Welcome to the SafeNet Executive Day! · And then, there‟s the data itself! How secure is my data...
Transcript of Welcome to the SafeNet Executive Day! · And then, there‟s the data itself! How secure is my data...

Welcome to the
SafeNet Executive
Day!
Новые
ГоризонтыИнформа
ционной
Безопасности

Новые Горизонты Информационной
Безопасности
Сергей Кузнецов
Глава Представительства,
SafeNet Европа Б.В. в
России&СНГ

Спонсоры и Участники
Платиновые Спонсоры
• СИС (Сертифицированные Информационные
Системы)
• Demos
Спонсоры и Участники
• IndeedID
• УЦСБ
• DPS (Data Protection Systems)
3

Выводы (Takeaways)
SafeNet 2013 – Представление Новой Компании Safenet в России
У нас есть ответ новым технологическим вызовам современности:
• Виртуализация
• Мобильность
• Облачные вычисления
• Большие Данные
Продолжение инвестирования в Коренной бизнес:
• eToken/iKey, Сертификация ФСТЭК
• HSMs/HSEs, Новые возможности
• DataSecure, Виртуальное устройство
SafeNet в России – серьезные планы по инвестициям:
• Персонал
• Локализация/Сертификация решений
• Доступность обучения
4

Что Вы можете найти в Демо зонах?
Виртуализация
• Стенд УЦСБ Protect-V с Виртуальным устройством KeySecure
• Живая презентация Rami Shalom в секции Protect-V
Мобильность
• Аутентификация – Зона СИС/Safenet
• Интеграция средств Аутентификации с решением Single Sign On –
Стенд IndeedID
Облака
• SAS (Safenet Authentication Service) + Protect Virtual – Стенд УЦСБ
• Crypto HSM – Стенд DPS, Зона Demos/Сейфнет
Большие Данные
• Токенизация – Секция Tokenization
• Storage Secure – Зона Demos/Safenet
• HSE/Senetas – Зона Demos/Safenet
5

SafeNet изменяет привычный рынок
Аутентификация как Сервис (SAS):
• Переход от Капитальных Инвестиций к Операционными Расходам
• Масштабируемость и адаптивность – как часть дизайна решения
• Опция Частного Облака
Безопасность – по прежнему #1 среди барьеров по адоптации и
внедрению Виртуализации (Forrester)
• Первое доступное Энтерпрайз решение. Возможность использования Облачных
Сервисов
HSM – может быть «Виртуализирован»
• Централизация управления, Консолидация ресурсов, Уменьшение времени
предоставления ключей
Storage Secure : защита NAS, самого быстро растущего сегмента
Хранилищ Данный
• Возможность превращения хранилища в Защищенный Облачный Сервис (WEP,
WepDAV)
6

Текущий Статус в России
7
СИС: • Дистрибутор решений Аутентификации
• SAS – контракт в процессе подписания
• Protect-V – контракт в процессе подписания
• Центр Компетенции/Субдистрибутор – Aladdin RD
Demos
• Дистрибутор HSM/HSE
• Storage Secure – в процессе обсуждения
• KeySecure – в процессе обсуждения
• NetApp Дистрибутор NetWell
RAINBOW
• Дистрибутор DataSecure
Модель продаж : Дистрибутор – Партнер – Заказчик

Спасибо

9
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

13:30 – 14:30 Обед
Тематические
сессии, часть
1
Сессия 1: SafeNet
Authentication Service
Сессия 2:
Storage Secure
Сессия 3: Hardware
Security Modules
14:30 – 15:15 Ведущие:
Джэйсон Харт, SafeNet,
Михаил Рожнов,
CertSys
Ведущие:
Рами Шалом, SafeNet,
Андрей Лаптев,
SafeNet
Ведущие:
Герман Бауэр, SafeNet,
Владимир Дегтярев, Demos
15:15 – 15:25 Вопросы и ответы Вопросы и ответы Вопросы и ответы
15:25 – 15:50 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
Тематические
сессии, часть
2
ProtectV
Data Secure:
Tokenisation
Solution Demo
Hardware Security Module
EFT
HSE/Senetas
15:50 – 16:35 Ведущие:
Рами Шалом, SafeNet,
Михаил Рожнов,
CertSys
Ведущие:
Марко Бобинак,
SafeNet,
Андрей Лаптев,
SafeNet
Ведущие:
Владимир Дегтярев, Demos
16:35 – 17:00 Вопросы и ответы Вопросы и ответы Вопросы и ответы
17:00 – 18:00 Закрытие мероприятия. Коктейли
10
Программа мероприятия

Corporate Brief &
Presence in Russia &
CIS
Gary Clark
VP EMEA Sales &
Operations, SafeNet

IT Landscape is at a Tipping Point
Consumerization of IT
Shift in Service Deliver
Models
Proliferation of Data to the
Cloud
Increasingly Complex
Threat Landscape

A New Mindset is Needed
Sole Perimeter Security is
No Longer Enough
Breaches Will Happen and
We Must Prepare
Differently
Data is the New Perimeter

State of Data Protection:
Protect What Matters, Where it Matters

SafeNet: The Data Protection Company
We protect the most
money that moves
in the world, $1
trillion daily.
We protect the most
digital identities in
the world.
We protect the
most sensitive
information in
the world.
FOUNDED
1983
REVENUE
~500m
EMPLOYEES
+1,400 In 25
countries
GLOBAL
FOOTPRINT
+25,000 Customers in
100 countries
ACCREDITED
Products certified
to the highest
security standard
Trusted to protect the world‟s most sensitive data

2004
2009
2003
2003
2004
2005
2008
2012

SafeNet: Where We Focus
Identity and Transaction Protection
Data Encryption and Control
Secure Communications
Compliance and Governance
Data Protection in Cloud & Virtual
Environments
Solutions Markets
Enterprise
Government
Software
Publishers &
Cloud
Service Providers
Device and
Equipment
Vendors Software Monetization
Solutions
Data Protection
Solutions
Software licensing and entitlement
management
Cloud service provisioning, control,
management and usage tracking
Software piracy prevention and IP
protection

Technology ISV & Software
Publishers
Retail
Healthcare Government Financial Services
Representative Global Customers
UK Government
SafeNet: Who We Secure

CIS Customers Trusting SafeNet

…and We Are Ready
Comprehensive Information Lifecycle Protection More ways to protect data than any other vendor- in Databases,
Applications, File Servers, Mainframes, Desktops, Cloud, Virtual
and Mobile.
Trusted by Largest Organizations for Critical Data Proven track record of protecting critical data and transactions –
trillions of dollars in bank transfers, stored streaming videos, and
from M1 tanks to Air Force One.
Confidence with the Most Certified Solutions SafeNet has more FIPS 140-2 and Common Criteria certifications
than any vendor, giving peace of mind to our customers.
High Performance for High Volume Deployment For the largest enterprise deployments - dedicated hardware and
optimized software scales to millions of protected records and
trillions of transactions.

Спасибо

22
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям
для шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

Data protection in the
age of Cloud and
Virtualization
Rami Shalom, VP, DEC
Product Management,
SafeNet

State of Data Security
Security
professionals
believe they will
suffer a breach.
*Based on a SafeNet Survey of 230 security professionals.

State of Data Security
Organizations
continue to rely
on the same
technologies.
*Based on a SafeNet Survey of 230 security professionals.

State of Data Security
Doubt in security
industry‘s ability
to detect and
prevent breaches.
*Based on a SafeNet Survey of 230 security professionals.

State of Data Security
Recognition that if
perimeters failed,
high value data
would not be safe.
*Based on a SafeNet Survey of 230 security professionals.

Cloud migration has a lot to do with it…

Loss of Control Creates New
Security and Compliance Concerns
29
[wrt Virtualization, Forrester] The
insider threat elevates privileged user
management to a whole new level: "I'll
see your domain admin and raise you
one virtualization admin account.‖

My Datacentre
• My Facility
• My machines
• My admins
• My control
• My responsibility
• My accountability
Finance Compliant Customer Regulated Data
Development
Cloud - Starting Point

Direction

Financial: 70% Reduction in IT Infrastructure spend (VMware)
Quality: Automation reduces the volume of
incidents by 27%, and event and incident handling
time by 40% (VMware)
Agility: Provisioning in minutes (from weeks!)
Value

Destination
33 © SafeNet Confidential and Proprietary
Our Datacentre • Our facility
• Our machines
• Our admins
• Our control
• Our responsibility
• My accountability
Their Cloud • Their facility
• Their machines
• Their admins
• Their control
• Their responsibility
• My accountability
Finance Compliant
Customer Regulated Data
Development
Finance Compliant
Customer Regulated Data
Development

Cloud Adoption and Security Concerns
Creating the Perfect Storm
34
Cloud adoption nascent but
soaring b/c of ROI potential
IaaS alone $2.4B -> $6.8B 3 years
Security concerns are the
overwhelming #1 concern for
moving to the cloud.
451 Group, August 2012 report

Who Said?
35 © SafeNet Confidential and Proprietary
―Despite the acknowledged benefits of cloud computing,
wide scale deployment of cloud computing services can
trigger a number of data protection risks, mainly a lack of
control over personal data as well as insufficient
information with regard to how, where and by whom the
data is being processed/sub-processed.‖
It is an independent European advisory body on data
protection and privacy. Its tasks are described in Article 30 of Directive
95/46/EC and Article 15 of Directive 2002/58/EC.
ARTICLE 29 DATA PROTECTION WORKING PARTY
Opinion 05/2012 on Cloud Computing Adopted July 1, 2012

The risk.

Securing The Traditional Infrastructure
Involves securing:
• Datacenter Facilities (Locked doors, alarms, surveillance cameras)
• Physical Network (Firewalls, Routers, VPNs, IDS & IPS)
• Physical Storage (Separate networks, wipe drives)
• Physical Servers (OS updates, disable services, antivirus, enable logging)
• Applications (Apply security patches, run with minimal system privileges)
• Users/Administrators (Directory Services, logging, force password resets, enable two-factor authentication)

Virtualization Introduces Additional
Components to the Datacenter
Datacenter Facilities
Physical Networks
Virtual Networks
Physical Storage
Virtual Storage
Physical Servers
Hypervisor
Virtual Machines
Applications
Users/Administrators
Virtual Administrators

Virtualization Vulnerabilities
39

Securing the Virtualization Layer
Virtual Networks
Virtual Storage
Hypervisor
Virtual Machines (VM)
Virtual Administrators
Management Isolation Jumpbox, indirect access
Administrator Isolation Domain admins, protect root
Virtual Machine Isolation Protect multiple VMs per host
Hypervisor Hardening Follow hardening guide, apply
security updates, host-firewall
Storage Isolation Restrict access, enable Chap for
iSCSI, separate network/vlan.
Network Isolation Separate vMotion, FT, storage,
mgmt and VM traffic, disable
promiscuous mode, VM traffic may
not reach physical network, logical
controls needed

Additional Challenges of Data Center
Consolidation VM VM VM VM VM VM
Physical
Server with
restrictive
security
policy
Physical
Server with
permissive
security
policy
A restricted workload can move from a secure physical
server to an unsecure one without the security admin‘s
knowledge!
Traditional physical security policies do not translate well to a virtual
environment. VMs are more dynamic than physical servers. How can they
be secured without creating air gaps and lowering our ROI.
Multiple copies of the VM exist that can be instantiated without anyone‘s
knowledge if removed from the environment.
Revoking access to sensitive data in the event of a breach is a far
more difficult problem on VMs than on physical servers.

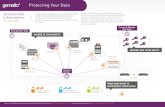
And then, there‟s the data itself!
How secure is my data in a virtualized world?
VMs are easy to copy (and steal.)
Virtual data objects are easy to
move.
Cloud introduces a new class of
privileged users and
administrators—server, storage,
backup, and application—all
operating independently.
VMs have multiple instances,
snapshots and backups of data.
APP APP APP APP
OS OS OS OS
Hypervisor
Compute Layer
Storage
Backup
Snapshots Snapshots
Shredding data capability if
data at risk or switch providers

Who Secures the Cloud?

Challenges in Virtual Datacenters & Clouds
Are all my data instances secure?
How will encryption affect my virtualization solution?
Can I assure only authorized access ?
Can I ―pull the plug‖ on data at risk of exposure?
Data Protection
Prevent leaks or unauthorized access
Who is accessing my data?
Can I enforce an effective access control policy?
Can I present a trusted audit trail?
Control
Set effective access policies
Where are all my data instances?
Can I trace every legitimate copy/ instantiation?
Can I trace unauthorized copying?
Visibility
Where is your data and what is it doing

Control versus Accountability?
“An organization cannot outsource accountability. Ever.” -Cloud Security Alliance
“…outsourcing maintenance of controls is not the same as
outsourcing responsibility for the data overall.” -PCI DSS Cloud Computing Guidelines v2
“…Regarding third-party or public clouds, clients should
consider that while they can outsource the day-to-day
operational management of the data environment, they retain
responsibility for the data they put in the cloud.” -PCI DSS Cloud Computing Guidelines v2

The solution.

State of Data Protection:
Protect What Matters, Where it Matters

WHERE IS YOUR DATA? WHERE ARE YOUR KEYS?
Virtual Machines
File
Server
s
Databases
Site-to-site
Data in Motion
Applications
SaaS Apps
Live Data
1
Virtualized Data
3
Key Management
and Root of Trust
4
Access
5
Stored Data
2
Warning
• Pockets of Encryption
• Operational Inefficiencies
• Audit Deficiencies & Failures
• Sensitive Data Exposure
Protecting What Matters, Where it
Matters

Virtual Machine
SafeNet Solutions for Virtualized
Architectures
Virtual Machine Virtual Machine
Compute Storage Network
Virtual
Compute
CPU
Virtual
Storage
NAS / SAN
Man
ag
em
en
t
Root-of-
trust and
trusted
crypto
Database As-
A-Service
Isolation of
virtual
machines
Strong
Authenticatio
n
Application
Guest OS
Application Application
Guest OS Guest OS
Virtual
Network
Physical
Network
Storage
Encryption
Hypervisor

ProtectV Maintain Control of Your Data Through Your Virtualization
and Cloud Migration
ProtectV Manager VM
VM
ProtectV enables VM encryption to:
• Isolate Virtual Machines and Storage
• Authorize server launches with StartGuard
• Track key access to all copies of your data
• Revoke key access after a breach No need for special discovery of sensitive data
• All data is encrypted, even in archive (ex: snapshots, backups & clones)

StorageSecure Isolate Data in Multi-tenant NAS Environments
51
Health
Solutions
Storage Head
Isolated Data
Shares
Pharmaceutical
Solutions
Patient
Relationship
Medical-
Surgical
•Encryption-enabled separation of data in shared virtual environments
•Separation of inter and intra departmental data
•Protect data belonging to security sensitive departments
•Enables hosting multiple customers on the same HW

Hardware Security
Module (HSM)
Applications
Virtual Machines
Backup
Media
Storage
KeySecure
SafeNet Key Management
Heterogeneous
Open standards-based
Physical or virtual
High assurance

Why Customers Choose SafeNet
Comprehensive Information Lifecycle Protection More ways to protect data than any other vendor- in Databases,
Applications, File Servers, Mainframes, Desktops, and more.
Trusted by Largest Organizations for Critical Data Proven track record of protecting critical data and transactions –
trillions of dollars in bank transfers, stored streaming videos, and
from M1 tanks to Air Force One.
Confidence in the Most Certified Solutions SafeNet has more FIPS 140-2 and Common Criteria certifications
than any vendor, giving peace of mind to our customers.
High Performance for High Volume Deployment For the largest enterprise deployments - dedicated hardware and
optimized software scales to millions of protected records and
trillions of transactions.

Спасибо

55
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в
числе первых, перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

Authentication As A
Service
Why new Cloud based
Authentication solutions
will be adopted by about
50% of the companies by
2017?
Jason Hart CISSP CISM
VP Cloud Solutions

What a great world

Remote Users Internal people 3rd Party Access Branch Offices PDA Users
Users and their workspaces
Today's World
Cloud Applications SaaS Apps

Virtual Word – With Virtual Back Doors
Welcome to the Future
Cloud Computing
Virtual Environment
With Virtual Security holes
During the past 15 years with learnt nothing

We have forgotten
Confidentiality
Integrity
Availability
Accountability
Auditability
We have not learnt
a thing?

Welcome to the 3rd Age of Hacking
• 1st Age: Servers • Servers
• FTP, Telnet, Mail, Web.
• These were the things that consumed bytes from a bad guy
• The hack left a foot print
• 2nd Age: Browsers: • Javascript, ActiveX, Java, Image Formats, DOMs
• These are the things that are getting locked down
– Slowly
– Incompletely
• 3rd Age: Mobile devices: Simplest & getting easier • Target the mobile devices to gain someone's password is the
skeleton key to their life and your business
• Totally invisible – no trace

Password Attack
Welcome to the Future of Hacking
Attack channels: web, mail, open services
Targeted attacks against users and business and or
premium resources
Password attack is totally invisible to you
Mobile devices are becoming an easy target for
Advanced persistent threats (APT)

During the Past 7 Days
63


Quoted from the report:
“…..So, it really comes as no surprise that authentication based attacks (guessing, cracking, or reusing valid credentials) factored into about four of every five breaches involving hacking in our 2012 dataset. …
“... 66% of the breaches in our 2013 report took months or even years to discover (62% months, 4% years).”
Verizon‟s annual Data Breach

www
Probe requests
Pro
be r
eq
ue
sts
Live Attack A g a i n s t y o u r V i r t u a l W o r l d . . . . A R P A t t a c k

Protect Everything with SAS
67 67
Online
Storage
Application
Hosting
SAML
Tokens &
Users
Administrator
Agent
RADIUS
API
Private Networks
Corporate
Network
Corporate
Network
Corporate
Network
Corporate
Network
LDAP / Active
Directory
LDAP / Active
Directory
LDAP / Active
Directory
LDAP / Active
Directory
Private Cloud
Services
Public Cloud
Applications
Collaboration
Tools
SAML SAML

SafeNet Authentication:
Provides the ability to rapidly scale, deploy authentication
Simple, easy and low-cost, driving strong authentication into all markets
The most powerful enterprise authentication server in the market
Offer a multi-tenant, multi-tier authentication platform that allows an
almost infinite number of ―virtual‖ authentication servers for you
business

More than Authentication
Automate Service Delivery - features include a policy engine that can automatically provision, suspend or revoke tokens based on changes in the user repository
Scheduled Automated Usage - Audit and Billing Reports
Branding - You can brand everything - Self-service, enrolment and messaging services.
Token Selection - The widest range of authentication token options

More than Authentication
Security - Customers can define their own security controls
and policies
Multi Tenant - The only true Multi Tier platform in the world
Multi Tier - manage centrally or fully devolve all
administration
Service Alerts - Full Automation of user and administrator
alerts
API - Detailed API sets for authentication and administration
Open platform – Every enterprise is different – full
customisation to meet your needs

Multi-tenant architecture • Scales to thousands of business units
• Unlimited numbers of users per business unit
Manage multiple business units from one centralised interface • Unlimited numbers
• Supports multiple domains
Secure • Only view one level down
• Isolation & Access Control
Delegated management for lower tiers • Deliver enhanced service wrappers
• Great for multi-region networks
Inherit capabilities to lower level • SMS / SMTP gateways
• Branding
Virtual Service Provider
Subscriber B
Managed Subscriber
Subscriber A
Enterprise Subscriber (Virtual Service Provider)
Region 1
Region 2
Region 3
Delegated
Multi-Tenant Multi-Tier – Overview

Multi-tenant architecture
• Unlimited Domains
• None Directory stores
• Localisation
Automation
• User fulfilment – Provisioning, Enrolment etc
• User Self healing
• Reports
Secure
• The ability to Manage clients if rights granted by
Client
Branding and region
• Adding of custom SMS Gates
• Everything can be fully Branded
Features
• Meets all markets requirements
Division 1
Regional Office
Helpdesk
Multi-Tenant Multi-Tier
Division 2
Division 3
Division 4
HR
Your Enterprise

Flexibility and Customisation
• Language - by region or Admin
• Alert messages – including language
• SMS Gateways - by region
• Branding - Even by region or business unit
• OTP policy - Even by region or user base
• User experiences
• Role Management
• Reporting
• Pretty much everything
• Even the service you would like to offer

Example Flexibility
SAS offers full automation,
including:
• Token provisioning
• Security rules definition engine
• Once created rules applied
automatically
• Alerts
• SAML service registration
• Self enrolment
• Self service
• Reporting
LDAP
Changes
Auto Update
SAS
Auto-
Provision
User
Self-
Enrollment
Reporting
and Alerts

LDAP / Active Directory / User Source
Corporate
Network
SafeNet supports any user store
via a sync agent
SQL, LDAP, AD ,ODBC, Lotus, Novell, anything (via
custom field mapping)
No schema change
Non intrusive/Read only
Multiple domains
No hardware required
Encrypted transmission of data
Users can also be bulk imported via .csv files and / or
created locally
Corporate
Network
LDAP / Active Directory / User Source
LDAP / Active Directory
/ User Source
Corporate
Network
User Directory Sources

Unified Authentication Platform
76
Custom

Widest Choice of Tokens
Authenticators for every user type – and an increasing
focus on commoditisation
Authenticators that:
Don‘t expire
Seed keys can be owned by the subscriber
Can be easily re-assigned to new users
Easy deployment saves cost and time
A token can be included in the service charge
H/W SMS BlackBerry iOS Android Microsoft Java
Multi Platform
USB Grid Microsoft OSx

Token Choice
78
Choose the right token type for each user:
Phone based
Software
Multiple hard tokens
„Tokenless‟ either SMS or Grid based
Our Authenticators:
Don‟t expire
Can be included in the service charge
Seed keys can be generated by the customer
Can be re-assigned to new users
Self enrollment options reduces administration
OTP & PIN complexity defined by the customer
Provides the lowest overall total cost of ownership
Supporting 3rd party tokens enables an orderly and
cost effective migration

Customizable
• Icons
• Colors
• Services
• Multi-language
Request Token
• Approve, Issue, Ship workflow
Self-service API (WSDL)
• Build into existing portals
Self Service

User “Aliases”
User has multiple ―IDs‖
• 1 UserID + up to 2
―Aliases‖
• All can use the same
token(s)
• Allows for different
privileges with only 1
token
Standard
User
Applications
Router &
Server
Management
UserID: Bill
UserID: SysAdmin
Finance
Servers
Enterprise
Resources
UserID: Billy

Security
Hardware HSMs Support
• All token seed records encrypted
and protected by HSM
• All encryption/decryption
executed internally by HSM
• Data center to data center
failover

SAML Single Sign on
Single Sign-on
• Authentication at one
allowed SAML site –
access to all allowed
sites
• Logoff at one allowed
site, logged off at all
allowed sites UserID: Bill
Password: ―OTP‖
SAML Assertion
SAML Assertion
SAML Assertion
bill

SafeNet Authentication Architecture
83
SafeNet
Authentication
Service DataCenter
DataCenter
Administrator Users
Tokens
Internet
SMS
Gateway Email via
SMTP
SMS via
HTTP(S)
(Subscriber or
SP selected)
SMS
message
Group
Subscriber
User Self-Service
LDAP Synch
Migration
Solutions
Authentication
Provisioning
Reporting/Alerts
Agents
User Repository Token Repository
Virtual Server
Management
& Admin
Reports
& Alerts
User
service
requests
Authentication
Request Radius
Authentication
Request
SAML
Authentication
Request
SafeNet
Authentication
Self-Enrolment
Portals
Security Policy
Engines
User
Repository
Agent
Access
Devices
Agents
User
information Migrations
Agent
Existing
RADIUS
Server

Global Trends
84
“as-a-Service” is Accepted by Customers
Source: The 451 Group Cloud Computing Market Monitor, August 2012
Authentication-as-a-Service is HOT!
$13bn by 2015, with 47% in North America
SAS is absolutely the hottest product!
“Gartner predicts that, by 2017, more
than 50% of enterprises will choose
cloud-based services as the delivery
option for new or refreshed user
authentication implementations, up from
less than 10% today.”
Gartner MQ for User Authentication, 2012

Leaders in the Market
85
Gartner ranks
SafeNet @ the top
of the Leader‘s
Quadrant

Facing challenges you can‟t address?
SaaS applications
VPNs
Web-based portals Virtual Environments
More users to protect:
employees, partners,
contractors
More data and
applications to protect
More end points being
used

1] CONTROL: It is complex to set
up, and hard to implement
87

The real world
88

2] AUTOMATION: Difficult and
time-consuming to re-provision
existing users, and enrol new
users
89

3] CHOICE: Only one token
choice per user, and can‘t use
existing authentication tokens
during the migration
90

4] TCO: hidden service &
maintenance costs and high
upfront infrastructure costs
91

Pricing!
It‘s all about total cost of operation
Includes internal costs
Simple per user per year model, MP tokens
included, no extras
Opex or Capex models
Automate everything - massively reduces
administration costs

Summary
Fully Automated
Protect
Everything & Everyone
Authenticate Your Way Migrate Easily
Lower TCO

Спасибо

96
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

Сoffee Break

98
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию
доступной, но защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям
для шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

Data protection for
big data
Rami Shalom, VP, DEC
Product Management,
SafeNet

Data management in the Cloud age
Data management is changing fast:
• Volumes – exponential growth
• Expected Velocity
• Diversity
Traditional systems cannot keep up with the demand
• It‘s simply not designed for that
New approaches are gaining momentum
• Highly flexible
• Scale easily
• Replicable (resilient)
• Cheaper
Big Data!

What is Big Data
“Big data is a collection of data sets so large and
complex that it becomes difficult to process using on-
hand database management tools”
Used for a variety of implementations such as –
• Event collection
• Data crunching
• Unstructured data analysis
• Social networks
• Scientific research – genomic, atmospheric, etc.
• Recently – financial implementations

Big Data – how does it work?!

Big Data – how does it work?!

So what‟s the risk?
App level hacking. No news.
Data isolation –
• What data is stored in each node??
• Where are your nodes??
• who can access your nodes??
Keeping track of your data
• Legit/illegitimate access events
• Data location, expansion and flow

Where is the challenge?!
Where are is the data?
• Where are your nodes?
• What data does each node hold?
• What‘s the lifecycle of each node?
• …
It‘s a new framework
• New flows
• Data capacity
• Ubiquity
Cannot rely on predefined data structures like before

What would it take to
mitigate those risks?
Protect your nodes!
• Make sure no one will access your nodes
• Make sure that wherever they are – they will be safe
• Make sure you can kill a node if needed
Protect your critical data elements
• Credit Card/Identity information
• From legitimate users
• Make sure you comply with regulation

What type of a solution would work?
Encrypt your data for effective isolation
Apply across your data to assure
proper coverage
Make sure you use the right granularity
level
Manage and own your keys!

What‟s available today?
No canned solution to address those risks
No Built in mechanisms nor are they on the roadmap
Different companies offer different pieces which were
repurposed for big data
No vendor offers a complete solution
SafeNet offers the main pieces necessary
Protect Big Data implementations!

What does SafeNet has to offer?
App level data
protection + Secure
access
Node level isolation &
identification
System level data
protection
Overall Key
Management
Storage level data
protection

App level protection ProtectApp
Application level agent
Encrypts data as it enters the system
Persistent protection henceforth
Pros: the ultimate solution! Granular, persistent, extensible
Cons: Code level integration required, intrusive.
Users
Web/Application
Servers
12345 A7DE8
DataSecure
ProtectApp

Node level Protection
ProtectV
Complete protection for each individual
node, using VM level encryption and
isolation
Pre-Boot level protection
Centralized key management
Complete protection of data at rest
FIPS 140-2 L3

Storage
Hypervisor
Hardware Layer
Backup Snapshots
App
OS
App
OS
App
OS
App
OS
App
OS
App
OS
Data copied into OS
partition‘s RAM
Data copied into
storage
Introducing ProtectV
Data Protection for the Cloud.
Data used by
financial app
Data copied in
hourly snapshot
App
OS
After
Enjoy Data Security AND Virtualization/Cloud

Storage Security Solution
11
3

Own and manage your keys KeySecure
Unified key lifecycle management solution
Open standards-based, enterprise key
management
High assurance and robustness • Appliance-based, tamper-proof hardware
• FIPS 140-2 level 3
Optional: virtual key management appliance
KeySecure

Summary
Big data introduces new significant risks
Traditional measures do not apply
• Location
• Capacity
• Flows
No built-in and/or canned solutions
It involves multiple pieces
SafeNet offers a crypto framework to mitigate most of
the risk

116
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и
виртуальным пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в
регионе EMEA (Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

Why a Root of trust of
your physical & virtual
environment is
needed?
Marko Bobinac PreSales Consultant

Agenda
Introduction to HSM‗s
Digital infrastructure on the Front Line
SafeNet HSM‗s
History, Portfolio and Integrations
Root of trust for your physical and virtual environment
How do we get there?
Introducing SafeNet‘s Crypto Hypervisor!
Payment HSM‗s

Introduction to HSM

Think You Don‟t Use Hardware Security Modules?
HSMs secure mobile money payments and verbal banking
transactions made from phones
HSMs secure card data and the delivery of Personal
Identification Numbers (PIN)
HSMs secure entertainment devices, including videogame
consoles and Personal Video Recorders (PVR/DVR)
HSMs secure automated toll booth passes
HSMs secure documents for governments, hospitals, and the court
system
HSMs secure Smart Metering Systems and the delivery of Meter
messages in our homes to Head End Utility systems
HSMs secure Device Manufacturing in the delivery of Trusted Device
Identities we used Every Day
HSMs secure SSL and Web Sites We all use every day

What is an HSM?
Multiple
Application
Servers Application
Key Usage Services
Key
Management
Services
Key Vault Services
Tamper Resistance/Response
Separation of Duties
MFA with M of N Controls
PKCS #11 CAPI / CNG
Java CSP OpenSSL
XML-DIGSIG
Backup/Restore
Export Controls
EKM Interface
Policies FIPS 140-2 Level 3 Common Criteria EAL4+
Offlo
ad
Multiple
Partitions
High Availability
And
Load Balancing
Cryptographic Processing

What do HSM„s do?
An HSM is a collection of algorithms, secure key
storage, accelerators, key management all inside a
tamper resistant unit – it‘s like a box of cryptographic
Lego – how you put the elements together determines
what the HSM does
122
Security Performance Auditability

What is a Hardware Security Module
(HSM)?
A device to keep Business critical crypto keys at the
highest level of security
Accelerate Crypto operations to eliminate bottlenecks
Provides a clear audit trail for all key materials, crypto
operations
We have a wide range of HSM options • Varying performance, storage capacity, and Form Factors,
authentication models
Wide range of SDKs/Toolkits for flexible integration
All with Industry Certifications!

Digital Infrastructures on the Front Line

All IT vendors recommends HSM„s
125

Vs.
Keys in Software Keys in Hardware
Corporate Responsibility

127
Image Credit: [funkwood / Deviant Art]
Will you be here?

SafeNet HSM portfolio

Pre-PKI HSM„s
EFT
Electronic Funds Transfer
• There was no public Internet, SSL traffic and Trusted CA‘s prior to 90‘s
• HSMs were used primarily in Card EFT Payments, the Banking, Government and Enterprise
sectors for protection of sensitive data and secure data exchange
• SafeNet (back then Eracom, founded in 1979) was one of the pioneers in HSM technology:
developed the very 1st PC Encryption Card, and
offered HSMs for EFT/Card Payment Security since the early 80s

Traditional PKI Landscape
Certificate Authorities
Registration Authorities
Web Servers Application
Servers
EFT
Traditional PKI Endpoints

The Evolving „Next Generation‟ PKI Landscape
Smart Grid
Digital Invoicing
Code Signing
e-Passports
… and many more
e-Voting
Online Commerce
e-Signatures
EFT
Next-Generation PKI Endpoints

SafeNet HSM Portfolio
133
Luna SA Luna SP Luna PCI Luna G5
PS Internal Express ProtectServer External Luna EFT Luna KMIP

Security for Server Systems | Custom Firmware
Network Attached and Scalable
High Performance Cryptographic Processor
Hardware security for Java-based applications
HSM Portfolio - Transaction & Identity
Protection
Luna PCI
Luna SA
Luna SP
ProtectServer
Offline Key Archive/Starter HSM Luna G5
Electronic Fund Transfer Luna EFT
Luna G5
Luna PCI
Luna SA
Luna SP
ProtectServer
Luna EFT

200 RSA 1024-bit TPS
600 RSA 1024-bit TPS
7,000 RSA 1024-bit TPS | 1,800 ECDSA TPS
7,000 RSA 1024-bit TPS | 1,800 ECDSA TPS
4,000 RSA 1024-bit TPS
HSM Performance Metrics Offering the Best Breadth of Performance in RSA, ECC and Symmetric
Algorithms
Luna G5
Luna PCI
Luna SA
Luna SP
ProtectServer
Perf
orm
ance
Luna EFT 1600 Visa PIN Verifies

Hardware Security Module Integration
HSMs always integrated with application – on same server or network
attached
Application communicates with keys stored in HSM usually via a client -
but Keys NEVER leave the HSM
HSM Usage:
• PKI – Key storage for CAs – signing of Digital Certificates
• EFT – Retail and Banking (PIN processing for Credit/Debit Cards at ATMs
or Point of Sale, Smart Card issuance). PCI DSS requirements
• Customised Applications – document signing, time stamping, ePassport
projects, DNSSEC, AMI

HSM Integrations (a partial general-purpose list)
ActivIdentity 4TRESS
Authentication Server
ActivIdentity ActivID CMS
Microsoft CA Luna SA PKI-
Bundle
Adobe LiveCycle Digital
Signatures ES2
Adobe Lifecycle Document
Security with Luna SA
Apache HTTP Server
BIND/OpenDNSSEC DNSSEC
EJBCA (Primekey)
Emue Technologies Fortress
Entrust Security Manager
IAIK PKCS #11 Provider
IBM Tivoli Access Manager
IBM Websphere MQ
Microsoft ADRMS (& RMS)
Microsoft Authenticode
Microsoft Certificate Enrolment
Microsoft Certificate Services
Microsoft FIM (ILM & CLM)
Microsoft IIS
Microsoft OCSP
Microsoft SharePoint
Microsoft SQL Server
OpenCA
Open SSL
Oracle 11g
Protegrity DPS
Red Hat Certificate Authority
RSA Keon
SafeNet ProtectDrive
SafeNet SMCII
SafeNet Authentication Service
SafeNet Authentication
Manager
SafeNet DataSecure i460
SafeNet KeySecure k460
Sun Java PKCS#11 Provider
Tumbleweed OCSP
Vasco VACMAN Controller
Venafi Encryption Director
Vordel XML Gateway
137

Payment SW Vendors – HSM Integration
Payment Software Vendor Product Name Business Region Served
ACI Base24-eps + TSS Global
ACI / EPS ASx EE
ACI / S1 Postilion Global
ACI / S2 Systems ON/2, OpeN/2 MEA
Arius Asoft EMEA
Banksoft BPS (Banksoft Pre-Personalisation System) EMEA
BPC (Banking Production Centre) SmartVista Global
Compass Plus Tranzware Online, Card Factory EMEA, APAC
CR2 BankWorld EMEA
CSFI u/SWITCHWARE Global
CubeIQ AlphaPIN EMEA
Distra e-switch APAC, EMEA
FIS / EFunds / Oasis Technology Connex, IST/Switch Global
HPS PowerCARD EMEA
Interblocks iSuite iSwitch APAC, MEA
Interpro Switch Americas
i-Sprint USO, AccessMatrix UAS MEA
IWI Net+1 APAC
OpenWay Way4 EMV Issuance EMEA, APAC
Opus / ECS Electra EFT Switch APAC, EMEA
RS2 BankWorks EMEA
S2M SELECT EMEA
Silverlake SIBS APAC
Sparkassen IT Solution Payment Switch EMEA
Sungard CardPro Americas, APAC
Tallyho Online Switch Module Americas, APAC
TAS CARD EMEA
TECS TECS Payment System EMEA
TietoEnator TransMaster EMEA
TPS Iris (Phoenix), Access, Sentinel EMEA
TSYS CTL ONLINE, PRIME, NCRYPT Global
Collis EMV Host Toolkit, PVT Global
Barnes International CPT 3000 EMV PVT EMEA

SafeNet HSM Integrations samples
SafeNet solutions
using HSM
SafeNet Authentication
Manager - SAM
SafeNet Authentication Service - SAS
KeySecure k460
DataSecure i460
SafeNet Management
Console II (for
HighSpeed encryptors)
SafeNet KMIP
(manage keys on HSM)

Root of trust for your physical and virtual
environment
140

… But HW doesn‟t work in a Virtual World? Today‟s Hardware-based encryption solutions are designed for the physical
world!
Islands of
encryption
141
Time-consuming crypto rollouts
Very slow to scale up and down
Limits of encryption today:
Inability to protect & control data centrally
Can’t take full benefits of cloud
DNSSEC SSL Email Code Sign Database

What is needed?
Encryption Infrastructure that follows the
cloud model!
14
2
Benefits:
• Reduce Costs (Reduce DC
presence)
• Centralize SME Crypto Group
• Unify Governance and
Compliance
• Centralize services
Islands of encryption
DNSSEC SSL Email Code Sign Database
Centralized Encryption model

On Demand Cryptographic Resources for
Your Virtual Data Center and the Cloud
143

Where do we start?... With a hypervisor for encryption…
Introducing the SafeNet Crypto Hypervisor!
Crypto Hypervisor c. 2013
• HSM Partition
• HSM Isolation
• Dynamic crypto allocation
VMware hypervisor c. 2001
• O/S Partition
• O/S Isolation
• Dynamic resource allocation
Application
Hypervisor
Operating System
Hardware
Platform
asD
AS
D48
RH
AsD
54
6F
4d
fgf
dd
fgd
fgh
jkD
6G
54
R
Dynamic Crypto Resource
Crypto Hypervisor
Crypto Hardware
Platform (HSM)
Application

Crypto Hypervisor:
Designed for operational cloud model
On-demand
crypto delivery
1
Self-service
portal for users
2
New crypto services
spin up easily
3
Encryption now a
cloud enabler
4
Part of ―New
VM Rollout
Process‖
5
Apps can now
migrate to cloud
6

Three things to know about
Crypto Hypervisor
146
Built for the cloud
• Shared resource pooling, rapid elasticity and multi-tenancy
• Can reduce capital costs up to 95%
Lower TCO
• Take advantage of virtualization
• Deliver high-assurance cryptographic resources in a fraction of the time
• 5 minutes, not 5 hours
Centralized control
• Strong auditing capabilities
• Compliance in the Cloud
• Ensure enterprise-wide consistency of crypto policy

Crypto Hypervisor Extends the Capability of
HSMs to Fit the Cloud Model
147
NIST1 Cloud Definition of
Essential Characteristics
Legacy
HSMs
On-Demand Self-Service No
Rapid Elasticity No
Measured Service Some
Broad Network Access
Yes
Resource Pooling Some
Multi-Tenancy2 No
1. National Institute of Standards and Technology
2. Multi-Tenancy is an essential characteristic added by the Cloud Security Alliance
NIST1 Cloud Definition of
Essential Characteristics
Crypto
Hypervisor
On-Demand Self-Service Yes
Rapid Elasticity Yes
Measured Service Yes
Broad Network Access
Yes
Resource Pooling Yes
Multi-Tenancy2 Yes

What‟s in the Crypto Hypervisor
Crypto Command Center Bundle
Crypto Command Center
SafeNet PED II
SafeNet Luna G5
SafeNet Luna SA 5.2
HSM Includes:
• Crypto Command Center Software
• SafeNet Luna G5
• Local PED II
• PED II Keys

What is Crypto Command Center?
System (SW) to automate the provisioning of HSM resources
Abstracts the management of HSMs from the end user
Administrators
• Manage the crypto for your company
• Manage the physical HSM devices
• Determine what crypto services are offered
• Create a catalog of services for end users
• Manage who has access to those services
Consumers/Users
• Manage crypto applications that consume crypto services
• Own their HSM resource when ‗leased‘
• Request and release use of HSM resources from catalogues
• Always in control of their keys!
149

VM is Stolen…VMs with “HTL” Host Trust
Link
HSM Client VM
NTLS
Luna SA
Today:
• Stolen VM will not be granted access to
SA partition
• Stolen image does not have OTT,
required to establish HTL Link
X Access Denied
• Prevents theft of an at-rest VM image
• Connection to the SA is authorized by a one-time token
HSM Client VM
© SafeNet Confidential and Proprietary

Benefits for Private or Public Cloud…
Reduced Risk • FIPS/CC validated HSM for applications
• Centralized compliance and governance
Increased Efficiency • Fast secure application deployment
Reduced Cost • Centralized crypto experts
• Shared HSM crypto resources
Increased Revenue • New HSM ‗AAS‘ Offering

Production example: AWS CloudHSM
• Secure Key Storage and Cryptographic Operations
http://aws.amazon.com/cloudhsm/

Payment HSM„s and
Use Cases
Hermann Bauer Director HSM Business
Development, EMEA

Agenda
Criticality of Payment and Banking Systems
HSM Payment Solutions and Use Cases • Card Transaction Processing (Acquiring, Switching, Authorisation)
• Card Issuance (Data Preparation, Card Personalisation) of EMV and mag-stripe cards,
plus PIN Issuance
• OTP with EMV Card (Chip Authentication)
• 3D Secure Internet Payments using Payment Card
• Contactless Payment Cards
• NFC Mobile Payments
• OBM (Online Banking Module) for End-to-End Encryption of Online Credentials
• Remote ATM Key Loading
• PCI/P2PE Compliance & Fraud Reduction
• ViewPIN – Secure online delivery/distribution of card PINs to cardholder
• Wholesale Payments / Interbank Funds Transfer
• Check Clearing
154

Insert Your Name
Insert Your Title
Insert Date
Why are Payment & Banking Systems,
as well as their protection, so critical?

Payment Systems
Financial Institutions, PSPs and Electronic Payment Systems • Integal Part of the Global Economy = Infrastructure, Live Blood
Wholesale and Retail Payments very much intertwined • Most Wholesale Payments are the result and the collection of many
small Retail Payments
Regulation and Standardization of Payments market Use of HSMs mandated by card schemes (Visa, MasterCard) and
domestic payment organizations
• EMV, PCI, SEPA, PSD, ...
Financial Institutions & Payment Service Providers very security conscious because MONEY is #1 target of criminals & fraudsters
HSMs critical in protecting MONEY
156

Data Breaches – Victims & Motives of
Attackers
157
Source: 2013 Verizon DBIR
… Well, what a surprise … MONEY
Motives of Hackers
$$$

Steady Growth in Payment Cards, Payment
Transactions & e- and m-Payments
Non-cash payments growth worldwide 7,1% in 2010 (283 bn, 306 bn expected in 2011) • Strong growth rate in developing countries (16,9%)
• Increase of more than 30% in Russia and China
Cards (debit cards and credit cards) biggest driver of non-cash payments volumes globally • Cards accounted for 55.8% of all non-cash payments in 2010
• In 2010, more than one in three non-cash payments were made using a debit card
Rapid growth of e-payments and m-payments • e-commerce activities (e-payments) is forecast to reach 31.4 billion in 2013, 20% sustained growth a year in 2009-13
• payments using mobile device (m-payments) expected to grow even faster, by 52.7% a year to reach 17 billion in 2013.
158
Source: World Payments Report 2012

Insert Your Name
Insert Your Title
Insert Date
Card Transaction Processing
Acquiring, Switching, Authorisation

Card Payment Transaction Security primarily based on symmetric cryptography (DES3)
Security Requirements
• User authentication
• Secure PIN processing (―end-to-end‖ protection requirement)
• Card authentication
• Transaction authentication
• Data confidentiality
• Cryptographic key management…
…involves the use of a certified HSM, mandated by
- international card schemes
- national payment schemes
Card Payment Security Concepts &
Services
160

T IA A S1
Acquirer Switch 1 Issuer A Terminal
Card Transaction Processing - Role of the
HSM
S2
Switch 2
IB
Issuer B
1 2
2 3
PIN operations
1. PIN Encryption
2. PIN Translation
3. PIN Decryption & Verification
Message Authentication operations
1. MAC Generation
2. MAC Translation (Generation/Verification)
3. MAC Verification
Each connected pair of entities share a
Common key to form a key zone
161

Insert Your Name
Insert Your Title
Insert Date
Card & PIN Issuance
Card Management, Data Preparation, Card Personalisation

Card Issuance Card Management, Data Preparation, Card
Personalization Applications
• Production & personalization of smart cards & secure documents
• Card types & environments:
• Payment Cards (EMV & mag-stripe credit/debit cards), Fuel/Fleet Cards
• eID / e-Passport Documents
• eHealth Cards
• Telco/SIM Cards
• Loyalty/Gift Cards
• Corporate ID Cards
• Online Banking & Authentication Cards & Tokens
• Personalization data includes private user information (PAN, PIN), keys and certificates
HSM Usage • Data Preparation: Server side key, PIN, certificate generation for injection into smart card
• Personalization: Encrypted communications (Secure Messaging) with smart card for chip encoding
• High speed/throughput key generation/derivation - may do thousands of cards per hour
• High availability – cannot tolerate stoppage of automated card processing equipment
• Adherence to relevant standards : EMV, ANSI, ZKA, APCA, GlobalPlatform, ICAO, …
• Certifications: FIPS 140-2 Level 3, PCI-HSM
Application Providers • ACI/BellID, AustriaCard, BPC, CardHall/Pronit, CardTek, Compass Plus, Cryptomathic, DataCard,
G&D, Gemalto, Morpho, Mühlbauer, NBS/UbiQ, Oberthur, OpenWay, TSYS CardTech, …
163

Card Issuance – Central Back Office
Bank
HSM Government
Issuer Card Application
Management System
Data Preparation System
Card Manufacturer
OS +
Card
Application
HSM
HSM
Card Production System
Personalisation System
Personalizer / Personalization Bureau
KEK
KEK
KMC
KMC
Chip Manufacturer
OS +
App
encrypted
file(s)
164

Instant Issuance at Branch
165
HSM

PIN Mailing / Key Mailing
166
HSM Features HSM directly attached to printer
PINs never exposed in clear form
(outside of protected HSM
evnvironment)
HSM generates and prints PINs to
PIN Mailers
Support of PIN Mailer layouts in
Postscript format 10)
PIN Printing in Words
USB & Serial Printing
Separate PIN Mailer User Rolers
Extensive Auditing

Insert Your Name
Insert Your Title
Insert Date
OTP with EMV Card
Chip Authentication Program (CAP)

Chip Authentication Program (EMV-CAP)
Payment Card as General-Purpose Secure Authentication Device
Card + Offline Reader
Products: Mastercard CAP & Visa DPA • Two Factor Authentication (2FA)
• Payment Card (Credit or Debit) & PIN
Authentication Process • Payment card inserted into stand-alone reader
• Cardholder authenticates to the chip with PIN entered on the reader (not interceptable)
• Card produces One-time Password (OTP), not susceptible to ―phishing‖ attacks
• Any chip card loaded with standard Mastercard M/Chip or Visa VSDC payment application or stand-alone CAP/DPA card
Advanced feature: Transaction Signing
168

Insert Your Name
Insert Your Title
Insert Date
3D
Verified by Visa
MasterCard SecureCode
3D-Secure Internet Payments

3D-Secure Credit-Card Transactions over the Internet
• A Visa Initiative, but licensed to others:
• Verified by Visa
• MasterCard SecureCode
• JCB J/Secure
• For merchants and financial institutions,
specifies authentication and processing procedures
• Requires some form of card-holder authentication, at
this stage generally keying of a password/PIN
170

3D-Secure - Online Card Payment
Technology Purpose
• Increase e-commerce transactions
• Promote consumer confidence
• Increase member and merchant profitability
Features • Provide global framework for authentication of remote payments
• Reduce operational expense by minimizing chargebacks for unauthorised use
• Can be implemented without special cardholder SW or HW
• Extensible as to authentication methods (e.g. payment smartcards, certificates)
• Enhanceable by Issuer without impacting acquirer or merchant
• Extensible into emerging channels like mobile phones, PDA, digital TV
• Based on globally accepted technical standards
• Provides a centralized archive of payment authentications for use in dispute resolution
3D-Secure Components
• MPI – Merchant Server Plug-In • processes payment messages
• ACS – Access Control Server • Issuing application requiring FIPS 140-2 Level 3 HSM. • CAVV – Authentication code for card generated by HSM • Authenticates card holder, merchant and transactions
171

Insert Your Name
Insert Your Title
Insert Date
Contactless Payments
MasterCard PayPass
Visa PayWave

Contactless Cards
Simpler way to pay, higher convenience, speed
―Tap & Go‖ experience (public transport, parking garages, toll roads, fuel dispensers)
Minimum impact on existing payment infrastructure
2 offerings: • Contactless / (EMV) Chip
• Usually dual interface card (contact and contactless
• Uses standard EMV authentication technologies (SDA/CDA)
• Low-value payments, approved offline by both card and terminal
(for fast transactions)
• Contactless / Mag-Stripe • meaning: for magnetic-stripe payment infrastructures
• potentially other form factors (key fob, watch)
• Online Payments
• New authentication mechanism: Static or Dynamic CVV
(CVC3 / dCVV)
173

Insert Your Name
Insert Your Title
Insert Date
Mobile Payments
NFC Mobile Payments

NFC Mobile Payments
―Payment Card― ( ) on mobile phone
• NFC used for communications (up to 10 cm distance)
• Payment app resides in SE (Secure Element) on mobile
• UICC, MicroSD, Integrated Chip
Equivalent to contactless/mag-stripe card
No modification to existing (contactless) acceptance infrastructure
No mobile network activity during transaction (payment app on mobile <-> reader/terminal)
New: OTA (over-the-air) personalisation/provisioning
• Issuer Installation (full OTA personalisation)
• Service Provider Installation (pre-installation)
• MasterCard and Visa offer such services
175

Insert Your Name
Insert Your Title
Insert Date
OBM (Online Banking Module)
End-to-End Encryption of Credentials for Internet/Online Banking

Internet Banking E2E Application
Typical internet security from the browser to web server is SSL, terminated at the web server
End-to-end encryption, browser to host, provides totally secure online transactions - end-to-end PIN / password protection
RSA encryption at client with Java applet – HSM decryption and verification at host
Supports numeric (card) PINs and (alphanumeric) passwords (4-30 characters)
PIN/password change option
Application
Server/Host Web Server
Internet
177

Insert Your Name
Insert Your Title
Insert Date
ATM Remote Key Loading

ATM Remote Key Loading
179
RKL means the secure on-line transport to the
ATM of its initial DES/3DES key (A-key, TMK)
using public key techniques, along with associated
key and certificate management.
RKL eliminates the arduous nature of manual key
loading and the associated compliance tracking
Result - dramatically reduced cost and increased
security
PCI-DSS compliant (change keys once per year)
2 Methods:
Certificate-based (Diebold)
Signature-based (NCR, Wincor-Nixdorf)

Insert Your Name
Insert Your Title
Insert Date
PCI-P2PE Compliance & Fraud Reduction
eCommerce & Payment Service Providers

PCI-DSS & PCI-P2PE Compliance
Key Requirements:
• Protect cardholder information (when stored and
transmitted)
Technologies:
• Network segmentation
• Tokenization
• Encryption reduce PCI scope
• Point-to-point encryption (P2PE)
181

What is Point-to-Point Encryption?
Point-to-Point Encryption (P2PE) is encryption of sensitive
data at the Point-of-Interaction (POI) for secure
transmission to a secure boundary where it may be
decrypted, re-encrypted or tokenized.
182
FIPS 140-2 L3 or PCI-HSM certified HSM is required by P2PE decryption provider

Insert Your Name
Insert Your Title
Insert Date
Payment Solutions using other
SafeNet HSMs and Appliances
(Luna SA/PCI, Luna SP, DataSecure)
ViewPIN
Electronic Check Processing
Wholesale Payments / Interbank Funds Transfer
PCI-DSS Compliance – Encryption and Tokenization

Insert Your Name
Insert Your Title
Insert Date
ViewPIN
Secure Online PIN/Credential Delivery

Secure Online PIN/Credential Delivery
ViewPIN - Luna HSM helps provide the only
secure/easy-to-use online EMV PIN delivery solution
Solution allows card issuers to provide a secure
electronic alternative to traditional PIN mailers
Benefits • Instant PIN issuance allowing immediate use of card
• Cost savings associated with not having to issue paper PIN mailers
• Eliminates PIN mailer interception fraud via post
• Provides a competitive advantage
185

Insert Your Name
Insert Your Title
Insert Date
Compliance & Fraud Reduction

DataSecure Powerful Centralized HW-Based Encryption Management
187
• Compliance & Fraud Prevention • Solution built from the ground up to meet compliance requirements (e.g. PCI-DSS)
• Two Methods
Encryption • At DB level (transparently) or Application layer
Tokenization • Tokenization replaces sensitive data (credit cards, social security numbers etc.)
with a surrogate value, a token
• As a result most system components are exposed only to the surrogate value and NOT to the original sensitive data
• Protects sensitive data and eliminates the risk of data-blooming
• Sensitive data does not exist in the system and processing is done only with the token
• Reduces significantly regulatory scope
• Works best on structured data

Insert Your Name
Insert Your Title
Insert Date
Wholesale Payments /
Interbank Funds Transfer

Wholesale Payments (Funds & Securities)
189
Applications
Applications
Directory
Certificate
Authority
Key Management
SSL Acceleration
FIPS certified
SafeNet HSM
SafeNet HSM
Small
Banks
Access Control
via 2 or 3 factor
Financial Transaction
Infrastructure
Payments & Cash Mgt
Treasury & Derivatives
Trade services
Pre-Settlement/trade
Clearing services
Custody services
SafeNet HSM
Large
Banks

Insert Your Name
Insert Your Title
Insert Date
Check Clearing

Check Clearing Process Embedded Example
Check MIRC data & images are captured at the Presenting
Bank
Clearing House Interface (Paying Bank)
Signed & Encrypted
Outward Electronic Check MICR
& image
Clearing House
Luna PCI
Root Key Storage, Signing,
Encryption
Luna PCI
Root Key Storage, Signing,
Encryption Luna PCI
Root Key Storage, Signing,
Encryption
Signed & Encrypted
Outward Electronic Check MICR
& image
Outward return Check MICR Inward Check MICR &
images
Electronic Check
Archive
Clearing House Interface (Presenting Bank)
Luna SA
User Auth
Auth &
license
control
Auth &
license
control
Database encryption OCSP & Enc data
Sign & Enc data
191

Спасибо

Wrap up - Closing of
the plenary session +
Q&A

Выводы (Takeaways)
SafeNet 2013 – Представление Новой Компании Safenet в России
У нас есть ответ новым технологическим вызовам современности:
• Виртуализация
• Мобильность
• Облачные вычисления
• Большие Данные
Продолжение инвестирования в Коренной бизнес:
• eToken/iKey, Сертификация ФСТЭК
• HSMs/HSEs, Новые возможности
• DataSecure, Виртуальное устройство
SafeNet в России – серьезные планы по инвестициям:
• Персонал
• Локализация/Сертификация решений
• Доступность обучения
194

195
9:00 – 9:50 Регистрация участников. Приветственный кофе
9:50 – 10:00 Открытие конференции
Сергей Кузнецов - Глава Представительства SafeNet в России и странах СНГ
10:00 – 10:15 SafeNet - лидер на рынке информационной безопасности. Представление компании
Гари Кларк (Gary Clark) - Генеральный Директор SafeNet в регионе EMEA (Европа,
Ближний Восток и Африка)
10:15 – 10:55 Экспансия данных. Как защитить виртуальный датацентр и облако?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
10:55 – 11:35 Аутентификация как сервис (AAAS) или почему Ваша компания будет в числе первых,
перешедших на облачную аутентификацию?
Джэйсон Харт (Jason Hart) – Вице-Президент по облачным решениям
11:35 – 12:05 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
12:05 – 12:45 Большие Данные (Big Data) наступают. Как сделать информацию доступной, но
защищенной?
Рами Шалом (Rami Shalom) - Вице-Президент по продуктам и решениям для
шифрования данных и управления данными
12:45 – 13:25 Корень доверия (Root of Trust) - нужен ли он вашим физическим и виртуальным
пространствам?
Герман Бауэр (Hermann Bauer) – Директор по развитию бизнеса в регионе EMEA
(Европа, Ближний Восток и Африка)
Марко Бобинак - Консультант по продуктам компании
13:25 – 13:30 Закрытие Пленарной Сессии. Вопросы и ответы
13:30 – 14:30 Обед
Программа мероприятия

13:30 – 14:30 Обед
Тематические
сессии, часть
1
Сессия 1: SafeNet
Authentication Service
Сессия 2:
Storage Secure
Сессия 3: Hardware
Security Modules
14:30 – 15:15 Ведущие:
Джэйсон Харт, SafeNet,
Михаил Рожнов,
CertSys
Ведущие:
Рами Шалом, SafeNet,
Андрей Лаптев,
SafeNet
Ведущие:
Герман Бауэр, SafeNet,
Владимир Дегтярев, Demos
15:15 – 15:25 Вопросы и ответы Вопросы и ответы Вопросы и ответы
15:25 – 15:50 Кофе-брейк. Работа экспертной зоны, демо-стендов партнеров
Тематические
сессии, часть
2
ProtectV
Data Secure:
Tokenisation
Solution Demo
Hardware Security Module
EFT
HSE/Senetas
15:50 – 16:35 Ведущие:
Рами Шалом, SafeNet,
Михаил Рожнов,
CertSys
Ведущие:
Марко Бобинак,
SafeNet,
Андрей Лаптев,
SafeNet
Ведущие:
Владимир Дегтярев, Demos
16:35 – 17:00 Вопросы и ответы Вопросы и ответы Вопросы и ответы
17:00 – 18:00 Закрытие мероприятия. Коктейли
196
Программа мероприятия