Cisco security everywhere jamie sanbower 2-25-16
-
Upload
cisco-public-sector -
Category
Technology
-
view
1.278 -
download
0
Transcript of Cisco security everywhere jamie sanbower 2-25-16
The latest and greatest
Jamie Sanbower, CCIEx3 #13637Security Technical Solutions Architect
Security Everywhere
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialSecurity Architecture OverviewNGFW / NGIPSAdvanced Threat DefensePolicy & AccessMeraki SecuritySummary
Agenda
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialSecurity Architecture Overview
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
3
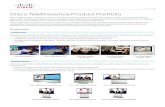
Comprehensive Best-of-Breed Security Portfolio
WWW
Threat Intelligence and Analytics
Open|Cloud|Integrated|ContinuousNGFW/NGIPSAdvancedThreatPolicy and AccessWebEmailUTMBuilding Blocks Working Together as an Architecture
Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialBaseball team analogy (moses)
43/1/16Cisco Live 2013
10I000 0II0 00 0III000 II1010011 101 1100001 110
Working Together to Create a Security ArchitectureCisco FTD ASA w/ FPCisco Web & Email SecurityCisco NGIPSCommon Identity, Policy and Context SharingMalware Prevention / Sandboxing10I000 0II0 00 0III000 II1010011 101 1100001 110110000III000III0 I00I II0I III0011 0110011 101000 0110 00101000 0II0 00 0III000 III0I00II II II0000I II0100I II0I III00II 0II00II I0I000 0II0 00
Context-aware SegmentationNetwork IntegrationContextVisibilityCisco AMP ClientAMPOpenDNSTrustsecISEPxgridNaaSNaaE
Cisco
Pervasive & IntegratedAcross the Portfolio
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
5
Better Together Lots of Products, Working Together
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
6
Example Capabilities Architected into Network Fabric
Network as an EnforcerNetwork as a SensorAccelerate Containment
Reduce Lateral Movement, Enforce Dynamic Granular Access Control, Compliance Adherence
Detect Anomalous Traffic Flows, Rogue Devices/Aps, User Access Policy Violations
Automate Quarantine, Traffic Redirection, Real-Time Application of ACLs
7
Hosted Identity Services ThreatGRID applianceAdvanced Threat AnalyticsRadWARE, and ZIX partnershipsCisco ASA with FirePOWER ServicesNetwork as a Sensor and Enforcer ACI Integration with ASA and FirePOWERNeohapsis and OpenDNS AcquisitionsAMP EverywhereAcquisition of Lancope and PorticullisFirePOWER Services on ISRNew Platforms(ASA 5506, 5508, 5516, 5506-H, & FirePOWER 9300)AMP in AnyConnectMassive Innovation and Investment
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialNGFW / NGIPS
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
9
NGIPS / NGFW Capabilities
Firepower NGIPSFirepower + AMPASA+Firepower+AMP
Application VisibilityControl (AVC)
IdentityAuthorization
Intrusion Prevention
MonitoringAnalytics
Threat Intelligence
Web ReputationFiltering
Anti-MalwareFile Reputation
MalwareSandbox
Firewall
Access ControlUsing TrustSec
Routing
VPN Concentrator
ClusteringCommon NGIPS and AMP code baseCommon Threat Management Firepower MCCommon Security Intelligence - TalosNGFW
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
10
NSS Labs Next-Generation Firewall Security Value Map
Source: NSS Labs 2014
The NGFW Security Value Map shows the placement of Cisco ASA with FirePOWER Services and the FirePOWER 8350 as compared to other vendors. All three products achieved 99.2 percent in security effectiveness and now all can be confident that they will receive the best protections possible regardless of deployment.
NSS Labs Next-Generation IPS Security Value MapSource: NSS Labs 2015
The Firepower 8350 blocked 99.5% of exploits. The device proved effective against all evasion techniques tested. The device also passed all stability and reliability tests. The Cisco Firepower 8350s rated by NSS at 18,544 Mbps, which is higher than the vendor-claimed performance; Cisco rates this device at 15 Gbps.
Some thoughts on how to interpret the latest NSS numbers
Security Effectiveness Scores:
1800 attacksCisco: 99.5% (missed 8)PAN: 98.8% (missed 21)TippingPoint: 86.6% (missed 241)Fortinet: 99.2% (missed 14)
Now, the report says the ran over 1800 attacks. If we just use 1800 as the number, then that means Cisco missed 8 attacks. PAN missed 21. Fortinet missed 14+. TippingPoint missed 241.
Cant we say, then, that a customer running PAN was 2-1/2 times more likely to be compromised than Cisco? The number is actually 2.6 times more likely. We could also call it 260% more likely.
Using the same logic, Fortinet customer would be 1.8 times more likely. (or 180% more likely)
TippingPoint completely sucks, using this logic. More than 30 times more likely, or 300% more likely to be compromised.
We all know PAN is a pain. Theyre not a pain because theyre a better firewall or IPS. Theyre a pain because they are VERY GOOD at focusing their attention on the few things they do better. In the past, this was application visibility and application-based firewall rules. Several years ago, it was identity-based rules.
Most recently, for me, its back to identity. Only now, theyre not looking at AD. Theyre focusing the customers on the need to support authentication through other means, like listening to Radius accounting packets (which can easily be spoofed, by the way) and Outlook Web Access authentication. Its also on SafeSearch lately. They convince the customers that these requirements are a MUST, and use it to eliminate Cisco.
We need to focus the customers, instead, on PROTECTING THEIR NETWORKS. No one does this as well as Cisco.
Gary12
Cisco Firepower Management Center (Firesight)
Theres actually a video embedded here. Play it during the presentation!13
Most Accurate NGIPS
Understand the Context of the traffic:
Who, What, Where, Which Applications
Theres actually a video embedded here. Play it during the presentation!14
Most Accurate NGIPS
IPS Rules automatically tuned for YOUR environment!
Theres actually a video embedded here. Play it during the presentation!15
Most Accurate NGIPS
Theres actually a video embedded here. Play it during the presentation!16
Most Powerful NGFW
Theres actually a video embedded here. Play it during the presentation!17
Most Powerful NGFW
Theres actually a video embedded here. Play it during the presentation!18
Most Powerful NGFW
Theres actually a video embedded here. Play it during the presentation!19
Most Powerful NGFW
Theres actually a video embedded here. Play it during the presentation!20
Advanced Threat Defense
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
21
NSS Labs Breach Detection Systems Security Value Map
Source: NSS Labs 2015
Cisco AMP offers superior security effectiveness, excellent performance, and provides security across more attack vectors than any other vendor.
99.2% Security Effectiveness rating in BDS testing, the highest of all vendors tested.
Excellent performance with minimal impact on network, endpoint, or application latency.
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialIntroduction to NetFlow23
10.2.2.2port 1024
10.1.1.1port 80
eth0/1eth0/2
Start TimeInterfaceSrc IPSrc PortDest IPDest PortProtoPkts SentBytes SentTCP Flags10:20:12.221eth0/110.2.2.2102410.1.1.180TCP51025SYN,ACK,PSH10:20:12.871eth0/210.1.1.18010.2.2.21024TCP1728712SYN,ACK,FIN
Start TimeInterfaceSrc IPSrc PortDest IPDest PortProtoPkts SentBytes SentTCP Flags10:20:12.221eth0/110.2.2.2102410.1.1.180TCP51025SYN,ACK,PSH
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialNetFlow = Visibility24
Router# show flow monitor CYBER-MONITOR cache IPV4 SOURCE ADDRESS: 192.168.100.100IPV4 DESTINATION ADDRESS: 192.168.20.6TRNS SOURCE PORT: 47321TRNS DESTINATION PORT: 443INTERFACE INPUT: Gi0/0/0IP TOS: 0x00IP PROTOCOL: 6ipv4 next hop address: 192.168.20.6tcp flags: 0x1Ainterface output: Gi0/1.20counter bytes: 1482counter packets: 23timestamp first: 12:33:53.358timestamp last: 12:33:53.370ip dscp: 0x00ip ttl min: 127ip ttl max: 127application name: nbar secure-http
A single NetFlow Record provides a wealth of information
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialTurn Network into a Security Sensor Grid
Internet
Atlanta
San Jose
New York
ASR-1000Cat6kUCS withNexus 1000vASACat6k3925 ISR3560-X3750-XStack(s)
Cat4kDatacenterWANDMZAccess
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
NetFlow
Know The Top Security Events You Should Investigate
Target Unusual Behavior Without Tuning
Easily white-list critical device network flow behavior
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialCritical devices would include point of sale systems, IoT devices, any device that uses a minimum amount of predictable functions/behaviors. Not for generic windows clients25
Cisco StealthWatch SystemNetwork Reconnaissance Using Dynamic NetFlow AnalysisMonitorDetectAnalyzeRespond
Understand your network normalGain real-time situational awareness of all traffic
Leverage Network Behavior Anomaly detection & analyticsDetect behaviors linked to APTs, insider threats, DDoS, and malware
Collect & Analyze holistic network audit trailsAchieve faster root cause analysis to conduct thorough forensic investigations
Accelerate network troubleshooting & threat mitigationRespond quickly to threats by taking action to quarantine through Cisco ISE
*Cisco acquired Lancope Dec 15
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialSCRIPT:The next product within the solution is Lancope StealthWatch Lancope is a Cisco partner and StealthWatch is on the Cisco Price List.StealthWatch enables context aware visibility, threat detection, incident response diagnostics and user monitoring It gives deeper visibility into the network and also accelerates the response of what to do with Netflow data, it analyzes the Netflow data and provides analytics on top of it StealthWatch can look at user behavior copying files, moving places in the network and determine whether these behaviors are suspicious It allows you to provide analytics and gain insight from Netwflow, you can gain visibility into user behavior, detect anomolies, collect and analyze network audit trails and leverage Cisco Identity Services Engine, or Cisco ISE, to take action based on this visibility.
26
Card Processor
Hacked Server
POS Terminals
ASA Firewall
Private WAN (trusted)
Credit Card Processor
ASA FirewallStoresData CenterUpdates from POS Server HTTPS Credit Card Processing HTTPSInternetISR G2 Routers
ISR G2 RoutersWireless AP
Wireless POSC3850 Unified AccessNetwork as a Sensor Host Lock Violation and Suspect Data Loss
Public Internet
Compromised Server
StealthWatch FlowCollectorStealthWatch Management Console Exfiltration of Credit Cards OR Commands from Attacker
Cisco ISECommand and Collect
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialThis is where you put them.
The lancope stuff.
Visibility doesnt require any presence in the store. You do need to have 3850 if you want to do NetFlow between devices in the store which is a recommendation. You also would only need a Flow Senor if you want to get granual Application Data, typically this can also be done at the datacenter.
Two features to help: Suspect Data Loss the Other is Host Lock Violation27
Best-of-Breed Cisco Advanced Malware ProtectionContinuous ProtectionReputation FilteringBehavioral Detection
Dynamic AnalysisMachine LearningFuzzy Finger-printingAdvanced AnalyticsOne-to-OneSignatureIndications of CompromiseDevice Flow Correlation
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential28These seven features break down into two types.
Reputation filteringBehavioral detection.
Reputation filtering is comprised of three key features. The first of which, is One-to-One Signatures
AMP EverywhereAMP Protection Across the Extended Network for an Integrated Threat Defense
AMPThreat IntelligenceCloud
Windows OS
Android Mobile
Virtual
MAC OS
CentOS, Red Hat Linux for servers and datacenters
AMP on Web and Email Security Appliances
AMP on Cisco ASA Firewall with Firepower ServicesAMP Private Cloud Virtual ApplianceAMP on Firepower NGIPS Appliance (AMP for Networks)
AMP on Cloud Web Security and Hosted Email
CWS/CTA
Threat GridMalware Analysis + Threat Intelligence EngineAMP on ISR with Firepower Services
EndpointsEndpointsNetwork Edge
AMP for EndpointsData Center
AMP for EndpointsRemote Endpoints
AMP for Endpoints can be launched from AnyConnect
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialWith AMP Everywhere, organizations can deploy a security architectures that shares information and provides an integrated threat defense, from network edge to data center to endpoints, across all attack vectors.29
Network AMP Indicators of CompromiseSometimes doesnt answer the question:Did the malware execute?
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
With AMP for Networks + AMP for EndpointsNetwork AMP + Endpoint AMP = Better Context
Detecting malware is great, but it could have been blocked on the client by AV or AMP for EndpointKnowing the malware executed makes prioritizing response much easier
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
A device with the AMP for Endpoints connector reacts to a retrospective event and immediately stops and quarantines the newly detected malware
Network AMP + Endpoint = Better Context
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialThis machine here, 10.5.11.8, we can see that it has the AMP for Endpoints connector installed. We know this because immediately after that retrospective event was raised the endpoint quarantined file. So by having the connector on the endpoint you have the ability to clear up and remediate and quarantine that infection on the end-point near in real time
32
When Malware Strikes, Have AnswersWhere did it come from?Who else is infected?What is it doing?
Device Trajectory
File Trajectory
File Analysis
Automated Remediation
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialAMP is context-aware
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialThe great thing about AMP is that its context aware. In this case, we are looking at the device trajectory. We see a list of applications (green are known-good, red known-bad and black unknown). The lines coming out of these are timelines, and the icons show when the file was moved, copied or executed. An example of context is the line coming out of 14 [PE] a file with unknown disposition that shows it dropping file 4 [PE], a known bad file. We can therefore infer that 14 is also bad. 34
Cisco AMP with ThreatGRID450+ behavioral indicators (and growing)Malware families, malicious behaviors, and moreDetailed description and actionable information
Prioritize threats with confidenceEnhance SOC analyst and IR knowledge and effectiveness (and security product)
Best-of-breed malware/file sandboxing
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialWe generate a Threat Score for every sample to assess how malicious it is. We do this by analyzing more than 450+ behavioral indicators defined by our own reverse-engineering and threat research team.. These indicators are based on the actual actions a file performs that we observe, that outside looking in approach i mentioned, when we run the file through our analysis engines.. The indicators are detailed descriptions of the actual behavior exhibited, including identifying what a particular sample was attempting to do. We look at these behaviors in a broader context, comparing your information against the behavior of millions of known samples to arrive at how that behavior was triggered by your specific sample. And we use a proprietary algorithm that considers the severity and confidence of the observed malware actions along with historical data and other parameters. The result is a threat score and behavioral analysis that gives security analysts the real-time insight they need to prioritize and respond to threats.
A key differentiator for Threat Grid is that we take this analysis and reporting and we perform it at scale.
35
PRODUCTS & TECHNOLOGIESUmbrellaEnforcementDNS based security service protects any device, anywhere
InvestigateIntelligenceDiscover and predict attacks before they happen
OpenDNS Adds to Ciscos Threat Prevention Portfolio
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialA Quick Refresher on DNS
RECURSIVE DNSLooks up & remembers the #s for each name
DOMAIN REGISTRAR Maps and records names to #s in phone books
AUTHORITATIVE DNSOwns and publishes the phone books
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential# = IP address37
Advantages of a DNS-based SolutionANY OPERATING SYSTEMWin, Mac, iOS, Android, Linux, ChromeOS, and even network devices and custom operating systems
FAST AND SCALABLEExtremely efficient query/response method
SIMPLE TO DEPLOYnetworks DHCP tells every connected device where to point DNS
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialThe elegance of DNS is that everything uses it already today. It doesnt matter who owns the device, how youve setup your network, or what OS or apps are running, they all work with DNS the same.38
INTERNETMALWAREBOTNETS/Command&ControlPHISHING
& HERE!
The Power of OpenDNS + Cisco
LANCOPEWSA (+ESA)
FIREPOWERAMPAMPAMPAMP
AnyConnectAMPAMPAMP
MERAKIAMPAMP
ASAHEREHEREHEREHEREHEREHQBranchBranchRoamingOff-netDNS LAYER
BENEFITSAlerts Reduced 2-10x; Improves your SIEMBlock malware before it hits the enterprise Contains malware C&C and Data ExfilNo added latencyProvision globally in under 30 minutes!
#CONFIDENTIALYour customers have already deployed Cisco appliances at offices and Cisco agents on devices.Of course, you can block malware on the network and the endpoint, but why wait until malware reaches the enterprise when you can block it out on the Internet.For that matter, why wait until anyone knows its malware, by learning about threats earlier in the attack lifecycle when the infrastructure is staged to launch the malware.That will cut customers # of alerts by 2 to 10 times.And for the malware that gets inside, contain its ability to exfiltrate data.
Block malware outside the enterprise, on the internet.
We Prevent and Contain threats very early in the attack lifecycle (kill chain), and do so by identifying / blocking the threat at the point at which its staged/launched/controlled (I.e. Very far away from the target [Network, Laptop, Application etc). we help stop attacks closer to the source of attack (so block the infection before the file/payload has been delivered and has had to traverse parts of the enterprise there are many benefits to this).
----ALTERNATIVE-----
Recall that DNS is ubiquitous for every network and endpoint footprint that exists in an organization. Even IoT devices rely on DNS.It doesnt require deploying a new appliance in the network. It doesnt require changing WCCP on a network you manage or deploying PAC files on an endpoint you own to redirect web traffic. And we dont care if web traffic is encrypted.Leveraging our wireless hardware partnerships, changing a single IP in DNS or DHCP servers, or referring to our network device setup guides make it so easy to point DNS to us.Were not exaggerating when we say it takes only 30 minutes to cover dozens of locations and thousands of devices.It is the fastest and easiest way to stop the vast majority of threats trying to infiltrate your systems and exfiltrate your data.----No endpoint security solution comes close to providing as much visibility into all Internet activity as Umbrella.And by combining the Internet-wide visibility that our Investigate product adds to Umbrella, customers can even identify targeted attacks.----But perhaps most valuable, is that because DNS precedes every IP connection, we cut the number of security alerts generated by the rest of a customers security stack in half or more.
39
OpenDNS working within the Architecture: better togetherSTART: App wants to connect to the InternetBENEFIT: Very-fast operation that accurately blocks a large percentage of threatsRESULT: Best-of-breed web threat protection that is efficient and easy to deploy
DNS request to resolve URL
1
DNS traffic redirects to OpenDNS
2
OpenDNS resolves request
3
App allowed to send web request
4
Web traffic redirected thru CWS
5
CWS performs web & file inspection
6
OpenDNSUmbrella DNS Traffic
CiscoCWS
InternetRemaining Web Traffic
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
40
A New Layer of Breach ProtectionRecursive DNS InspectionThreat PreventionDNS is common to almost all threatsProtects On & Off NetworkNot limited to devices forwarding traffic through on-premise appliancesPartner & Custom IntegrationsBlock based on malware analysis (Threatgrid, FireEye, etc.)Block by Domains for All Ports No added latencyIncredibly easy to POV/Deploy30min deploy timeUMBRELLAEnforcement
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialFree version41
OpenDNS Umbrella and ThreatGrid integrationSuspect Domain Protection
Dynamic AnalysisStatic AnalysisThreat Intelligence
AMP Threat Grid
Domain Based IOC DataFileSample
ASA /FP
MobileAMPFIREPOWER
FIREPOWER
Web Sec
ESA
FirewallApplianceWeb SecurityE-Mail SecuritySecurity AnalystAMP ThreatGrid Enabled Security SolutionsProtected Clients
Immediate Protection from domain based IOCsBenefitsAutomated integrationFull AMP Solution Coverage
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
Policy & Access
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
43
Protection against Advanced Persistent ThreatsNetwork Segmentation is critical
Verizon DBIR 2014: Recommended Controls
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
44
Cisco Secure AccessMaking segmentation easy and dynamic
ISETrustsecAnyConnect
Cloud WebSecurity
Web Security
Centralized Policy
Identity Authorization
L2/L3 Segmentation
Guest Access
MDM Integration
Posture& Profiling
Access ControlSegmentation
L2/L3 Segmentation
FirewallSimplification
Universal Security Client
MDM Integration
Posture& Profiling
AMP Enabler
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
45
Yellow RetailWAN
Data Centre
Yellow3rd-party supplierBlue RetailStore
Core Network (Transit)
Yellow RetailStore
TAG everything yellowAllow Yellow & Purple
DC Router: Allow yellow to yellow Allow blue and Yellow to purpleTag Yellow apps YellowTag Shared apps Purple
TAG everything BlueAllow Blue to PurpleDeny Blue to Blue except collaboration appsSharedAppsRetailApps
Simplify: Segmenting PCI traffic with SGT Security Domain Level classifications
Blue RetailWAN
M&ACompany XSGACLSGACLSGACL
Blue RetailWAN
SGACL
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
Meraki Security
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
47
Cisco Meraki: Cloud-managed Networks
Meraki MS Ethernet Switches
Meraki SMMobile Device Management
Meraki MR Wireless LAN
Meraki MX Security Appliances
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialMeraki MX Security Appliances6 models scaling from small branch to campus / datacenterComplete networking and security in a single applianceZero-touch site to site VPNWAN optimizationNG firewallContent filteringWAN link-bondingIntrusion Prevention
Feature highlights
Future support for:AMPIPFIX
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialSystems Manager Mobile Device ManagementDevice Management controls iOS, Android, Mac, and Windows devicesCloud-based - no on-site appliances or software, works with any vendors networkFree for up to 100 seatsCentralized app deploymentDevice securityRapid provisioningBackpack file sharingAsset management
Feature highlights
AMPIPFIX
Future support
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialSummary
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
51
Pervasive & Integrated Across CiscoIn Summary
Attack Continuum
Network-Integrated,Broad Sensor Base,Context sharing and Automation
Continuous Advanced Threat Protection, Cloud-Based Security Intelligence
Leading products working together as a systemBuilt for Scale, Consistent Control, ManagementVisibility-DrivenThreat-FocusedPlatform-Based
BEFOREDiscoverEnforce Harden
AFTERScopeContainRemediate
Detect Block DefendDURING
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
52
Only Cisco DeliversConsistent ControlReducedComplexityConsistent Policies Across the Network and Data CenterFits and Adapts to Changing Business Models Global Intelligence With the Right ContextDetects and Stops Advanced ThreatsAdvanced Threat Protection
UnmatchedVisibility
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco ConfidentialThe value Cisco brings customers is: Unmatched VisibilityYou will have access to the global intelligence you need with the right context to make informed decisions and take immediate action.Network as a sensorContextual awarenessUtilize global intelligence with big data analyticsOpen interfaces to visibility tools
Consistent ControlYou can consistently enforce policies across the entire network and have the control you need to accelerate threat detection and response.Unified policy orchestration, language and enforcementOpen interfaces to control platformsExtends from data center to cloud to end-point
Advanced Threat ProtectionYou will be able to detect, understand and protect against advanced malware/advanced persistent threats across the entire security continuum.Real-time threat analysisRetrospective threat analysis
Reduced ComplexityYou can adapt to the changing dynamics of your business environment quickly , at scale and securely.Integrated security services platformsUnified managementAutomationOpen ecosystem through APIsACI fabric integrationManaged Services53
# 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential