main(int ac, char** av){ int i; for(i=1; i
description
Transcript of main(int ac, char** av){ int i; for(i=1; i

1
main(int ac, char** av){ int i; for(i=1; i<ac; i++)
printf(av[i]);}

2
main(int ac, char** av){ int i; for(i=1; i<ac; i++)
printf(strlen(av[i]));}

3
#define MAX 100main(){ int i; char t[200]; for(i=1; i<=MAX; i++){
scanf(“%s\n”, t);printf(t);
}}

4
#include <stdio.h>#include <string.h>#include <stdlib.h>
main(int ac, char** av){ char key[]="HelloWorld"; int i; char ct[200];
for(i=0;i<strlen(av[1]);i++) ct[i] = av[1][i] ^ key[i%strlen(key)];
printf(ct);}

5
ALICE BOB
Eve

6
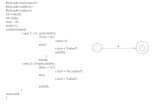
EvePDA
ALICE
PDA
Challenge: n
Id, {Id+n}Kid OK
Challenge response(the lab door protocol)

7
What can go wrong?
• One sided authentication– But isn’t the visual authentication of the door enough!?
• n is not really random• n is not really unrepeatable• PDA compromise / copy• PDA loss• Key compromise or theft• Brute force attacks• Algorithm weaknesses

8
IFF (Identify-Friend-or-Foe) Systems

9
MIG in the middle(not true but interesting)http://www.cl.cam.ac.uk/~rja14/errata.html
MIG In The Middle Attacksouth african air defense = SAADsouth african bomber = SABAngolan air defense = AADAngolan MIG = MIG
SAAD --> MIG: NMIG --> AAD: NAAD --> SAB: NSAB --> AAD: KT{SAB, N}AAD --> MIG: KT{SAB, N}MIG --> SAAD: KT{SAB, N}

10
Good protocol wrong problem!
• Aircraft verification vs. detection

11
Microsoft has proposed the so-called passport protocol for authenticating users on the web. The protocol works as follows:
(a)Initially users connect to the passport web site and create profiles for themselves (each profile includes a user name and password);
(b)When the user wants to login to a secure site (e.g., secure.com) he/she direct their browser to site;
(c)The secure site then redirects the user to the passport web site;(d)The user then enters his/her username and password;(e)If logging in is successful the passport site sets a special
cookie in the user’s browser and redirects him/her back to the original site (secure.com, in this case);
(f) The cookies contain information about the user’s identity and are encrypted and signed so that they cannot be forged;
(g)Secure.com collects the cookie from the user and decrypts it to verify the user’s identity and the authenticity of the cookie; and
(h)If all is well the user is allowed access to the site.

12http://avirubin.com/passport.html

13http://avirubin.com/passport.html







![· Web viewint library::menu(int color,int r,int c,int npara,char *popup[])](https://static.fdocuments.us/doc/165x107/5aa760287f8b9aee748bfebc/-viewint-librarymenuint-colorint-rint-cint-nparachar-popup.jpg)


![Welcome to The Air Force School · char Profile [30 J public : Director ( ) void Input ( ) void output ( ) class Company: private Chairperson , int CID; char City [20] i public :](https://static.fdocuments.us/doc/165x107/5fc1805c045d79754671aaad/welcome-to-the-air-force-school-char-profile-30-j-public-director-void-input.jpg)



![ME964 High Performance Computing for Engineering … · int main() {char c[10]; int d[10]; int* darr; darr = ... (p,](https://static.fdocuments.us/doc/165x107/5b686a627f8b9acc608ce910/me964-high-performance-computing-for-engineering-int-main-char-c10-int.jpg)
![int main() { return 0;cs4400/c+representation.pdf#include #include int main(int argc, char** argv) {int a, b; a = atoi(argv[1]); b = atoi(argv[2]);](https://static.fdocuments.us/doc/165x107/5e41acf1ff471a55ba198623/int-main-return-0-cs4400c-include-include-int-mainint-argc-char-argv.jpg)

![Expressionsfac.ksu.edu.sa/sites/default/files/csc215_-_02_vars_data_types_and...Variables initialized via assignment operator: ... char 8 -128 .. 127 unsigned char 8 0 .. 259 int [signed]](https://static.fdocuments.us/doc/165x107/5b0a58be7f8b9a0c4b8be459/initialized-via-assignment-operator-char-8-128-127-unsigned-char-8-0-.jpg)
![Intro, C refresher...Primitive Types in C Integer types char, int Floating point float, double Modifiers short[int] long[int, double] signed[char, int] unsigned[char, int] 22 C Data](https://static.fdocuments.us/doc/165x107/5f3aba8516ff843a9117349e/intro-c-refresher-primitive-types-in-c-integer-types-char-int-floating-point.jpg)