Www.jiscinfonet.ac.uk Email or MEmail Alan Cameron Records Management Consultant JiscinfoNet.
-
Upload
gordon-wiggins -
Category
Documents
-
view
213 -
download
0
Transcript of Www.jiscinfonet.ac.uk Email or MEmail Alan Cameron Records Management Consultant JiscinfoNet.

www.jiscinfonet.ac.uk
Email or MEmail
Alan Cameron
Records Management Consultant
JiscinfoNet

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Some propositions
• Email is a person to person communication channel , but it is not the private possession of the end-user.
• Email is the equivalent ‘ ….of sticking a post card on a public notice board……’
• An end-user can commit an organisation to a contract or legal risk
• All Emails created or received within an organisation are legally discoverable
• Email management is a business issue not just an IT problem.

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Three horror stories
• Norwich Union settled out of court for £450k. Employees had exchanged defamatory Emails about a competitor (believed to be an in-joke). By time writ was issued Emails had been destroyed .
• London Law Firm. Litigation still in course. Racial and sexual discrimination as a result of internal Emails. Potentially no top limit on the potential fine.
• UBS Warburg incurred US$206k costs retrieving Emails from IT archive for litigation.

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk Applications Business Requirement
SERVERS, Short term storage Continuous availability24 x 7
Anti-virus, anti-spam, content control, authorization
Security Management
Archive Retention/disposal, search and retrieval
Email archiving
Email blocking, access rights, retention/disposal
Policy Management
Use of folders, agreed file conventions, deletion/save, attachments
End user training/management

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
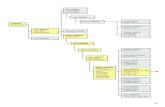
How does an Email system fit with a Records Management system?
Anti-virus & Spam filters
Firewall
Policies and Policy Management
Email SystemSearching and Retrieval
Records Management Systems ?

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
The Storage Problem
• One HE institution with 4,500 staff processes av.45,000 + Emails a day. (not constant, has peaks and troughs)
• It allows free student use. ++?• Email archive , which goes back 3 years is already many
gigabytes, achieved by back-ups daily, and debateable how much could be retrieved
• An Email plus attachment sent to all staff is stored 4,500 times.

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Email Storage; Conflicting Interests?
• IT ADMINSTRATORS limit size of personal mailboxes to contain data
volumes which are growing exponentially • END USERS
Want to keep more that they are allowed Rarely ‘manage’ their in-box Resent Interference in ‘personal’ business
• COMPLIANCE OFFICERS Keep everything ‘just in case’

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
The Search for Solutions
• The IT Answer Looks to major vendors such as IBM and Microsoft to
produce systems answers Automatic indexing and retrieval Cost of storage reducing ‘..therefore a minor issue..’
• The Business Answer Making better use of existing capabilities of Email
systems End-user training Use of corporate file spaces,metadata conventions
etc.

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
The Reality
• The vast majority of Institutions have no strategy for effective management of Email
• All Institutions are therefore vulnerable to legal discovery, fraud, and compliance issues particularly FOI and Data Protection.
• The retention period for an Email is identical to that of a record containing the same information in any other medium.
• Few end-users of Email are aware of their employer’s liability for their Email use.

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Email studies in FE/HE
Only aware of 3
1. University of Central England Case study by the Butler Group
2. Loughborough University Study commissioned by JISC
(contains a generic Email policy document)http://www.loboro.ac.uk/computing/irm
3. Secure E-mail in UK Further and Higher Educationhttp://www.jisc.ac.uk/index.cfm?=jcas_PAPERS_secure_email

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Towards an Email Policy in an Institution
Summary
1. E-mail Management is a corporate responsibility. It is not reasonable to expect the End-User to know what should or should not be deleted/retained
2. It has to operate at 3 distinct levels• As part of overall IT strategy because part of the answer
lies in technical development• A clear policy for all users which is enforced and
monitored• Training in the better use of the facilities contained within
the major Email systems

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
E-Mail Policy Options 1
• Ownership All messages belong to the organisation Only business messages are owned by the organisation Personal messages are jointly owned Personal messages are confidential
• Permitting e-mail Use E-mail only for organisation’s business May be used for incidental personal purposes Personal purposes without restriction

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
E-Mail Policy Options 2
• Encryption None without specific authority Only specified forms of encryption permitted Encrption permitted
• Labelling All personal messages must be labelled as such Messages must disclose limits of employee’s authority Personal messages must carry a specified disclaimer

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
E-Mail Policy Options 3
• Monitoring E-mail may be monitored for any business purpose, without
notice or consent Monitoring permitted with good cause or legal obligation Systematic monitoring with agreed procedures N o monitoring
• Contents Disclosure Messages contents may be disclosed for any business
purpose without consent Disclosure as required by the law Disclosure permitted within agreed procedures No disclosure

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
E-Mail Policy Options 4
• Notification of Monitoring or Disclosure No notification unless required by law or other duty Notification forbidden by the legal process Notifcation after any access or disclosure
• Substantive Rules System may not be used for illegal or wrongful purposes System may not download software without technical
approval System may not be used for electronic snooping

Providing Expertise in Planning &
Implementing Information
Systems
www.jiscinfonet.ac.uk
Any Questions?
Thank You
www.jiscinfonet.ac.uk