE ARCHITECTUL COMPLEXITY: rough application
rationalization and infrastructure consolidation, we try to simplify IT forour customers so that it becomes easily manageable and more meaningful t
their business.
INCREASE THE VALUE OF REVENUEGENETING SERVICES
In many cases today we help our customers to increase their touch points
with their own customers, reduce their time to market, help them to delive
more e cient serv ices to their customers, and become more agile and
competitive in the market place.
ENHANCED END USER EXPERIENCE: While traditional methods
of monitoring IT services have been quite discrete in their approach, today
we measure our performance through the eyes of the business user that
experiences our services.
It is no longer enough if the servers are up 99.99% and the network is u
99.99% etc; what really maers is that the end user who is trying to comple
a transaction through an application is able to do it in the specied time.
By monitoring the performance across each layer of the chain we are able to
control the performance and deliver enhanced end user experience.
AK LETS LOOK TO THE FUTUREWHERE DO YOU SEE THE
FUTURE OF IT INFSTRUCTURE TNSFORMATION IN THE
NEXT TWO TO FIVE YEARS, AND WIPROS PART IN IT?
DJ: Wipro is very actively promoting a concept called 21st CenturyVirtual Corporation. Essentially it means organizations globally should ha
A detailed look at core and non-core processes
Lean process optimization to drive sustainable productivity improveme
Optimization of technology to enable innovation
Extended execution leveraging partners versus contractors in a whol
new way.
By virtue of three decades of experience in IT services and solutions, Wipr
is increasingly being chosen as a partner of choice by customers for IT
transformation.
Customers are increasingly looking to achieve business and IT
alignment, more meaningful reporting, beer coordination between variou
departments, a reduction of the overheads associated with managing
multiple vendors, and so on.
-
8/9/2019 ETM Q3 2010 Issue
19/44
hp://www.GlobalETM.com
XECUTIVE PANELSECURITY INFORMATION AND EVENT MANAGEMENT
0
ActionableIntelligence
-
8/9/2019 ETM Q3 2010 Issue
20/44
SECURITY INFORMATION AND EVENT MANAGEMENT EXECUTIVE P
AC: WHAT ARE YOUR CRITICAL
SUCCESS TIPS FOR USERS? HOW DO
YOU INCREASE THE CHANCE OF SIEM
DEPLOYMENT BEING SUCCESSFUL
EARLY ON AND THEN GET TO
ONGOING OPETIONAL SUCCESS?
ML:e most important thing is tomanage expectations and align the necessary
resources. Ensure that you have agreement
from every department that expects to benet
from a SIEM, and make sure the technical
resources they can apply to the planning and
implementation phases, as well as what metrics
theyre going to use, measure the success.
When working with larger organizations
and enterprises with de-centralized networking,
its likely that a SIEM vendor was probably
selected having gone through a proof of concept
deployment. e learning from these test runs
can be critical to planning and successfully
implementing production SIEMs.
Identify where the obstacles throughout the
organization might be as well as the individuals
who support the eort and can help champion
the cause, trying to nd some way that each area
of the enterprise will benet from the tool.
Also, dont assume that a SIEM that
performs well in its concept with just two
weeks worth of production data will perform
equally as well with 12 months. If you cant
generate in the kind of volume your SIEMwill be faced with in the real world, make sure
the vendor can supply sample data or provide
access to a host with commensurate volumes of
information to demonstrate what youll be faced
with a year down the road.
DU:I agree with you in terms of thePOC and production environments. A lot of
folks dont anticipate what their volume will be
and assume that its going to be able to scale.
Vendors can provide tools to inject that data
and there are other options to help you do that.
Seing expectations and geing executive
sponsorship and support is very key. e
customers that weve seen have the most succ
with implementations. It starts from the top,
assigning resources and making sure that folks
are on board.
ere are some process changes that go
along with itthe technology is not going to
work like magic. Its a tool and it needs to be
adopted by individuals and users.
I would also suggest you start with simple
use cases based on policies youve already
dened and for which you may or may not
already have processes in place, but at least
youre starting small and you can get them
in place. at helps you to validate and gain
condence in the system.
One example would be server monitoring
You want to try to identify whether someone
is compromising a server and knowing this
information can prevent insider abuse before
signicant damage is done. So geing server
user monitoring processes in place is an early
use case to start with.
Another common use case is rewall
monitoring to meet compliance needs as well
as to make sure that you can identify activity
paerns for forensics purposes, for example.
e next thing would be to really iterate over
these use cases.
So you start with the simple use cases and
then plan for the next phase of use cases whichmaybe a lile bit more advanced. is way
youre taking baby steps as you go, validating,
making accomplishments, and then preparing
yourself for future success.
AA: You should think of it as a classic Iproject. Plan, install, tune and train. When I sa
plan, its about involving the stakeholders who
might use this and then, beer yet, the vendor
that youve selected, because quite oen they c
have useful advice for you. ink about volum
usage, what youre going to audit and so o n.
DR. ANTON A. CHUVAKIN talks about the usability and integration of
security information and event management and touches on log management
with the added benefit of three industry experts; MICHAEL LELAND
(NITROSECURITY), A.N. ANANTH (PRISM MICROSYSTEMS)and DEBBIE UMBACH (RSA, THE SECURITY DIVISION OF
EMC).
-
8/9/2019 ETM Q3 2010 Issue
21/44
EAD TO HEAD BUSINESS PROCESS-DRIVEN ALM
2
ETMS ALI KLAVER chats to EDDY PAUWELS(SERENA SOFTWARE) about business process-drivenapplication lifecycle management and how they link to each other, as
well as how businesses can benefit from such a strategy.
Create your own
app factory
hp://www.GlobalETM.com
-
8/9/2019 ETM Q3 2010 Issue
22/44
-
8/9/2019 ETM Q3 2010 Issue
23/44
Every year or so the high
technology industry gets a new
buzzword or experiences a
paradigm shi which is hyped as
the next big thing.
For the last 12 months or so, cloud
computing has had that distinction. Anyone
reading all the vendor-generated cloud
computing press releases and associated
news articles and blogs would conclude that
corporations are building and deploying both
private and public clouds in record breaking
numbers.
e reality is much more sobering. While
there is a great deal of interest in the cloud
infrastructure model, the majority of midsized
and enterprise organizations are not rushing to
deploy private or public clouds in 2010.
An ITIC independent web-based
survey that polled IT managers and C-level
professionals at 700 organizations worldwide
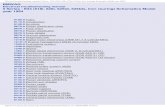
in January 2010, found that spending on cloud
adoption was not a priority for the majority of
survey participants during calendar 2010 (seeFigure 1).
However, that is not to say that
organizationsespecially mid-sized and
large enterprisesare not considering cloud
implementations. ITIC research indicates
that many businesses are more focused
on performing much needed upgrades to
such essentials as disaster recovery, desktop
and server hardware, operating systems,
applications, bandwidth and storage before
turning their aention to new technologies like
cloud computing.
Despite the many articles wrien about
public and private cloud infrastructuresover the past 18 months, many businesses
remain confused about cloud pecics such as
characteristics, costs, operational requirements,
integration and interoperability with their
existing environment or how to even get started.
DEMYSTIFYING THE CLOUD
What is cloud computing? Denitions vary. e
simplest and most straightforward denition
is that a cloud is a grid or utility style pay-as-
you-go computing model that uses the web to
deliver applications and services in real-time.
Organizations can choose to deploy a
private cloud infrastructure where they hosttheir services on-premise from behind the
safety of the corporate rewall. e advantage
here is that the IT department always knows
whats going on with all aspects of the corporate
data from bandwidth and CPU utilization to
all-important security issues.
Alternatively, organizations can opt for
a public cloud deployment in which a third
party like Amazon Web Services (a division of
Amazon.com) hosts the services at a remote
location. is laer scenario saves businesses
money and manpower hours by utilizing the
What are the organizations top IT spending priorities
for 2010 (select allthat apply*)?Disaster recovery 47%
45%
44%
41%
37%
36%
36%
35%
31%
30%27%
24%
17%
15%
13%
11%
11%
10%
9%
6%
2%
Upgrade server hardware
Deploy new apps to support the business
Server virtualization software
Replace older versions of server OS
Security
Upgrade desktop OS
Upgrade desktop hardware
Storage
Upgrade legacy server-based apps/DBs
Improve revenue and profitability
Increase bandwidth
Skills training for existing IT staffers
Desktop virtualization (VDI)
Upgrade the WAN infrastructure
Add remote access and mobility
Application virtualization
Green datacenter initiatives
Add IT staff
Build a private cloud infrastructure
Implement a public cloud infrastructure *Total may exceed 100%
Copyright 2009 ITIC All Right Reserved
NALYST FEATURE CLOUD COMPUTING
LAU DIDIO(ITIC)talks about thepartnerships, and divisions,
between the two sets of playersin the current virtual desktopinfrastructure marketCitrix/Microso and VMware/EMC.
Theprosandcons
ofcloud
8
-
8/9/2019 ETM Q3 2010 Issue
24/44
host providers equipment and management. All
thats needed is a web browser and a high-speed
internet connection to connect to the host to
access applications, services and data.
However, the public cloud infrastructure
is also a shared model in which corporate
customers share bandwidth and space on the
hosts servers.
Organizations that are extremely concernedabout security and privacy issues, and those that
desire more control over their data, can opt for a
private cloud infrastructure in which the hosted
services are delivered to the corporations
end users from behind the safe connes of an
internal corporate rewall.
However, a private cloud is more than just
a hosted services model that exists behind
the connes of a rewall. Any discussion of
private and/or public cloud infrastructure
must also include virtualization. While
most virtualized desktop, server, storage and
network environments are not yet part of acloud infrastructure, just about every private
and public cloud will feature a virtualized
environment.
Organizations contemplating a private
cloud also need to ensure that they feature very
high (near fault tolerant) availability with at
least ve nines (99.999%) uptime or beer.
e private cloud should also be able to
scale dynamically to accommodate the needs
and demands of the users. And unlike most
existing, traditional datacenters, the private
cloud model should also incorporate a high
degree of user-based resource provisioning.
Ideally, the IT department should also be
able to track resource usage in the private cloud
by user, department or groups of users working
on specic projects for chargeback purposes.
Private clouds will also make extensive use
of business intelligence and business process
automation to guarantee that resources are
available to the users on demand.
Given the Spartan economic conditions
of the last two years, all but the most cash-rich
organizations (and there are very few of those)
will almost certainly have to upgrade theirnetwork infrastructure in advance of migrating
to a private cloud environment.
Organizations considering outsourcing any
of their datacenter needs to a public cloud will
also have to perform due diligence to determine
the bona des of their potential cloud service
providers. ere are three basic types of cloud
computing although the rst two are the most
prevalent. ey are:
Soware as a Service (SaaS) which uses
the web to deliver soware applications
to the customer. Examples of this are
Salesforce.com, which has one of the most
popular, widely deployed, and the earliest
cloud-based CRM application; and Google
Apps, which is experiencing solid growth.
Google Apps comes in three editions
Standard, Education and Premier (the rst
two are free). It provides consumers and
corporations with customizable versions ofthe companys applications like Google Mail,
Google Docs and Calendar.
Platform as a Service (PaaS) oerings;
examples of this include the above-
mentioned Amazon Web Services and
Microsos nascent Windows Azure
Platform. e Microso Azure cloud
platform oering contains all the elements
of a traditional application stack from the
operating system up to the applications and
the development framework. It includes
the Windows Azure Platform AppFabric
(formerly .NET Services for Azure) as well asthe SQL Azure Database service. Customers
that build applications for Azure will host
it in the cloud. However, it is not a multi-
tenant architecture meant to host your entire
infrastructure. With Azure, businesses will
rent resources that will reside in Microso
datacenters. e costs are based on a per
usage model. is gives customers the
exibility to rent fewer or more resources
depending on their business needs.
Infrastructure as a Service (IaaS) is
exactly what its name implies: the entire
infrastructure becomes a multi-tiered hosted
cloud model and delivery mechanism. Both
public and private clouds should be exible
and agile. e resources should be available
on demand and should be able to scale up or
scale back as business needs dictate.
CLOUD COMPUTINGPROS AND
CONS
Cloud computing like any emerging
new technology has both advantages
and disadvantages. Before beginning
any infrastructure upgrade or migration,organizations are well advised to rst perform a
thorough inventory and review of their existing
legacy infrastructure and make the necessary
upgrades, revisions and modications.
Next, the organization should determine
its business goals for the next three to ve
years to determine when, if, and what type
of cloud infrastructure to adopt. It should
also construct an operational and capital
expenditure budget and a timeframe that
includes research, planning, testing, evaluation
and nal rollout.
PUBLIC CLOUDS ADVANTAGES AND
DISADVANTAGES
e biggest allure of a public cloud
infrastructure over traditional premises-based
network infrastructures is the abili ty to o oa
the tedious and time consuming management
chores to a third party. is in turn can help
businesses:
Shave precious capital expenditure
monies because they avoid the expensive
investment in new equipment including
hardware, soware and applications as well
as the aendant conguration planning and
provisioning that accompanies any new
technology rollout.
Accelerated deployment timetable. Havi
an experienced third party cloud services
provider do all the work also accelerates th
deployment timetable and most likely mea
less time spent on trial and error.
Construct a exible, scalable cloud
infrastructure that is tailored to their
business needs. A company that has
performed its due diligence and is working
with an experienced cloud provider can
architect a cloud infrastructure that will sca
up or down according to the organizations
business and technical needs and budget.
e potential downside of a public cloud
that the business is essentially renting commo
space with other customers. As such, dependi
on the resources of the particular cloud mode
there exists the potential for performance,
latency and security issues as well as acceptab
response, and service and support from the
cloud provider.
Risk is another potential pitfall associated
with outsourcing any of your rms resources
and services to a third party. To mitigate
risk and lower it to an acceptable level, its
essential that organizations choose a reputabl
experienced third party cloud services provid
very carefully.
Ask for customer references and check th
nancial viability. Dont sign up with a serviceprovider whose nances are tenuous and who
might not be in business two or three years
from now.
e cloud services provider must work
closely and transparently with the corporation
to build a cloud infrastructure that best suits
the business budget, technology and business
goals.
To ensure that the expectations of both
parties are met, organizations should create a
checklist of items and issues that are of crucial
importance to their business and incorporate
CLOUD COMPUTINGANALYST FEA
-
8/9/2019 ETM Q3 2010 Issue
25/44
XECUTIVE PANEL IT OUTSOURCING
2
MIKE ATWOOD (HORSES FOR SOURCES) moderates
a panel discussion on IT outsourcing touching on transformation,
the cloud and some fantastic case studies with the help ofCHUCK
VERMILLION (ONENECK IT SERVICES) and KARINE
BRUNET (STERIA).
A marriage of sorts
hp://www.GlobalETM.com
-
8/9/2019 ETM Q3 2010 Issue
26/44
IT OUTSOURCING EXECUTIVE PA
MA: A S YOU EXPAND YOUR BUSINESS,
WHAT IS YOUR IDEAL CLIENT AND
WHAT LETS YOU RECOGNIZE THAT?
KB: A typical client is one that wants toexperience a big transformation in the coming
months or years. It can be transformation of its
IT or its entire organization, perhaps through
mergers and acquisition. I think this is where anoutsourcer can bring the best value.
Looking especially at the prole of Steria,
we work very closely with our clients to assist
them in their transformation. So for us, a very
good client is one with a transformation agenda.
MA: AND IN TERMS OF IT RESOURCES,
IS WHAT YOURE PROVIDING HOSTING,
AND HOW DOES THAT HELP WITH A
TNSFORMATION?
KB:I think were providing not
resources but services, and thats what we mean
by outsourcing.
Steria is a mid-sized player in the market
and its one of the top ten players in the
European market. One of our dierentiators is
the fact that we have very good proximity and
exibility with our clients.
Prior to migrating a client, one of our
key capabilities is to be exible enough in the
transformation phase to adapt our service
solution to whatever the client challenges are.
Another demonstration of that exibility may
lie in that one part of our service incorporates
an oshore alternative, but we may still need
people on site for certain services because the
client is not mature enough to have everything
fully outsourced.
We are able to accommodate that, and then
industrialize the service delivery and the service
mechanism to achieve an e cient deliver y.
MA: DO YOU PROVIDE ANY TNS
FORMATIONAL CONSULTING SERVICES?
KB: We provide two types oftransformation consulting services; one in thetechnical aspect which is about transforming your
IT infrastructuremeaning virtualization and
platform as a service or cloudand one which is
much more on the organizational level.
Restructuring the way you operate your
IT services can be tricky, but as a mid-sized
player, we see more and more clients deciding
on selective sourcing. is requires that they
organize the governance, processes and how
theyre going to manage multiple suppliers, as
well as the potential to mix with internal teams.
We also provide organizational consulting to
assess the maturity of the organization and their
processes, and advise on that.
MA: CHUCK, WH AT IS YOUR IDEAL
SCENARIO?
CV:For us it starts with painwe dontlike that our customers are in painbut we liketo talk to companies that are experiencing pain
because, generally speaking, theyre trying to
avoid the experience of managing their own IT
systems and have just had enough. ey want
someone else to do it for them.
Or, they recognize the pain when theyre
implementing a new system and have decided
theyre not up to the task of eectively
managing that new environment.
e second thing we look for is a
complicated environment. I think we really
dierentiate ourselves when we nd that its
not just a single application our customers
are looking to host or outsource, but rather,
theyre looking to outsource a multiple set
of applications on several dierent types of
infrastructure.
is is where were best able to dierentiate
our capabilities.
MA: AND DO YOU PROVIDE ANY SORT
OF TNSFORMATIONAL SERVICES?
CV:IT outsourcing generally createstransformation within a company because
youre signicantly changing the way they view
and access their IT services. With regards to
calling it transformational servicesno, we
dont provide any services described as such.
We know who we are as an outsource
provider of IT services. We pride ourselves
on the fact that customers would look at us
not as a vendor, but recognize us as one of
their employees.
MA: ONE OF THE ISSUES THAT
NORMALLY ARISE WHEN SOMEONE
IS THINKING ABOUT OUTSOURCINGIS: WHAT EXACTLY DO I OUTSOURCE?
WHAT IS THE SCOPE OF THE
OUTSOURCING PROJECT, AND WHAT
AM I GOING TO SEND OUT? CHUCK,
WHAT WOULD YOU ADVISE A CLIENT
THAT THEY SHOULD OUTSOURCE?
CV:We can provide a broad array ofservices and do everything for our customers;
from as low as the base infrastructure providing
the data centre services, all the way through
the application level that includes not only th
enterprise or ERP application management, b
also functional consulting on top of that.
Our support centre is one where someon
can not only call in if theyre having a technica
issue, but they can also call our support centre
theyre having functional issues, such as gein
a batch release in the ERP system, or how to
beer use the manufacturing functionality toaccomplish a particular task.
Also, with regards to the EDI or electroni
data interchange, we will host and manage
customers EDI translators. Well establish the
trading relationships with the trading partner
test those transaction sets, and then ensure th
they go forward in production.
When there are errors agged by the
translator, well research the nature of the issu
and then forward that information back to
someone in the company to help x whatever
data issue is causing the problem. Its almost
business process outsourcing in some of these
cases.
We also do outsourcing of desktop
administration. In some cases its done with o
site desktop resources, and in others its done
with the desktop resources in our location in a
depot fashion. We have a very broad capability
MA: AND WHEN YOU DO THE
OUTSOURCING, WHAT ASSETS DO
YOU OWN AND WHAT ASSETS DO
YOU ADVISE THE CLIENT THAT THEY
OUGHT TO KEEP OWNERSHIP OF?
CV:Were prey exible with regardsto asset ownership. Generally speaking, we
encourage customers to keep the assets they
started with. We move the assets from their
facilities to our facilities and provide the
services.
However, as the relationship starts to
mature and the assets come to the end of their
useful life, our customers can decide what
theyre going to do from a new equipment
acquisition perspective. Oentimes they look
to OneNecks cloud services as an alternativeto owning their own assets. However, from a
desktop perspective, they normally continue t
own their own assets.
MA: IS THERE SOME SCOPE THAT
WOULD BE TOO SMALL OR THAT YOU
WOULDNT TAKE ON?
CV:No, for us its all about makingsure our customers are satised and that were
solving a business problem.
-
8/9/2019 ETM Q3 2010 Issue
27/44
have everywhere is to verify that the accounts
for these departing employees have been
properly terminated.
ere is a use case which is called the
pink slip null which is essentially when HR
tells you that a person has been let go or has
chosen to resign, which to IT means that their
access and accounts must be removed from the
directory. You can put that username into your
list and start looking for any activity from those
usernames for the next few weeks.
is is a failsafe to make absolutely sure
that there is no further activity. If youre doing
Active Directory youve probably removed that
username or disabled them, but they could have
congured a service with their name, as we
SK THE EXPERT SECURITY INFORMATION AND EVENT MANAGEMENT
SIEM
satisfaction
AK: ANANTH, COULD YOU GIVE
US A FEW EXAMPLES OF SIEM IN
OPETIONAL USE CASES ?
AA: One example thats clear in theserecessionary times is that people have had
turnover in sta, particularly in North America,
as so-called pink slips. A problem that IT people
One of the most ignored benets of securityinformation and event management technologyis using SIEM technology to improve overallIT operations.A. N. ANANTH andSTEVE LAFFERTY (PRISM
MICROSYSTEMS) talk to ETMS ALIKL AVER about how improved operations is seldomgiven much aention but might well provide themost tangible cost justication.
4
-
8/9/2019 ETM Q3 2010 Issue
28/44
found out with one of our customer locations
some time back.
So its a good idea to do this because its
very inexpensive to run and should be coming
up empty if youve done your job right. Its a
fantastic way of assuring yourself that things
have gone according to plan.
If you look at the security vulnerabilities,
a lot of it happens because of default accounts
that have been dormant for a long time and