Atm details
-
Upload
pushpendra-singh -
Category
Documents
-
view
220 -
download
1
description
Transcript of Atm details

Chapter 10 ATM 1
Automatic Teller Machines

Chapter 10 ATM 2
Automatic Teller Machines “…one of the most influential
technological innovations of the 20th century”
Began in 1968, more than 500,000 today One of the first commercial use of crypto
(block ciphers), tamper resistant hardware, security protocols, etc.
The “killer app” for commercial crypto

Chapter 10 ATM 3
ATMs An interesting case study
o What was done correctlyo What was done incorrectly

Chapter 10 ATM 4
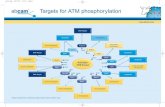
ATM Security Module Security module implemented in
tamper-resistant hardwareo IBM 4758 crypto processoro Security module is at banko All crypto computations done in
security module, such as PIN verification

Chapter 10 ATM 5
ATM Security Module IBM PIN generation
o Acct number N on magnetic stripeo PIN key K (in tamper-resistant hardware)o “Natural PIN” is F(E(N, K)), where encryption
E is DES, and F is a functiono PIN = natural PIN + offset (so customers
can choose their own PIN) Note: PIN verification relies on N and
secret K, and is done in security module

Chapter 10 ATM 6
IBM PIN Gen Example Account number: PIN key K: DES encrypt
E(N,K): Decimalize: Natural PIN: Offset: Customer PIN:
8807012345691715FEFEFEFEFEFEFEFEA2CE126C69AEC82D0224126269042823022465656789

Chapter 10 ATM 7
More ATM Security PIN encrypted with “terminal
master key” and sent to security module
‘Dual controls” --- terminal master key entered in 2 parts (2 people)
PIN “translation” (from one ATM network to another) done in security module

Chapter 10 ATM 8
Problems Early on, encryption done in software Not feasible for all pairs of banks to
share keys, so KDC used (VISA) Large number of trans, so corners cut
o “Optimization is the process of taking something that works and replacing it with something that doesn’t quite, but is cheaper”
Most ATMs use 56-bit DES

Chapter 10 ATM 9
What goes wrong ATM system designed to stop
sophisticated attacks In practice, the real issues are
o Processing errors --- e.g., computer crasheso Only 0.001% probability, but 5 billion ATM
trans Card theft from mail Fraud by bank staff
o Laptop inside ATM to record PIN’so Key for test system used for real system

Chapter 10 ATM 10
Unexpected Attacks Shoulder surfing to get PIN, copy acct
number from receipt One system --- telephone calling card,
ATM thought previous card inserted One system --- output 10 bills when 14-
digit test sequence entered One bank issued same PIN to everybody Fake ATM to collect PINs Steal the ATM (camera is inside ATM)

Chapter 10 ATM 11
ATMs Biggest mistake in design of ATM
system: “… worried to much about criminals being clever instead of worrying about customers and banks being stupid”

Chapter 10 ATM 12
ATM legal issues In US, banks carry risk of ATM
technologyo must refund most disputed transactiono costs average bank $15K/year in fraud
In much of Europe, customer bore costo Banks claimed ATMs infallibleo John Munden case
British policeman, found his acct $700 short Bank: no bugs in code since written in assembler Munden convicted and fired Overturned on appeal: bank would not release its
code

Chapter 10 ATM 13
ATM legal issues If Munden case had occurred in
California, “he would have won enormous punitive damages”
Lessonso Non-repudiation is critical --- camera in ATM
would have solved Munden case immediately
o In general, security system must be able to withstand examination by hostile experts