ATM Simulation Using Fingerprint Verification
-
Upload
shashank-verma -
Category
Documents
-
view
613 -
download
3
Transcript of ATM Simulation Using Fingerprint Verification

ATM Simulation with Fingerprint Verification
Submitted to
Amity University Uttar Pradesh
in partial fulfillment of the requirements for the award of the Degree of
Bachelor of Technology inComputer Science & Engineering
by
Shashank VermaTanya Gupta
under the guidance of
Mrs. Divya Sharma
DEPARTMENT OF COMPUTER SCIENCE & ENGINEERING AMITY SCHOOL OF ENGINEERING AND TECHNOLOGY
AMITY UNIVERSITY UTTAR PRADESHNOIDA (U.P.)
1

DECLARATION
We, Tanya Gupta and Shashank Verma student(s) of B.Tech (Computer Science And
Engineering) hereby declare that the project titled “ATM Simulation with Fingerprint
Verification” which is submitted by us to Department of Computer Science And
Engineering, Amity School of Engineering and Technology, Amity University Uttar
Pradesh, Noida, in partial fulfillment of requirement for the award of the degree of
Bachelor of Technology in Computer Science And Engineering, has not been
previously formed the basis for the award of any degree, diploma or other similar title
or recognition.
2

Certificate
On the basis of declaration submitted by Tanya Gupta and Shashank Verma,
student(s) of B. Tech Computer Science And Engineering, I hereby certify that the
project titled “ATM simulation using Fingerprint Verification” which is submitted to
Department of Computer Science And Engineering, Amity School of Engineering and
Technology, Amity University Uttar Pradesh, Noida, in partial fulfillment of the
requirement for the award of the degree of Bachelor of Technology in Information
Technology is an original contribution with existing knowledge and faithful record of
work carried out by them under my guidance and supervision.
To the best of my knowledge this work has not been submitted in part or full for any
Degree or Diploma to this University or elsewhere.
Noida
Date (Guide)
Department of Computer Science And
Engineering
3

ABSTRACT
The need to control access to certain information and resources has been taken
seriously nowadays due to fraud and other threats to current security systems. This
research believes that that no single method, algorithm, key or procedure is entirely
secure. Hence a combination of multiple security components is mandatory to
provide a high level of protection against fraud and other threats. This project is
about enhancing the security feature of an ATM feature by fingerprint verification.
It looks into the vulnerabilities of ATM cards, Personal Identification numbers
(PIN) or passwords widely used in systems today. As a result, the aim of the project
is to propose a framework for user identification and authentication in automated
teller machines (ATM) as opposed to PIN. This robust method of user identification
and authentication would hopefully reduce the vulnerabilities of ATM in the future.
ACKNOWLEDGEMENT
Our sincere gratitude goes to all those who cooperated and showed unconditional
interest in helping us out in this project work.
4

This Project is a result of the persistent guidance, enthusiastic views and provoking
suggestions of our Faculty Guide, Mrs.Divya Sharma. We well appreciate the time
she took out from his busy schedules to tend to all our queries. We express our
genuine gratitude to him for welcoming and accepting our ideas, for providing all the
facilities needed during the project development and for always bringing out the best
in us.
We must acknowledge our deep debt of gratitude to numerous faculty members
whose great and masterly work we have consulted during the preparation of this Final
Year Project.
Last but never the least, we would like to acknowledge the ongoing support of our
respective family members as well as friends who helped us throughout our project by
providing moral support and helping us in solving problems we faced during the
project.
Date –
Noida
Tanya Gupta
Shashank Verma
5

CONTENTS
Candidate’s Declaration iii
Certificate iv
Acknowledgements v
Abstract vi
Contents xv
List of Figures
List of Tables
CHAPTER 1 INTRODUCTION 17
1.1 Problem Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
1.2 Motivation and Challenges . . . . . . . . . . . . . . . . . . . . . . . . 17
1.3 Using Biometrics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
1.4 What is fingerprint? . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
1.5 Why use fingerprints? . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
1.6 Using fingerprint recognition system for ATM System. . . . . . . . . 19
1.7 Organization of the thesis . . . . . . . . . . . . . . . . . . . . . . . . 19
CHAPTER 2 AUTOMATED TELLER MACHINE FRAMEWORK 21
2.1 Hardware - Software Level Design . . . . . . . . . . . . . . . . . . . . 21
2.2 Attendance Management Approach . . . . . . . . . . . . . . . . . . . 22
6

2.3 On-Line Attendance Report Generation . . . . . . . . . . . . . . . . . 23
2.4 Network and Database Management . . . . . . . . . . . . . . . . . . 24
2.5 Using wireless network instead of LAN and bringing portability . . . 24
2.5.1 Using Portable Device . . . . . . . . . . . . . . . . . . . . . . 30
2.6 Comparison with other student attendance systems . . . . . . . . . . 30
CHAPTER 3 FINGERPRINT IDENTIFICATION SYSTEM 33
3.1 How Fingerprint Recognition works? . . . . . . . . . . . . . . . . . . 33
3.2 Fingerprint Identification System Flowchart . . . . . . . . . . . . . . 33
9 Conclusion 73
9.1 Outcomes of this Project . . . . . . . . . . . . . . . . . . . . . . . . . 74
10 Future Work and Expectations 75
10.1 Approach for Future Work . . . . . . . . . . . . . . . . . . . . . . . 75
7

List of Figures
1.1 Example of a ridge ending and a bifurcation . . . . . . . . . . . . . . 18
2.1 Hardware present in classrooms . . . . . . . . . . . . . . . . . . . . . 22
2.2 Classroom Scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
2.3 Network Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
2.4 ER Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
2.5 Level 0 DFD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
2.6 Level 1 DFD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
2.7 Level 2 DFD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
2.8 Portable Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
3.1 Fingerprint Identification System Flowchart . . . . . . . . . . . . . . 34
8

List of Tables
9

2.1 Estimated Budget . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
10

Chapter 1
Introduction
Over the past three decades, consumers have been largely depending on and trust the
Automatic Teller Machine, better known as ATM machine to conveniently meet their
banking needs. Using an ATM, customers can access their bank accounts in order to
make cash withdrawals, debit card cash advances, and check their account balances as well
as purchase prepaid cellphone credit. Most ATMs are connected to interbank networks,
enabling people to withdraw and deposit money from machines not belonging to the bank
where they have their accounts or in the countries where their accounts are held (enabling
cash withdrawals in local currency).
1.1 Problem Statement
Designing a prototype model of ATM system and enhanching its security with the help of
fingerprint recognition technique.
11

Figure 1. Context diagram for the prototype system
1.2 Motivation and Challenges
Despite the numerous advantages of ATM system, ATM fraud has recently become more
widespread. Fraud techniques such as card skimming, shoulder surfing etc. have been
observed recently. In order to increase the level of security of the ATM networks use of a
biometric technique for verification along with existing PIN has been thought of a solution
to decrease the increasing number of frauds. Also in rural areas people are not educated
enough to use the ATM system. So, use of only biometric verification can help those
people access the ATMs in an easier manner and hence increase its popularity among rural
masses.
We tried to develop a prototype model for the same, which would use PIN number along
with the fingerprint verification scheme to verify the user before he/she can access his /her
account and make the transactions. However ATMs using single layer of verification ie.
Biometric verification can also be developed using our prototype model.
1.6 Using fingerprint recognition system for ATM system
12

Managing the security of the ATM system is a challenging task. This could be achieved
only by increasing the levels of protection of the system. It can be done with the help of a
fingerprint identification system developed in this project. This fingerprint
identification system uses existing as well as new techniques in fingerprint recognition
and matching. A new one to many matching algorithm for large databases has been
introduced in this identification system.
Chapter 2 13

Literature Review
2.1 Biometrics
Biometrics is a technique that analyzes human characteristics to distinguish one
person from another. It uses unique, measurable characteristics or traits of a human
being for automatically recognizing or verifying identity. Measurable biometrics
characteristics can be divided into two categories. The first category is the physical
characteristics consisting of the eye, the iris, the retina, the face, the fingerprints, hand
geometry, finger geometry, palm print,
vein patterns, and ear shape. The second category is the behavioral characteristics
such as signature, voice, keystroke, and body odor. Nine biometrics technologies have
been compared and it was concluded that fingerprinting is the only technology that is
legally accepted, readily automated and matured which has been used and accepted
14 in forensic application since the 1970s. Although signatures are also legally
acceptable biometrics, they are facing issues on accuracy, forgery and behavioral
variability for automatic identification. Therefore, the best biometrics technique is
fingerprint recognition, since it is the most mature technology and has been accepted
all over the world.
2.1.1 The Fingerprint
The fingerprint is the easiest ‘something you are’ characteristic to capture
and process. It is also very easy for a user to supply and the technology is
neither invasive nor inconvenient. In fact, among all the biometrics
techniques, fingerprint based identification is the oldest method which has
been successfully used in numerous applications.
Fingerprinting is one of the most mature technologies and considered
legitimate evidence in courts of law all over the world (Jain er al., 2001). It
is also used in forensic investigations. Recently, an increasing number of
civilian and commercial applications are either using or actively considering
using fingerprint based identification because of a better understanding of
15fingerprints and furthermore, its matching perfonnance is better than any
14

other existing biometrics technologies (Jain er al. , 2001).
A fingerprint is believed to be unique to each person and also each finger. It
is unique in terms of the arrangement of its minutiae. Even identical twins
have different fingerprints and they do not change over time. This can be described by the
probabilistic model as:
P(C) = P(N).P(M).P(A) (2.1)
where: P(N) = f(Poisson’s Law)
P(M) = f(frequency of appearance of minutiae type)
P(A) = f(no. of possible permutations of minutiae)
From the probabilistic model, it is calculated that the
probability of finding two identical fingerprints is one over eight billions
fingerprints.
2.1.2 Capturing Fingerprint Methods
There are two ways of capturing the fingerprint image: inked (offline) and
live scan (ink less). For the inked methods, a fingerprint is
obtained by an impression of it on a paper and then scanned using a flatbed
document scanner. This method is usually used in law enforcement to
identify suspects from the crime scene.
In the live scanning, there are three main methods to capture fingerprint
images: the optical, the capacitive and the thermo conductive. The optical method is
implemented with a small camera and light
source to capture an image of a fingerprint. The capacitive method makes
full use of the human body’s natural electrical charge to measure the
differences in capacitance value between ridges and valleys in a fingerprint;
algorithms are then used to construct an image from the capacitance values.
The last method, which is the thermo conductive method, is done by
measuring the human tissue characteristic thermal conductivity differences
between the ridges and the valleys of a fingerprint. In other words, the
ridges and valleys conduct heat at different rates and these differences can
be registered. The last two methods are reliable for differentiating a living
finger and a dead finger.
15

2.1.3 Fingerprint Representation
Fingerprint representation, commonly known as template, can be classified
into two types: local and global. For the local type of fingerprint
representation, the information of the fingerprint is based on the entire
image, finger ridges, and pores on the ridges or salient features derived from
the ridges (Jain et al., 2001). Representation predominantly based on ridge
endings or bifurcations is the most common.
Figure 2 1: Ridge ending and ridge bifurcation.
The combination of ridge endings and ridge bifurcations is known as
minutiae. Representations of fingerprints based on minutiae are made
because the captured minutia consist of individual information and is
storage efficient and its detection is relatively robust to various sources of
fingerprint degradation. The template relies on the minutiae locations and
the directions of the ridges.
For the global type, on the other hand, the information is contained in the
global pattems of ridges, which provides more infonnation including the
fingerprint critical points such as core and delta (Figure 2 2). It can be used
in a large scale fingerprint identification system which classified the
fingerprints into categories based on the information contained in the global
patterns of ridges. The classification elaborates methods of manual systems
to index individuals into bins based classification of their fingerprint. These
methods eliminate the need to match an input fingerprint(s) to the entire
fingerprint database in identification system, hence reducing the computing
requirements.
Figure 2 2: Sample fingerprint with core and delta marked
2.1.4 Feature Extraction16

Feature extraction deals with detecting the ridge endings and the ridge
bifurcations from the input fingerprint images. In practice, it is not always
possible to obtain a perfect ridge map in an input fingerprint due to a
number of factors such as aberrant formations of epidermal ridges of
fingerprints, postnatal marks, occupational marks, etc.. Therefore in order to
get a better feature of the fingerprint, there are five methods to extract the
feature on the fingerprint images:
i. Orientation Estimation
Orientation estimation deals with the orientation field of a fingerprint image
which represents the directionality of ridges in the fingerprint image. The
fingerprint image is divided into a non overlapping block such as 32 by 32
pixels and an orientation representative of the ridges in the block. The block
orientation could be determined from the pixel gradient using either
averaging method, voting method or optimization method (Jain et al., 2001).
ii. Segmentation
Segmentation is done to localize the portion of a fingerprint image depicting
the finger (foreground). Two ways of segmentation are known as global or
adaptive thresholding. A reliable approach for segmentation exploits the fact
that there is a significant difference in the magnitudes of variance in the
gray levels along and across the flow of a fingerprint ridge. The block size for variance
calculation typically spans one to two
inter ridge distances.
iii. Ridge Detection
Ridge detection can be done by either the simple or the thresholding
approach. These approaches might not work for noisy and low contrast
portions of a fingerprint image. The important criterion is the gray level
values of the ridges on a fingerprint image which attain their local maxima
along a direction normal to the local ridge orientation. Based on these
criteria, pixels are identified to be the ridge pixels. Extraction of ridges can
be thinned or cleaned using standard thinning and cormected components
algorithms. 17

iv. Minutiae Detection
After the thinning process is done, the ridge pixels with three ridge pixel
neighbors are identified as ridge bifurcations and those with one ridge pixel
neighbor is identified as ridge endings. However, the minutiae are not
genuine due to image processing artifacts and noise present in the
fingerprint image.
v. Postprocessing
Finally, genuine minutiae are gleaned from the extracted minutiae using a
number of heuristics. For example, too many minutiae in a small
neighborhood may indicate the presence of noise and can be discarded. Very
close ridge endings oriented anti parallel to each other may indicate
spurious minutiae generated by a break in the ridge due to poor contrast or a
cut in the finger. Two closely located bifurcations sharing a common short
ridge suggest the presence of extraneous minutiae generated by bridging of
adjacent ridges as a result of dirt or image processing artifacts.
2.1.5 Fingerprint Matching
The fingerprint is matched by comparing the captured image and the present
image provided by the user. The objective of fingerprint matching is to
determine whether the prints represent the same finger or not. Users are
identified by using several approaches either image based, ridge pattem
based or point (minutiae) pattern based fingerprint representations. The
point pattern matching (minutiae matching) approach facilitates the design
of a robust, simple and fast verification algorithm while maintaining a small
template size.
The matching phase defines the distance metric between two fingerprint
representations and determines whether a given pair of representations is
captured from the same finger (known as mated pair). The determination is
based on whether this quantified distance is greater than a certain threshold.
21Its distance metric or similarity is based on the concept of correspondence in
minutiae based matching. A minutia in the presented fingerprint and a18

minutia in the stored fingerprint template are said to be corresponding if
they are identical.
Characteristics registered for fingerprint matching includes the core, which
approximates the centre of the pattern, and the axis, which represents the
vertical orientation of the finger
Figure 2 3: A fingerprint image showing core, axis marker, and marked
minutae
Chapter 3
19

Project Design and Implementation
The application will employ vb.net on the front-end and Microsoft Access on the back-end.
4.1 Hardware Requirements
(i) Any screen resolution (more than or equal to 800 X 600) would work.
(ii) Pentium IV processor, or above
(iii) Fingerprint scanner – URU4000B
4.2 Software Requirements
(i) Windows XP/Vista
(ii) Microsoft Visual Studio 2008
(iii) Microsoft Access
5.1 Hardware - Software Level Design
Required hardware used should be easy to maintain, implement and easily available.
Proposed model consists following parts:
(1)Fingerprint Scanner,
(2)Computer
Fingerprint scanner will be used to input fingerprint of customers into the
computer software. LCD display will be displaying the facilities that the customer can
avail and make the transactions. Computer Software will be interfacing fingerprint
scanner and LCD. It will input fingerprint, will process it and extract features for
matching. After matching, it will update database entries of the customer and keep
a record of any transaction made by him/her.
20

Figure 2.1: Fingerprint scanner
5.2 Approach
Our system integrate biometric identification into normal, traditional authentication
technique use by electronic ATM machines nowadays to ensure a strong, unbreakable
security and also non-repudiate transactions. In order to demonstrate the strength of our
proposed authentication protocol using the combination of three authentication methods of
card, PIN and fingerprint, we used U.are.U 4000 fingerprint biometrics development kit
manufactured by Digital Persona Software Limited.
The proposed design involves two phases namely registration phase and verification phase.
Each of the phases is briefly describe below.
Registration Phase
Prior to an individual being identified or verified by a biometric device, the registration
process must be completed. The objective of this registration process is to create a profile of
the user. This process is carried out by the administrator of the system. The process consists
of the following two steps:
1. Sample Capture: The user allows three biometric readings by placing a finger on a
fingerprint reader. The quality of the samples, together with the number of samples taken,
will influence the level of accuracy at the time of validation. Not all samples are stored; the
technology analyzes and measures various data points unique to each individual. The
number of measured data points varies in accordance to the type of device.
21

2. Conversion and Encryption: The individual’s measurements and data points are
converted to a mathematical algorithm and encrypted. These algorithms are extremely
complex and cannot be reversed engineered to obtain the original image. This algorithm is
further stored in the database or server.
Figure. Flowchart for the registration process
Identification and Verification - Once the individual has been enrolled in a system, he/she
can start to use biometric technology to have access to his account via the ATM machine to
authorize transactions.
1. Identification: a one-to-many match. The user provides a biometric sample and the
system looks at all user templates in the database. If there is a match, the user is granted
access, otherwise, it is declined.
22

2. Verification: a one-to-one match requiring the user provides identification such as a PIN
and valid ATM card in addition to the biometric sample. In other words, the user is
establishing who he/she is and the system simply verifies if this is correct. The biometric
sample with the provided identification is compared to the previously stored information in
the database. If there is a match, access is provided, otherwise, it is declined.
Figure. Flowchart for the verification process
After the verification process, the user can carry on with his/her transactions such as balance
inquiry, balance withdrawal, balance transfer etc.
3.1 User Interfaces
Administrator interface. Will enable administrator to add new users, view existing
23

users and delete users.
User interface. Will enable users to acess their accounts and make necessary
transactions.
3.2 Operations
The product release covers all automated aspects of the database. The tables in the database
have to be maintained on the server side.
3.3 Product Functions
The System will allow access to two kind of users(administrator and customers).The
administrator shall enter the details of the customers with the primary key being their
scanned fingerprint images . The Log-in times shall be monitored as a real time system,
since as soon as the customer authenticates himself/herself he/she is allowed to make the
required transactions. The system shall have all the transaction details entered into the
database, hence a proper account would be maintained of the customers transactions.
3.4 Constraints
Due to limited features in the Standalone Development, simultaneous log-ins of the Users
(i.e user and Administrator) is not feasible.
3.10 EXTERNAL INTERFACES
(i) Login Screen:
Input: login PIN
Data format: text or numeric
Output destination: Database table
(ii) Registration Screen:
Input: Username , fingerprint image, balance
Data format: text or numeric
Output destination: Database table
24

(iii)Home Page:
Displays the basic information of the user logged in along with the facilities the user can
avail.
Data format : text, numeric , pictorial.
(iv)Withdraw Amount Screen:
Requests you to enter the amount you want to withdraw from your account.
Data format : text, numeric , pictorial.
(v)Balance Inquiry Screen:
Informs you how much balance you have in your account.
Data format : text, numeric , pictorial.
(vi)Mini Statement Screen:
Informs you about your last 5 transactions.
Data format : text, numeric , pictorial.
(vii)Funds transfer Screen:
Requests you to enter the account number and the amount of money you want to transfer to
that account.
Data format : text, numeric , pictorial.
.
5.6 Comparison with other ATM systems
Typically, a user inserts into the ATM a special plastic card that is encoded with
information on a magnetic strip. The strip contains an identification code that is transmitted
to the bank's central computer by modem. To prevent unauthorized transactions, a personal
25

identification number (PIN) must also be entered by the user using a keypad. The computer
then permits the ATM to complete the transaction; most machines can dispense cash, accept
deposits, transfer funds, and provide information on account balances..
Figure. ATM authentication process
Integrating ATM system with the biometric authentication techniques is a solution to avoid
the fraud. Biometric authentication ensures that a person is actually present rather than their
cards and passwords without requiring the user to remember anything. Among all the
biometrics, fingerprint based identification is one of the most mature and proven technique.
Banks can choose different authentication schemes for their customers at their ATM’s ie
single level (only biometric authentication) or dual level authentication (PIN combined with
biometric authentication).
Figure. Proposed prototype
5.7 Fingerprint Identification System
An identification system is one which helps in identifying an individual among
26

many people when detailed information is not available. It may involve matching
available features of customer like fingerprints with those already enrolled in database.
5.7.1 How Fingerprint Recognition works?
Fingerprint images that are found or scanned are not of optimum quality. So we
remove noises and enhance their quality. We extract features like minutiae and others
for matching. If the sets of minutiae are matched with those in the database, we call
it an identified fingerprint. After matching, we perform post-matching steps which
may include showing details of identified candidate, marking attendance etc. A brief
flowchart is shown in next section.
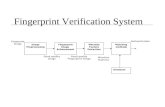
5.8. Fingerprint Identification System Flowchart
A brief methodology of our Fingerprint Identification System is shown here in follow-
ing flowchart. Each of these are explained in the later chapters.
27

Figure 3.1: Fingerprint Identification System
Flowchart
28

1. PLAN AND SCHEDULE
S. NO Set of definable
tasks
Start Date End Date Cost estimated
1. Planning and
reviewing
literature for the
project
10.12.11 23.12.11 Nil
2. Purchasing the
device and
finishing the
design and
coding modules
2.01.12 10.03.12 Rs. 5800
3. Testing and
error correction;
debugging;
Change
management
11.03.12 4.04.12 Nil
4. Report
generation
4.04.12 23.04.12 Rs. 500
TABLE 1: Schedule for the project completion
29

Chapter 4
Simulation
4.1 VB.NET
Visual Basic .NET is one of the two flagship languages (with C#) for the .NET framework
from Microsoft. Despite being called Visual Basic, it is actually not backwards-compatible
with VB6, and any code written in the old version will not compile under VB.NET.
As a language, Visual Basic.NET has the following traits:
Object-Oriented
As with all .NET languages, VB.NET includes full-blown support for object-oriented
concepts, including simple inheritance. Everything in VB.NET is an object, including all of
the primitives (Short, Integer, Long, String, Boolean, etc.) as well as types, events, and even
assemblies. Everything inherits from the Object base class.
Event-Driven
All previous versions of Visual Basic were event-driven, but this feature is heavily
enhanced under the .NET framework. Events are no longer recognized because they use a
certain naming convention (ObjectName_EventName), but now are declared with a Handles
ObjectName.EventName clause. Event handlers can also be declared at runtime using the
AddHandler command.
.NET Framework
As the name implies, VB.NET runs on top of Microsoft's .NET framework, meaning the
language has full access to all of the supporting classes in the framework. It's also possible
to run VB.NET programs on top of Mono, the open-source alternative to .NET, not only
under Windows, but even Linux or Mac OSX.
4.2 Microsoft Access
Microsoft Office Access, previously known as Microsoft Access, is a database management
system from Microsoft that combines the relational Microsoft Jet Database Engine with
a graphical user interface and software-development tools. It is a member of the Microsoft
Office suite of applications, included in the Professional and higher editions or sold
separately. On May 12, 2010, the current version of Microsoft Access 2010 was released by
Microsoft in Office 2010; Microsoft Office Access 2007 was the prior version.30

MS Access stores data in its own format based on the Access Jet Database Engine. It can
also import or link directly to datastored in other applications and databases.[1]
Software developers and data architects can use Microsoft Access to develop application
software, and "power users" can use it to build software applications. Like other Office
applications, Access is supported by Visual Basic for Applications, an object-
oriented programming language that can reference a variety of objects including DAO (Data
Access Objects), ActiveX Data Objects, and many other ActiveX components. Visual
objects used in forms and reports expose their methods and properties in the VBA
programming environment, and VBA code modules may declare and call
Windows operating-system functions.
4.3 U.are.U 4000B Fingerprint Scanner
The U.are.U 4000B is a USB fingerprint reader designed for use with DigitalPersona’s
enterprise software applications and developer tools.
The user simply places their finger on the glowing reader window, and the reader quickly
and automatically scans the fingerprint. On-board electronics calibrate the reader and
encrypt the scanned data before sending it over the USB interface.
DigitalPersona products utilize optical fingerprint scanning technology for superior
quality and product reliability. The U.are.U 4000B Reader and DigitalPersona fingerprint
recognition software engine have an unmatched ability to recognize
even the most difficult fingerprints.
31

Chapter 5
Discussion of Results
32

Chapter 6
Conclusion
Throughout the project, the focus has been on enhancing the process of
identification and authentication on the automatic teller machine (ATM). The
project has proposed the use of the fingerprint as a suitable
substitution for the personal identification number (PIN). This chapter summarizes the
analysis for justifying the use of fingerprint and smart card, then concludes the project and
states future directions.
6.1 The Fingerprint vs. the Personal Identification Number (PIN)
Fingerprints are the most acceptable biometrics all over the world in identifying a
person. It is the characteristic that can prove a person is the person he/she claims to
be. It is also the mature technology for automated identification systems because it
has evolved way back since 1970. Until now some governments in the
world are still implementing fingerprint techniques to identify their citizens, and the
criminal from the scene of crimes in forensic work. In this research, fingerprint is
chosen for its uniqueness, ease of use and also convenience to the user. From the
experience and the analysis on the prototype, the advantages of the fingerprint are
listed below:
a. Fingerprints cannot be stolen, lost or inadvertently passed to others as the
fingerprint is always possessed by its owner.
b. It is not transferable, as it always attached to the body.
c. The user does not have to memorize the fingerprint. The only memory
needed by the user is which finger they need to use to gain access.
d. The uniqueness of a finger can be used repeatedly to gain access to other
applications as well without fear of it being duplicated.
The prototype system has implemented fingerprint identification to carefully identify
the authorized user for accessing the system, gain services offered and access their
account information.
33

From the analysis and experience gained throughout the research, it is found that the
fingerprint technology is the best technology to be used in identifying user. With the
help of the SDK, the implementation of the fingerprint was relatively easy. Without
the SDK, the prototype development process would be time consuming and
complicated.
The prototype system as a whole has integrated the fingerprint technologies for user
identification and authentication in accessing the ATM.
Database used in the research provides some data for the client
system to do the operations normally done by the ATM. Although it is a simple
database, it is adequate enough for the user to carry out the transaction using the
client system.
Even though the system has not been tested using the actual machine, the system was
found to be better than the conventional ATM system based on the advantages
possessed by the main components (i.e., fingerprint). The research
has shown that using ‘something you are’ (i.e., fingerprint), would be a better
identification method rather than using ‘something you know’ (i.e., PIN).
This robust prototype system that relies on some unchanging, difficult to forge entity will
hopefully reduce the ATM vulnerabilities.
34

Chapter 7
Future Prospects
35