Lecture 3: The Transport Layer: UDP and TCPshervin/courses/ceg4185/lecture… · ·...
Transcript of Lecture 3: The Transport Layer: UDP and TCPshervin/courses/ceg4185/lecture… · ·...
1
Prof. Shervin Shirmohammadi CEG 4185 3-1
Lecture 3:
The Transport Layer:
UDP and TCP
Prof. Shervin Shirmohammadi
SITE, University of Ottawa
Prof. Shervin Shirmohammadi CEG 4185 3-2
The Transport Layer
• Provides efficient and robust end-to-end service to upper layers.
– Not all services need to be provided!
• Uses services provided by the network layer.
• End-to-end delivery of entire message.
Connection
2
Prof. Shervin Shirmohammadi CEG 4185 3-3
End-to-End Delivery
• Services are done from an end-to-end perspective
– Error control, flow control, …
• Connectionless or connection-oriented
…
Transport layer
Networking layer
Prof. Shervin Shirmohammadi CEG 4185 3-4
Addressing• Service Access Point (SAP), also referred to as Ports at
the transport layer.
3
Prof. Shervin Shirmohammadi CEG 4185 3-5
Reliable Delivery
• Note that it is not compulsory for a transport layer protocol to provide such services.
• The idea is that if any of these services are to be provided in an end-to-end sense, then the transport layer is where you would implement them.
Prof. Shervin Shirmohammadi CEG 4185 3-6
error checked
at networking
error checked
at networking
error checked
at networking
Error Control
• Error checking is done for the Transport
Layer PDU (T-PDU).
• Even though T-PDU is put into the N-PDU
as payload, the networking layer may or
may not provide error control for it.
– What does IP do?
4
Prof. Shervin Shirmohammadi CEG 4185 3-7
Sequence Control
Prof. Shervin Shirmohammadi CEG 4185 3-8
Loss Control
5
Prof. Shervin Shirmohammadi CEG 4185 3-9
Duplication Control
What can cause duplication?
Prof. Shervin Shirmohammadi CEG 4185 3-10
Flow Control• Controls the flow of information, again from an end-to-end perspective.
– Factors affecting this are the end host, but also the network.
6
Prof. Shervin Shirmohammadi CEG 4185 3-11
Multiplexing and Demultiplexing
Data Link Networking
Transport
Prof. Shervin Shirmohammadi CEG 4185 3-12
App1 App2 App3
TCP UDP123 250 125
IP
App 3 dataSPort=125
data data data
App 2 dataSPort=250
App 1 dataSPort=123
TCP dataProtocol=TCP
TCP dataProtocol=TCP
UDP dataProtocol=UDP
to data Link layer
Multiplexing
TCP dataProtocol=TCP
7
Prof. Shervin Shirmohammadi CEG 4185 3-13
App1 App2 App3
TCP UDP560 440 1090
IP
App 3 dataDPort=1090
data data data
App 2 dataDPort=440
App 1 dataDPort=560
TCP dataProtocol=TCP
TCP dataProtocol=TCP
UDP dataProtocol=UDPFrom data Link layer
Demultiplexing
TCP dataProtocol=TCP
Prof. Shervin Shirmohammadi CEG 4185 3-14
Connection
• Obviously required only if we’re talking
about a connection-oriented transport
protocol.
– Otherwise just send the packet and hope for the
best.
• Need two protocols really:
– connection establishment
– connection release
8
Prof. Shervin Shirmohammadi CEG 4185 3-15
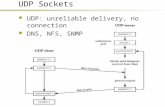
User Datagram Protocol (UDP)• Defined in RFC 768.
• Connectionless service
• Multiplexing/Demultiplexing
• Error Detection (not really error control)
– Detection only, no recovery; and even the detection is optional
• No flow control
• No congestion control
• What does it do then?
• Used by SNMP, DNS, RTP, Multicasting.
Prof. Shervin Shirmohammadi CEG 4185 3-16
Multiplexing/Demultiplexing
• Uses Port numbers
– Also used for addressing
9
Prof. Shervin Shirmohammadi CEG 4185 3-17
13: daytime 53: name server
69: TFTP 111:RPC
161 SNMP
ICANN Ranges
Internet Corporation for Assigned Names and Numbers
http://www.icann.org/
Prof. Shervin Shirmohammadi CEG 4185 3-18
UDP Packet Format
• There is also a pseudo-header that is created
and computed. The pseudo-header does not
really exist as a header!
10
Prof. Shervin Shirmohammadi CEG 4185 3-19
Pseudoheader
• This is done to detect wrong delivery of the packet by the
Networking layer.
Prof. Shervin Shirmohammadi CEG 4185 3-20
Checksum
One’s complement of the one’s complement sum modulo
11
Prof. Shervin Shirmohammadi CEG 4185 3-21
Multicasting
• The ability to send a packet to more than one
destination. (send once, receive at multiple
destinations).
• Uses the IP multicasting (class D) addresses.
• Interested parties must join a multicast group.
• Network infrastructure (routers, bridges, …)
must support IP Multicast for this to happen
• Mostly not supported on the Internet.
Prof. Shervin Shirmohammadi CEG 4185 3-22
Transmission Control Protocol (TCP)
12
Prof. Shervin Shirmohammadi CEG 4185 3-23
TCP - Transmission Control Protocol
• Provides reliable end-to-end byte stream over unreliable IP subnet.
• Designed to dynamically adapt to properties of subnet (bandwidth, delay, loss) and for robust handling of failures.
• Initial definition in standard RFC 793. Updates in RFC 1122, RFC 1323, RFC 2001
• TCP accepts user data from local processes, splits into pieces no larger than 64K bytes (usually about 1500 bytes in practice), and sends each piece as a separate IP datagram. When IP datagrams arrive at the destination, TCP reconstructs the original byte stream.
Prof. Shervin Shirmohammadi CEG 4185 3-24
The Service TCP Provides
• Connection-oriented
• Connection release
• Point-to-point communication
• Addressing, Multiplexing and Demultiplexing
• Complete reliability
• Full-duplex communication
• Reliable connection startup and shutdown– 3-way handshake
• Flow Control
• Congestion Control
13
Prof. Shervin Shirmohammadi CEG 4185 3-25
Port Numbers
Prof. Shervin Shirmohammadi CEG 4185 3-26
Reserved TCP Port Numbers
14
Prof. Shervin Shirmohammadi CEG 4185 3-27
TCP Error Control
• Sources of error:
– Segment damaged in transit
– Segment fails to arrive
• Transmitter does not know of failure
• Receiver must acknowledge successful receipt
• Too many ACKs if sent for each segment
– Use cumulative acknowledgement
• Time out waiting for ACK triggers retransmission (retransmission timer)
Prof. Shervin Shirmohammadi CEG 4185 3-28
Duplication Detection
• If ACK lost, segment is re-transmitted
– Causes duplication
• Receiver must recognize duplicates
• Duplicate received prior to closing connection
– Receiver assumes ACK lost and ACKs duplicate
– Sender must not get confused with multiple ACKs
– Sequence number space large enough to not cycle within maximum life of segment
• Duplicate received after closing connection
15
Prof. Shervin Shirmohammadi CEG 4185 3-29
Flow Control: Credit Allocation
Prof. Shervin Shirmohammadi CEG 4185 3-30
Congestion
• Caused by too much traffic going through a network;
more than the network can handle.
• Results in Routers dropping packets.
• Causes time-outs: equally likely from lost messages due
to unreliable transmission media, as from congestion.
• Simply retransmitting a lost message makes congestion
worst.
– Why?
• There needs to be a way to control congestion.
16
Prof. Shervin Shirmohammadi CEG 4185 3-31
TCP Congestion Control
• RFC 1122, Requirements for Internet hosts
• Retransmission timer management
– Estimate round trip delay by observing pattern
of delay
– Set time to value somewhat greater than
estimate
– Simple average
– Exponential average
– RTT Variance Estimation (Jacobson’s
algorithm)
Prof. Shervin Shirmohammadi CEG 4185 3-32
Window Management• Slow start
– awnd = MIN[credit, cwnd]
– Start connection with cwnd=1
– Increment cwnd (double) with ACK, to some threshold
– Increment cwnd by 1 with ACK after the threshold
• Dynamic windows sizing on congestion
– When a timeout occurs
– Set slow start threshold to half current window
• ssthresh=cwnd/2
– Set cwnd = 1 and slow start until cwnd=ssthresh
• Increasing cwnd by 1 for every ACK
– For cwnd >=ssthresh, increase cwnd by 1 for each RTT
17
Prof. Shervin Shirmohammadi CEG 4185 3-33
TCP Slow Start
Prof. Shervin Shirmohammadi CEG 4185 3-34
TCP Data Transfer• Connection is a stream of bytes, not messages.
– Four messages of 512 bytes may be sent by TCP as any combination of pieces totaling 2048 bytes:
• 1 × 2048 bytes
• 2 × 1024 bytes
• 4 × 512 bytes
• 8 × 256 bytes
• ...
• When application sends data to TCP, it may not be sent immediately:
– TCP may decide to collect more data before transmission.
– TCP PUSH flag is used to request no transmission delay.
• TCP URGENT flag immediately sends all pending data, and
causes receiver to send an interrupt to its user.
18
Prof. Shervin Shirmohammadi CEG 4185 3-35
TCP Header
Prof. Shervin Shirmohammadi CEG 4185 3-36
Control Field
19
Prof. Shervin Shirmohammadi CEG 4185 3-37
TCP Header Fields• Source and destination ports: 16 bit address of local port
(socket).
• Sequence and acknowledgment numbers:
– Every byte is numbered in a TCP stream.
– Acknowledgment number is next byte number expected.
– 32 bits each.
• Header length:
– Needed because options field can vary in length.
– Number of 32 bits words in header.
• URG: set to 1 if urgent pointer in use
– Pointer indicates offset from current sequence number at which urgent data ends.
– Meaning that the receiving program should be notified of its arrival as soon as possible.
Prof. Shervin Shirmohammadi CEG 4185 3-38
TCP Header Fields (cont’d)• ACK: Set to 1 to indicate acknowledgment number is valid
– If 0, no acknowledgment in this segment.
• PSH: Set to 1 to indicate pushed data.
– Force delivery of bytes currently in the stream without waiting for buffer to fill.
• RST: Set to 1 to indicate reset.
– Host has become confused due to crash or for other reason.
– Also used to reject a connection, or refuse an invalid segment.
• SYN: used to establish connections.
– SYN = 1, ACK = 0 in connection request.
– SYN = 1, ACK = 1 in connection acceptance.
• FIN: set to 1 to indicate end of user data.
– Used to close connection.
– May continue to receive data.
20
Prof. Shervin Shirmohammadi CEG 4185 3-39
TCP Error Checking
• Checksum field provides error detection information for TCP segment header, plus the pseudo-header shown above.
• Checksum computation:
– Set checksum field to all zeros.
– Pad user data with extra 0 byte, if needed, so that user data has an even number of bytes.
– Add all 16 bit words in 1’s complement, and take 1’s complement of the sum.
– When receiver performs this computation, including checksum field, result should be 0.
TCP segment length00000000
Destination address
Source address
32 bits
Protocol = 6
TCP “Pseudo-header”
Prof. Shervin Shirmohammadi CEG 4185 3-40
Additional Timer Issues• TCP persistence timer:
– Prevents deadlock when current window size is 0, and acknowledgment increasing window size is lost.
– When persistence timer expires, ask receiver for window size.
• TCP keep alive timer:
– Timer expires after long interval with no messages.
– On expiry, send a message to receiver asking “are you still there?”
– Connection terminated if no response.
• TCP close timer ensures all packets die on connection termination.
























![User Datagram Protocol (UDP) UDP [RFC 768] UDP Socket](https://static.fdocuments.us/doc/165x107/586e022b1a28ab3c168b57c2/user-datagram-protocol-udp-udp-rfc-768-udp-socket.jpg)