Teradata MultiLoad Reference - Home | Teradata Developer Exchange
WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles...
Transcript of WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles...
©2016 Crowe Horwath LLP
Demystifying CybersecurityUnderstanding and Responding to a Growing Risk
Jeff SacksPrincipal (Non-CPA Partner)Technology Risk Group West Region Leader
©2016 Crowe Horwath LLP 22
Agenda
• Introduction: Outcome of Cyber-attacks – Breach of Valuable Information
• What is Cybersecurity?
• Cybersecurity Frameworks and Regulatory Guidance
• InTREx and FFIEC Cybersecurity Tool/Approach
• Breach/Incident Response Planning
• Testing and Insurance
• Company and Board Expectations
©2016 Crowe Horwath LLP 44
1.
•People tend to put every word they are going to say on their PowerPoint slides. Although this eliminates the need to memorize your talk, ultimately this makes your slide look crowded, wordy, and boring. You will lose your audiences attention before you even reach the bottom of your …
©2016 Crowe Horwath LLP 66
2.
•Avoid•Excessive•Bullet-•Pointing.•Only•Bullet•Key •Points.•Too Many•Bullet-Points•And Your •Key Messages •Will Not•Stand Out.
©2016 Crowe Horwath LLP 77
3.
•BAD COLOR SCHEMES•Clashing Background & Font Colors Can Lead To:
• Distraction• Confusion• Headaches• Nausea• Vomiting
©2016 Crowe Horwath LLP 88
4.
•Font Analysis
•COURIER NEW – Organized & Structured
•MISTRAL – Artistic
•TIMES NEW ROMAN – Lazy, Apathetic, Unimaginative (Always Use The Default)
•FREESTYLE SCRIPT – You are a horrible speller so you try to hide it with a hard to read font
•(Wingdings) - (You’re a nerd and you have no life).
©2016 Crowe Horwath LLP 1212
Breaches By The Numbers
• 43% of companies had a data breach in the past year
• Only 15% of all breaches that occur, make the media
• 600-700 breaches reported nationally on an average year
• More than 80% of the breaches “have a root cause in employee negligence”• Misconfiguration/Default Configuration• Lack of Patching• Social Engineering
• Security Awareness Training is Key!
©2016 Crowe Horwath LLP 1414
Cybersecurity Risk Trends
• Cyber Attacks• More frequent, varied, and mobile
• Vulnerabilities continue to persist• Not just 0-day exploits, but known vulnerabilities
• New cyber-attack threats increase as technologies change• Offer new ways to exploit fresh technologies
• Attackers are Evolving• Commercializing tools, resources and infrastructure
©2016 Crowe Horwath LLP 1515
Risk Trends and Impacts for Financial Institutions
• Plethora of available information• Attack ploys utilize online social networks to craft custom and targeted attacks
• Malware strengthens• Malware focused on destruction and has evolved into ransom ware
• Global unrest and changing motivations• Regions intent on harming the U.S will continue to target financial institutions
• Impacts• Financial• Operational• Legal • Reputational
©2016 Crowe Horwath LLP 1616
Common Breach Vectors
• Viruses – A computer virus is a malware program that, when executed, replicates by inserting copies of itself (“infecting”) into other computer programs, data files, or the boot sector of the hard drive. Viruses often perform some type of harmful activity such as stealing hard disk space or CPU time, accessing private information, corrupting data, displaying messages on the user's screen, spamming contacts, or logging keystrokes.
• Vulnerabilities• Heartbleed (more data is read than should be allowed – theft of keys, cookies, and
passwords. 17% of Internet servers vulnerable)• Shellshock (execute arbitrary commands which allows a hacker to gain unauthorized
access to computer systems)• SQL Injection (a code injection technique, used to attack data-driven applications, in
which malicious SQL statements are inserted into an entry field for execution )
• Stolen/re-used credentials (User ID’s & Passwords)
©2016 Crowe Horwath LLP 1717
Attack Scenario
Initial Point of EntryThe Point of Entry represents how the attacker obtains initial access. Examples could include social engineering, unpatched Internet accessible systems, or weak passwords on externally accessible systems.
Fortify Access and Access DataAs the attacker pivots around the network, they continue to attempt to escalate their authority until they have the necessary access. They will typically fortify their access by installing malware or backdoors to maintain access. The administrator credentials the attacker obtained likely has authority to the cardholder network, where they can install card harvesting malware to capture credit card data.
Pivot PointThe initial access typically does not provide the information the attacker is looking for. They will leverage the access they do have to try to increase authority on the network. This could be occur through shared passwords, unpatched systems, or excessive privileges. For example, attackers often leverage misconfigured devices and shared passwords to eventually obtain domain administrator authority.
Data ExfiltrationOnce the attacker has data, they need to get it out of the network. This can be completed through email or FTP. Malware can write the cards to a temp file on the database, which can then be copied to a server, then to a workstation that has Internet access, where it can be sent via FTP to the attacker (DATA LOSS PREVENTION)
©2016 Crowe Horwath LLP 1818
How Do Breaches Happen?
Target Example
• Point of Sale Malware• Kartoxa POS Malware author - Rinat Shabaev was looking for
a regular programming job asking for $12 / hour• After failing to find any significant project work, he turned to the
hacker community to use his skills to write malware
• Breach planned for several months
• Botnet breach of an HVAC vendor
• After extensive testing, performed breach a week before Black Friday
• Two weeks of data collection before putting the data up for sale
©2016 Crowe Horwath LLP 1919
How Do Breaches Happen?
Anthem Example
• Credentials compromised of at least five different employees• At least 1 was that of an administrator
• LinkedIn job profiles clearly noted Teradata as data warehouse technology.• Additional LinkedIn searches identify CXO’s, architects, and DBA’s.
• Credentials compromised through “phishing”
• Gained access to database credentials
• Use of “sophisticated malware” to evade anti-virus products
• Encryption would not help as logical access controls were weak (Preventive)
• Database activity monitoring not in place (Detective)
©2016 Crowe Horwath LLP 2020
The Dark Web
• Marketplace for stolen data – aka the “Dark Web”• Credit Cards• Health Records• Financial Information• Personal Information• Usernames and Passwords
©2016 Crowe Horwath LLP 2424
Cybersecurity or Information Security?
• Many are still asking and many still have differences of opinion.
• Cybersecurity is the protection of information in the cyber “space”
• IT Security (same as cybersecurity)
• Information Security/Assurance is the protection of information in all forms; intellectual, hardcopy, softcopy/electronic
©2016 Crowe Horwath LLP 2525
Simplest Definition of Cybersecurity
• “Measures taken to protect a computer or computer system (as on the Internet) against unauthorized access or attack.”
• Who does it impact?• Anyone, individual or organization, connected to the internet
©2016 Crowe Horwath LLP 2626
Trends in cybersecurity – “The Internet of Things”
• Everything has an IP• HVAC• Cars• Garage Door Opener• Refrigerator• Webcams• Washers• Hot Tubs• Light Bulbs
©2016 Crowe Horwath LLP 2828
The NIST Cybersecurity Framework
• Framework Core• Functions
• Identify• Protect• Detect• Respond• Recover
• Categories• Subcategories• Informative References
©2016 Crowe Horwath LLP 2929
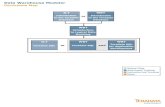
IdentifyIdentify
• Asset Management
• Business Environment
• Governance• Risk
Assessment• Risk
Management Strategy
• Asset Management
• Business Environment
• Governance• Risk
Assessment• Risk
Management Strategy
ProtectProtect
• Access Control• Awareness and
Training• Data Security• Information
Protection Processes and Procedures
• Maintenance• Protective
Technology
• Access Control• Awareness and
Training• Data Security• Information
Protection Processes and Procedures
• Maintenance• Protective
Technology
DetectDetect
• Anomalies and Events
• Security Continuous Monitoring
• Detection Processes
• Anomalies and Events
• Security Continuous Monitoring
• Detection Processes
RespondRespond
• Response Planning
• Communications• Analysis• Mitigation• Improvements
• Response Planning
• Communications• Analysis• Mitigation• Improvements
RecoverRecover
• Recovery Planning
• Improvements• Communications
• Recovery Planning
• Improvements• Communications
Who Does What? – Framework Functions
Primarily Info Sec Controlled
©2016 Crowe Horwath LLP 3030
This Is Overwhelming - What Can I Do?
• All of the frameworks say the same thing:• Know your data• Assess your data controls with a risk
assessment• Remediate by implementing security controls• Repeat
• There are so many frameworks and expectations, how do I consolidate everything that applies to me?
• Answer: Unified Controls Frameworkhttps://www.unifiedcompliance.com/
Identify Data
Assess Controls
Remediate Controls
©2016 Crowe Horwath LLP 3232
InTREx – FDIC’s “Information Technology Risk Examination Program”
• Released on July 1, 2016 – Regulators are already asking for it!
• Changes the way FDIC exams take place – ratings in various I.T. risk areas will be combined for an overall composite I.T. rating.
• Financial institutions complete InTREx questionnaire 90 days before the I.T. exam to help examiners determine scope and resources needed
• Questionnaire focuses on • Cybersecurity• Emerging risks & technologies (i.e. – virtualization and mobile banking)• Previous I.T. risk management efforts and reviews• Core processing, network, online banking, development & programming, software & services, audit,
management, support & delivery, information security,
• Preparation• Review InTREx program information• Have I.T. assign dedicated personnel to address the changes and complete the InTREx pre-exam questionnaire• Gather recent I.T. internal audit reports, ratings, and management remediation/action plans
©2016 Crowe Horwath LLP 3333
Cybersecurity Assessment Tool
• Released on June 30, 2015
• New framework for assessing and improving cybersecurity preparedness within financial institutions
• Developed in response to increasing volume and sophistication of cyber threats targeting the financial sector
• Consistent with NIST Framework and FFIEC I.T. Handbook
• Voluntary??? Regulators are asking for it!!!
https://www.ffiec.gov/cyberassessmenttool.htm
©2016 Crowe Horwath LLP 3434
Cybersecurity - Regulatory Expectations
• Builds upon the FFIEC IT Handbook, to include:
• Assessing complexity of the institution’s IT environmentand how it’s IT services are managed (INHERENT RISK & MATURITY LEVEL)
• Assessing an institution’s current and overall cybersecuritypreparedness.
©2016 Crowe Horwath LLP 3535
Cybersecurity Assessment Tool – INHERENT RISK
• How much cybersecurity risk an institution has, before implementing controls
• Calculated across 39 factors based on complexity, volume, and type of technologies in use
• Based on 5 categories:• Technologies and Connection Types• Delivery Channels• Online/Mobile Products and Technology Services• Organizational Characteristics• External Threats
©2016 Crowe Horwath LLP 3636
Inherent Risk Levels
• There are five risk levels across each activity/technology• Least Inherent Risk• Minimal Inherent Risk• Moderate Inherent Risk• Significant Inherent Risk• Most Inherent Risk
Least Inherent Risk
Minimal Inherent Risk
Moderate Inherent Risk
Significant Inherent Risk
Most Inherent Risk
©2016 Crowe Horwath LLP 3737
Cybersecurity Assessment Tool – MATURITY ASSESSMENT
• After Inherent Risk is determined, the institution assesses their Cybersecurity Maturity within 5 domains:• Cyber Risk Management and Oversight• Threat Intelligence and Collaboration• Cybersecurity Controls• External Dependency Management• Cyber Incident Management/Resilience
• Each domain has assessment factors and contributing components
• Overall, there are 494 controls to assess
©2016 Crowe Horwath LLP 3838
Cybersecurity maturity levels
• There are 5 levels of maturity that can be obtained in each domain• Baseline• Evolving• Intermediate• Advanced• Innovative
Advanced
Intermediate
Evolving
Baseline
©2016 Crowe Horwath LLP 3939
Cybersecurity Maturity Levels
• It is important to note that all assessment controls must be met in the current and previous maturity levels to meet that maturity
• For example:• If all Advanced (level 4) controls are in place, but there is one Evolving (level 2)
control missing, the Maturity Level is only considered Baseline (level 1)
©2016 Crowe Horwath LLP 4040
Inherent Risk/Maturity Relationships – Analyzing the Results
• After assessing Inherent Risk and Maturity Levels, an institution can understand whether they are aligned
• This is determined in part by an institution’s appetite for risk
©2016 Crowe Horwath LLP 4242
Be Prepared – Incident Response Planning
• 27% of companies don’t have a breach response plan or team in place• 37% have not reviewed or updated their plan since it was created
WHAT TO ASK• What will I do?• What are the laws?• What will my regulator say?• How much will my customers ask?• Who will I call?• How do I stop it?
©2016 Crowe Horwath LLP 4343
Incident Response Planning (IRP) – Key Items
1. Understand your “Data” before creating an IRP. In other words determine data that you are trying to protect and the level of protection. Knowing this and the ways that data can be accessed is important for developing the appropriate response
2. Inventory incidents or scenarios and classify them into manageable categories or buckets3. Understand the threats that you are likely to face – start off with “known” threats and then create a
source for new and emerging threats for on-going monitoring4. Determine the stakeholders and define the IR “TEAM”. At a minimum this team should include:
• Corporate Communications• Legal• Compliance• Line of business representative(s)• IT• External Forensics Partner or Vendor
5. Set up a “Command Center” and Command Center Leader – could be a conference room6. Incident – containment and investigation strategy7. Evidence preservation strategy8. Overall communication plan including customers, media, federal and state agencies9. Conduct a post-mortem or lessons learned and update IRP procedures
©2016 Crowe Horwath LLP 4747
Undertake Some Testing – Find Your Weaknesses (Penetration [Not Vulnerability] Assessments)
• External Penetration• Technical Services Review (EPA)• Web Applications• Stealth/Blind Penetration (Incident Response)• Remote Social Engineering
• Email/Telephone/Social Media
• Internal Penetration Test• Technical Services Review (IPA)• Onsite Social Engineering/Physical Security Review/USB Drop
• Data Loss Prevention (DLP)• What channels can we utilize to get data out? Can it be
detected?
• Wireless Testing
©2016 Crowe Horwath LLP 4848
Cybersecurity Insurance
• A robust cybersecurity insurance market could help reduce the number of successful cyber attacks by: • Promoting the adoption of preventative measures in return for more coverage• Encouraging the implementation of best practices by basing premiums on an
insured’s level of self-protection
• Be aware• Insurers can be selective in the type of “incidents” they cover
• Detailed control questionnaires can lead to inaccurate figures during and ultimately denied claims
• Costs• Cyber insurance premiums cost, on average, between $50,000 and $100,000
a year for $10 million worth of coverage
©2016 Crowe Horwath LLP 5050
Cybersecurity – A Boardroom Conversation
• Personal Experience• 75% of the boards asked about standards such as:
• FFIEC Requirements• NIST Cybersecurity Framework• ISO 27001 Standards
• Another common theme• How do we know we are not the
next “Target”?
• Boards requiring annual "health check" reports that include descriptions and updates on every aspect of cyber protection
©2016 Crowe Horwath LLP 5151
Cybersecurity - A Boardroom Conversation
• Recent ISACA and IIA Research Foundation Report
• Cybersecurity: “What the Board of Directors Needs to Ask”
• Does the organization use a security framework?• What are the organization's top five cybersecurity risks?• How are employees made aware of their cybersecurity role?• Are external and internal threats considered when planning a cybersecurity program?• How is cybersecurity oversight managed in the organization?• If a breach occurs, is there a strong response protocol?
©2016 Crowe Horwath LLP 5252
Final Thoughts – Conclusion - Guidelines
• Approach cybersecurity as an enterprise-wide risk management issue, not just an I.T. issue.
• Understand the legal implications of cyber risks as it relates to a company's specific situation.
• Have adequate access to cybersecurity expertise and discuss cyber-risk management regularly.
• Establish a risk management framework with adequate staffing and budget.
• Identify which risks to avoid, accept, mitigate, or transfer (through insurance) along with action plans for each tactic.
©2016 Crowe Horwath LLP 5454
In accordance with applicable professional standards, some firm services may not be available to attest clients.
This material is for informational purposes only and should not be construed as financial or legal advice. Please seek guidance specific to your organization from qualified advisers in your jurisdiction.
© 2016 Crowe Horwath LLP, an independent member of Crowe Horwath International crowehorwath.com/disclosure
Jeff Sacks, PrincipalPhone [email protected]
Thank you
![Page 1: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/1.jpg)
![Page 2: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/2.jpg)
![Page 3: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/3.jpg)
![Page 4: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/4.jpg)
![Page 5: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/5.jpg)
![Page 6: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/6.jpg)
![Page 7: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/7.jpg)
![Page 8: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/8.jpg)
![Page 9: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/9.jpg)
![Page 10: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/10.jpg)
![Page 11: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/11.jpg)
![Page 12: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/12.jpg)
![Page 13: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/13.jpg)
![Page 14: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/14.jpg)
![Page 15: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/15.jpg)
![Page 16: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/16.jpg)
![Page 17: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/17.jpg)
![Page 18: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/18.jpg)
![Page 19: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/19.jpg)
![Page 20: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/20.jpg)
![Page 21: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/21.jpg)
![Page 22: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/22.jpg)
![Page 23: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/23.jpg)
![Page 24: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/24.jpg)
![Page 25: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/25.jpg)
![Page 26: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/26.jpg)
![Page 27: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/27.jpg)
![Page 28: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/28.jpg)
![Page 29: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/29.jpg)
![Page 30: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/30.jpg)
![Page 31: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/31.jpg)
![Page 32: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/32.jpg)
![Page 33: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/33.jpg)
![Page 34: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/34.jpg)
![Page 35: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/35.jpg)
![Page 36: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/36.jpg)
![Page 37: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/37.jpg)
![Page 38: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/38.jpg)
![Page 39: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/39.jpg)
![Page 40: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/40.jpg)
![Page 41: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/41.jpg)
![Page 42: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/42.jpg)
![Page 43: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/43.jpg)
![Page 44: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/44.jpg)
![Page 45: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/45.jpg)
![Page 46: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/46.jpg)
![Page 47: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/47.jpg)
![Page 48: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/48.jpg)
![Page 49: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/49.jpg)
![Page 50: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/50.jpg)
![Page 51: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/51.jpg)
![Page 52: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/52.jpg)
![Page 53: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/53.jpg)
![Page 54: WTB Conference Cybersecurity Speech-FINAL! [Read-Only] · 2016-09-26 · • LinkedIn job profiles clearly noted Teradata as data warehouse technology. • Additional LinkedIn searches](https://reader042.fdocuments.us/reader042/viewer/2022041106/5f08935e7e708231d422b0a0/html5/thumbnails/54.jpg)